Abstract
In the protection of computer networks from attackers organizations often use firewalls. Though firewall software is often effective in controlling threats on a computer network lapses in its use can allow potentially harmful programs or individual’s access the system. For this reason it is important to perform periodical assessment to ensure the organizational information system is not breached. In this paper such an assessment will be performed using software and a policy.
Introduction
In the provision of security on a computer network or stand alone system there are no absolute guarantees (Windowsecurity.com 2002, p. 1 of 13).The issue of cyber security is an especially crucial organizational agenda as it involves protection of company data from attackers and unauthorized access (Suma 2010, p. 3213). Essentially a firewall is a software shield that is installed on a computer to provide protection of files and the system from external threats (Lucas, Singh & Cantrell 2006, p. 74). Taking a real world example a firewall resembles the steel reinforced passenger compartment in a vehicle that acts as a shield to the occupants in the event of an accident.
The firewall acts as a chokepoint between the internal system and the external network (Wright, Freedman & Liu 2008, p. 276). Physical access control is among the aspects that often go unnoticed during the design phase of networks and in some instances is the source of breaches on the network. There are a greater number of threats and entry points in a network than there were in the past. For example in a medium to large sized networks several entry points can exist due to a variety of factors such as presence of various Internet Service Providers (ISP’s), etc (Lucas, Singh & Cantrell 2006, p. 74).
In general given that a firewall is aimed at providing security to the system and user data it is important that the software is capable of preventing attacks. This report therefore seeks to identify a set on optimal tests that can be used to ascertain the effectiveness of a computer firewall.
Background of the Problem
As stated in the introduction the objective of this project is to develop an effective approach to assessing the security of a firewall. As mentioned earlier one major source of potential vulnerability is the existing infrastructure upon which the network is constructed. The infrastructure can be accessed using either an audit or an assessment. The assessment is performed to identify potential issues whereas the audit which is done later to gauge performance in accordance with policies and procedures (Lucas, Singh & Cantrell 2006, p. 308).
To provide adequate security to the system it is essential to have a proper understanding of the components of the network system (Weinschenk 2003, p. 1 of 2). These components include network perimeter security, internal network security, intrusion prevention and monitoring, server and host configuration, security from malicious code, incident response capability, security policy and procedure, employee training and physical security (Lucas, Singh & Cantrell 2006, p. 309).
It has been established that even some of the widely used security software on the market is vulnerable to threats. An example of such an incident was reported in 2006 when Symantec antivirus software was found to be highly vulnerable to worm like threats (Lucas, Singh & Cantrell 2006, p. 323). It should be noted that this software is in use on 200 million computers world wide. This suggests that even with popular commercial software applications some degree of risk may still exist.
Literature Review
It has been reported in research that the practice of simply purchasing and installing a firewall could easily result in an inappropriate decision by an organization as far as network security is concerned (Brand 2007, p. 21). This because it has been suggested that intrusion testing requires consideration of risks that are not necessarily software based (Sofroniou 2004, p. 26). Assessing security risks the business is exposed to requires that a through examination of legislation in relation to business rules and the internal IT requirements (Weinschenk 2003, p. 1 of 2).
Based on this it has been suggested that a test plan needs to be formulated that will help ensure the firewall complies with organizational policy. The results of such a plan can help identify different points in the system where firewall mechanisms can be useful. These mechanisms are usually either software oriented or appliance type devices. Based on the organizational needs it is possible to identify which among packet filtering firewalls, application and circuit gateways, MAC layer firewalls and gateways (Brand 2007, p. 25).
In addition to the above point it is important to consider the role of various threats to the network that may increase vulnerability. The introduction and widespread use of mobile technology in the world today has seen emergence of substantial opportunities through increases in production, availability and convenience (Milligan & Hutcheson 2008, p. 1). At the same time this mobile technology and the widespread use has resulted in an increase in criminal behavior and fraudulent dealings.
The mobile networks and devices have resulted in an increase in risky trends such as rapid spreading of viruses, loss of sensitive data, increased risk of exposure of data via spam, etc (Milligan & Hutcheson 2008, p. 1). With the high risk that comes with the use of these devices it becomes important to consider techniques to reduce the potential risks such devices can pose to the network.
Some threats to networks are caused by allowing programs to run and gather data on users and their activities also known as spyware. The term spyware is used to refer to the software used to transmit and gather information about end users (Clutterback 2006, p. 461). These programs operate as illicit data sensors and gather information on the user behavior which is transmitted back to a remote source. Owing to this discrete method of collecting data these programs can be very useful and also potentially very harmful. It is crucial that the firewall in place detect and prevent their entry onto a network (Clutterback 2006, p. 473). Spyware is harmful as it can be categorized under reconnaissance threats or attacks. The information gathered can be used to initiate an attack on the network and as such their operation should be avoided permanently.
In addition to the above mentioned threats it has been established that a large number of security breaches result from activities of staff within organizations. In a study on the role of insiders in cyber crime it was noted that in 2003, the banking and finance sector recorded a 43% increase in cyber crime and at least 29% of this was due to insider activity (Cappelli & Keeney 2004, p. 3). It has been suggested that solution to the threats from insiders it may be necessary to have two tiered security architecture (Speed & Ellis 2003, p. 108). A host based system to prevent threats from external sources and a network based system to monitor insider activity (Kozushko 2003, p. 16).
An alternative would be the use of new technology known as honey pot’s to lure insiders. Such programs can emulate even regular programs and allow the user to interact with them and capture data about potential threats (Spitzner 2003, p. 2). The above data indicates that in addition to external threat security software it is essential to have a mechanism to monitor internal threats to avert potential problems.
Ethical Issues
The process of completing an assessment of firewall security within an organization is often plagued by complex legal and ethical issues. It has been reported that though research on cyber security may be among the few means available to improve security on the internet its practice has been hindered by various legal statutes (Burstein 2008, p. 1 of 11).
For example, for successful research in cyber security it is essential to collect data from the network. However, legal provisions preventing the use of wiretaps, non content interception and prying into stored content from ISP repositories (Burstein 2008, p. 3 of 11). These legal challenges have made the process of research in cyber security cumbersome and have limited the scope of research work on networks.
This situation normally arises due to the lack of policy on how computer technology should be utilized (Dittrich, Bailey & Dietrich 2009, p. 2). However, some of the major successes in cyber security have been made by breaches of such legal prohibitions. Some of the studies have led to retrieval of huge data banks with information collected through the use of malware that was instrumental in fraud and impersonation attacks (Dittrich, Bailey & Dietrich 2009, p. 2). Based on this data it would appear that completion of a project such as this one will require some solution to the legal and ethical questions posed. It is suggested that the participating staff sign agreements that allow any intrusion of privacy that may be required for successful assessment of security software.
Recommendations
In the past firewalls were deployed on the perimeter of a network to ward off potential threats. However, with improvements in technology such an approach is no longer adequate as some threats have evolved allowing their operation within the application layer of a network (Scarfone and Hoffman 2009, p. 7). Because of this it is often a practice during the design of networks to include firewall functionality at locations other than the perimeter.
In light of this the degree of security has been enhanced but there is still a need to provide a mechanism to test the security of the firewall periodically to ensure its efficiency. One approach of improving the firewall is through reviewing the firewall policy (Wright, Freedman & Liu 2008, p. 277). These policies dictate how the firewall should handle network traffic for specific addresses on the network in addition to address ranges, content type, protocols and applications based on the organizational information security policy (Scarfone and Hoffman 2009, p. 28). This policy should be updated frequently as the possibility of various classes of threats and vulnerabilities arise. This planning in the initial stages of deploying a firewall is especially crucial with regards to expected performance.
Among the means that have been identified to test the firewall policy is the use of penetrations testing. This process involves making attempts to break the rules laid down in the firewall policy (Wilheim 2009, p.259). The results generated after completion of the procedure can be compared against expected results to provide insight into whether the firewall is operating within the required parameters (Scarfone & Hoffman 2009, p. 42). If the firewall is capable of generating network traffic and monitoring the traffic as required it may be assumed that the firewall is operating appropriately.
Among the common anomalies that the examination of the policy will be on the look out for include shadowing, correlation and generalization anomalies. Either of these anomalies in the rules could result in penetration that is untraceable (Brand 2007, p. 22). Based on the weakness of a penetration test this approach is best used when in conjunction with an audit (Bouwer & Jager 1998, p. 28). In developing an appropriate audit procedure the auditor is required to give special consideration to the organizational internal control objectives. These objectives allow the auditor to develop specific queries to include in the audit trail. This is because an audit is not intended to ascertain the efficiency of the software but the achievement of the internal objectives (Bouwer & Jager 1998, p. 28).
To understand the firewall the auditor can browse the user manuals and parameter printouts. The technical capability should not deter the auditor from addressing issues based on the internal security policy. This is because even with good firewall software it is possible to have configured the system wrongly thus leaving the network exposed to threats. In addition to this an auditor is expected to inspect the system logs to confirm whether the users are keeping to the rules (Weinschenk 2003, p. 1 of 2). In some cases poor knowledge of IT systems causes uses to increase the level of threats within a computer network.
These are notes to assist completion of the practical part of your project
Course Technology. 2010. Penetration Testing: Network and Perimeter Testing. Cengage Learning: Mason, OH.
The book is available on Google books Start at Page 3-12.
Selecting Software for the Test
When making a selection on the solution to use for this experiment there are several of available options to select from such as software, personal firewalls and hardware based firewall solutions (Danesh, Lau & Mehrasa 2002, p. 134). Each option comes with specific demerits that the project will consider prior to making an appropriate selection. For example, the cost factor in off the shelf firewall hardware products. Though the cost has dropped to almost $100 in recent years this is still out of reach for the purpose of this project. In addition to that they offer limited configuration options. However, these are the easiest to implement as they just require to be plugged in between the computer and the network (Danesh, Lau & Mehrasa 2002, p. 134).
Another option is the use standalone hardware firewalls. This is a computer dedicated to act as a firewall. This machine can protect the entire network and not just a single machine. They are appropriate as the software will allow the configuration on any options required. Another advantage is if an operating system like Linux is in use the user can download and use the open source programs for free. The only disadvantage is the user must knowledgeable on scripts that are used to configure the firewall (Danesh, Lau & Mehrasa 2002, p. 135).
The last option is the simplest and is considered most suitable for the purpose of the report. This option requires installation of the software which in many cases configures itself automatically (Danesh, Lau & Mehrasa 2002, p. 134). In addition to this it is essential to have an optimal security policy available to determine whether the configuration provided meets the business needs. This is essential as it can assist in identifying potential loopholes.
The Procedure
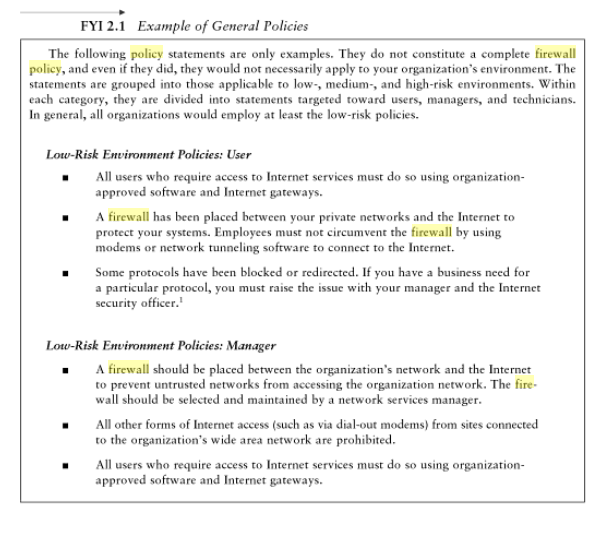
Once you have enabled your firewall you need to define a set of rules that you intend for the firewall to adhere to such as the sample below. The firewall will then be tested based on the rules. Some tests may require you connect your pc on a network and attempt access using features such as remote access. Others may require you attempt to access the shared documents without permission. The rules form the basis of whether your security is appropriate or otherwise. Remember to follow the guidelines in the recommendations above. If your rules contain redundant rules that may be a problem.
References
Bouwer, AM & Jager, H, 1998, ‘Internet Firewall Environment: An Audit Perspective’, South African Journal of Accountability and Auditing Research, vol. 1, pp. 21-33.
Brand, M, 2007, ‘A Comprehensive Firewall Testing Methodology’, Proceedings of the 5th Australian Information Security Management Conference, pp. 21-32.
Burstein, AJ 2008, Conducting Cyber security Research legally and ethically. Web.
Cappelli, D & Keeney, M, 2004, ‘Insider Threat: Real Data on Real Problem’, USSS/CERT Insider Threat Study, pp. 1-29.
Clutterback, PJ, 2006, ‘A Software Audit Framework for Spyware Risk Mitigation’, Proceedings of the 1st International Conference on Design Science Research in Information Systems and Technology, pp. 461-474.
Danesh, A, Lau, F & Mehrassa, A 2002, Safe and Secure: Secure your home network and protect your privacy online, Sam’s Publishing, USA.
Dittrich, D, Bailey, MD & Dietrich, S 2009, ‘Towards community standards for ethical behavior in computer security research’, Technical Report 2009-01, Stevens Institute of Technology, Hoboken, NJ, USA, pp. 1-18.
Kozushko, H, 2003, ‘Intrusion Detection: Host Based and Network Based Intrusion Detection Systems’, Independent Study, pp. 1-23.
Lucas, M, Singh, A & Cantrell, C, 2006, Firewall Policies and VPN Configurations, Syngress Publishing Inc, Rockland, MA.
Milligan, PM & Hutcheson, D, 2008, ‘Business Risks and Security Assessment for Mobile Devices’, Information Systems Control Journal, vol. 1, pp. 1-6.
Scarfone, K & Hoffman, P, 2009, ‘Guidelines on Firewalls and Firewall Policy’, National Institute of Standards and Technology Special Publication, 800-41, pp. 1-48.
Sofroniou, A 2004, Change Management in IT, Andreas Sofroniou, Marlborough Road, UK.
Speed, T & Ellis, J 2003, Internet Security: A Jumpstart for Systems Administrators and IT Managers, Elsevier Science, Burlington, MA.
Spitzner, L, 2003,’Honeypots: Catching the Insider Threat’, Computer Security Applications Conference, pp. 1-10.
Suma, SSC, 2010, ‘Evaluation of Vulnerability Assessment in System from Hackers in Cyber security’, International Journal of Engineering Science and Technology, vol. 2(7), pp. 3213-3217.
Weinschenk, C 2003, How to make sure a firewall does its job. Web.
Wilheim, T 2009, Professional Penetration Testing: Creating and Operating a Formal Hacking Lab, Syngress Publishing Inc, Burlington, MA.
Windowsecurity. 2002, Comprehensive Computer Network Security Assessment. Web.
Wright, C, Freedman, B & Liu, D 2008, The IT Regulatory and Compliance Handbook, Syngress Publishing Inc, Burlington, MA.
Vacca, J. R., Ellis, S., & Ellis, S. R 2005, Firewalls: Jumpstart for network and system administrators, Elsevier Digital Press, London.