Introduction
Businesses worldwide operate under conditions that are subject to change, depending on the political situation, economic, and natural conditions. Business houses are constantly under the threat of disasters, such as earthquakes, terrorist attacks, fires, riots, power outages, and stock market crashes. Due to such risks, the intellectual assets, such as classified documents, source codes, and physical assets, such as infrastructure and hardware, run the risk of compromise.
In such a situation, a plan must be in place to allow the business to recover its intellectual and physical assets and continue the business operations, at the earliest. It is also essential to assure clients and business partners, who have invested time and resources, that in case of a disaster, their investments could be recovered in an acceptable time frame. To handle such situations, it is important to have a plan that is implemented to counter the effects of disasters. Having a Disaster Recovery Plan (DRP) and Business Continuity Plan (BCP) becomes important when a business expands to an overseas market. This paper discusses the important elements of a DRP and BCP for a company with global operations.
Scenario 1- Natural Disaster – Hurricane and Earthquake
A disaster is defined as an event that causes interruption of business operations for an uncertain period of time. In this case, an IT company called ABC Ltd. has been considered.
About the Company ABC Ltd.
The company has several Strategic Business Units (SBUs) or profit centers that are spread all over the world. The company provides services to various overseas clients through support units, such as offshore development cells (ODCs), onsite personnel, and sales offices (Botha, 2004). Figure 1 shows the organizational structure of a company, ABC Ltd.
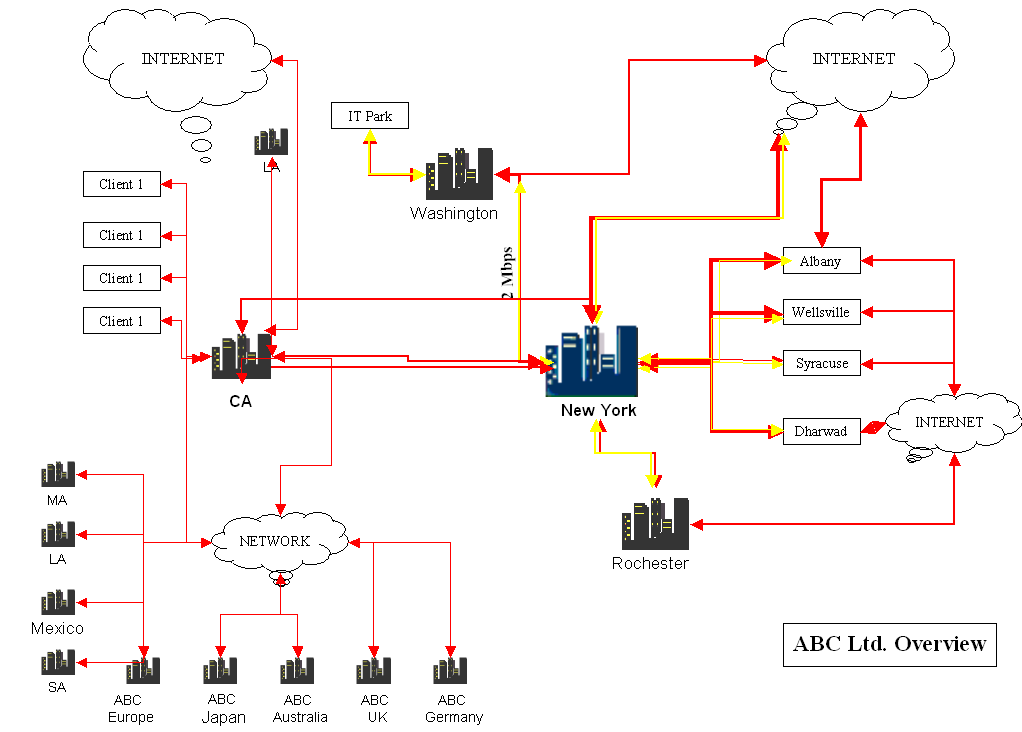
The figure shows the interconnectivity between different units of the company. The central hub of the company is in New York. It is a B2B central server and serves as the communication gateway and database for all business-related protocols, processes, and storage areas networks, and others. The central hub also serves as a Gateway for different clients that the company provides services for and these are identified as Client 1, Client 2, etc. The Network is connected to a number of strategic business units in continents such as Europe, Japan, Australia, the UK, Germany, etc. These centers are identified as ABC Europe, ANC Japan, etc. The clients are serviced through a network with different strategic business units (Edwards, 2006).
BCP Scenario
In the scenario, we will project that a major Hurricane has broken out along with an earthquake in the regions in which ABC Ltd. is situated. Natural disasters have taken out all the fiber optic cables and other infrastructure. The intellectual property of the company, its database containing records of transactions, software applications, customer financial records, etc, are stored in the IT systems. If the IT systems are not recovered in time, then all business would cease, people would not be able to use credit cards, personal identification authentication systems would be lost and there would be utter chaos (Edwards, 2006).
Please refer to A1. Table of Disaster Levels. For the sake of the paper, it is assumed that a Level 4 disaster has stuck the centers.
BCP Solution
The Business Continuity Management Program (BCP) within a company is responsible for performing the business impact analysis, a process of classifying information systems resources baseline on criticality, and development and maintenance of a BCP. Tasks that need to be covered are included in the BXP document. The BCP should also maintain the BCP document up-to-date. This responsibility includes periodic reviews of the document – both scheduled (time-driven) and unscheduled (Event-driven). BCP defines a Recovery Time Objective (RTO) that specifies a time frame for recovering critical business processes.
The BCP meets the needs of critical business processes in the event of disruption extending beyond the time frame. Recovery capability for each Strategic Business Unit (SBU) – including all Projects being executed under the SBU – shared service, location, and Offshore Development Center are defined. In the event of any moderate/minor disaster, the recovery capability should ensure that the business processes work seamlessly without affecting any other dependent critical business processes. E.g. If the main power grid is disrupted, there must be standby facilities like generators to ensure that power is available. (Edwards, 2006)
Objective and Scope of BCP
BCP plan is intended to provide a framework within which companies can take decisions promptly during a business disruption. The objectives of this plan are (Broder, 2002):
- To identify major business risks.
- To proactively minimize the risks to an acceptable level by taking appropriate preventive and/or alternative measures.
- To effectively manage the consequences of business interruption caused by any event through contingency plans.
- To effectively manage the process of returning to normal operations in a planned and efficient manner.
- The scope of the corporate business continuity management plan document must include plans for restoring:
- SBUs and all the Projects being executed by the SBUs
- Shared services
- Information Systems at all locations of the company
The Proposed Solution
The following network is proposed for the BCP solution.
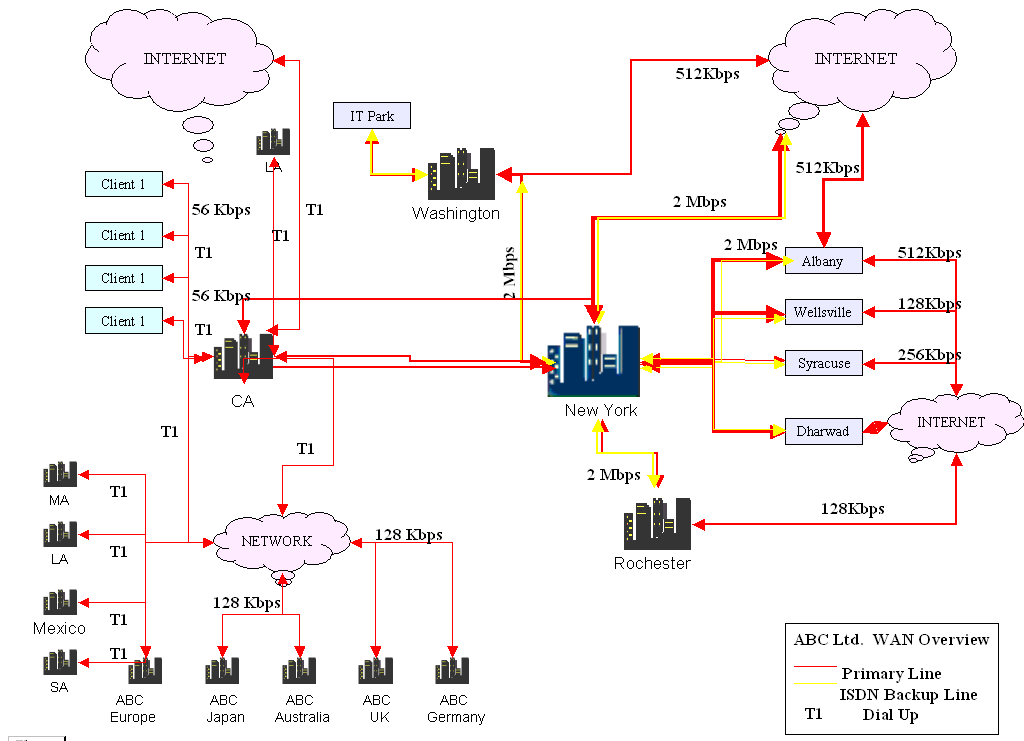
A redundant connectivity network has been proposed between different nodes in the network. According to the plan, a number of mirror cache sites have been proposed and these would take updates from different servers and while transferring the information in the network, they would also store data in storage area networks. A 2 Mbps primary line with dedicated fiber optic cabling is proposed for the connection between the central server and the mirror caches.
In addition, there would be an ISDN backup line that would connect the systems and this would be operated at 512 kbps. Further connections would have a T1 Dial-up connection at 28-156 kbps. The update between the serves would be done at 12.00 hours GMT and at 24.00 hrs GMT. In this manner, even if disasters would take out one whole continent or even the central server, there is sufficient redundancy to start the network at reduced speeds. The data would already be stored in storage data networks and it can be physically retrieved and restored.
Scenario 2 – Secure Lines/ VPN network compromised
In this case, the same company is covered in Section 1.1. has been considered. In this scenario, we will assume that the Site to site VPN connectivity from one of the centers ABC Ltd. New York has been compromised by fire. The fire has engulfed the IT systems in the center and it would be cut off from the rest of the network. (Crothers, 2003). The following figure shows the existing Site to Site VPN Connectivity to ABC Ltd. NY.
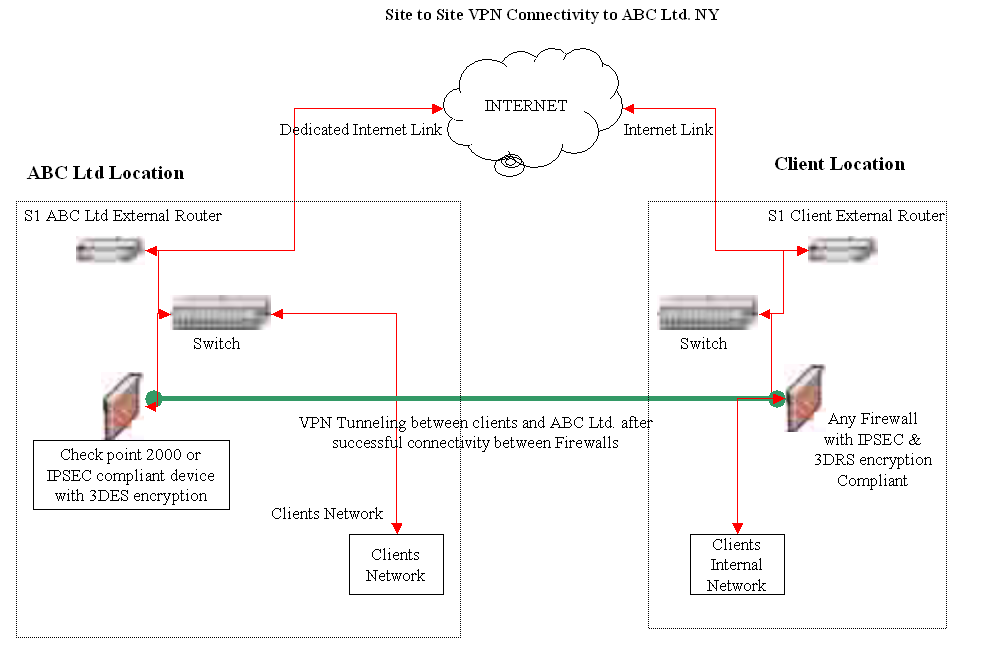
Steps to Implement a BCP
Developing the BCP involves the following phases (Broder, 2002))-
- Risk Assessment
- Business Impact Analysis
- Strategy Selection
- Business Continuity Plan Documentation
- Testing
- Maintenance
Risk Assessment
In this phase, one needs to identify the risks to the business processes, assess existing mitigation measures, and recommend mitigation measures wherever necessary. The activities in this phase enable you to determine the extent of the potential threat and the risk associated with the IT infrastructure and IT applications of your company (Broder, 2002).
The risk assessment phase involves/includes the following:
Inventory: identifies/Documents the various business processes, hardware, software, communication links, documents, and associated people using standard templates developed by the risk assessment team.
Threat analysis: Identifies various threats to the business processes. It also identifies the probability of a threat being executed and the potential impact a threat will have on the business in the event of its execution. This is done using a standard template developed by the risk assessment team. The risk assessment team identifies a list of over 35 possible threats to any asset. Based on this list each location is assessed for the probability of each threat being executed and the potential impact on the business processes (Fitzgerald, 1995).
A threat is any circumstance or event that can potentially cause harm to the business.
Vulnerability analysis: Scans critical servers and hardware devices owned by the company periodically for identifying vulnerabilities and taking corrective actions based on the audit reports. These reports should be studied for their completeness and adequacy. In addition, while arriving at the probability of a threat being executed, the existing vulnerabilities of each location must be analyzed. (Fitzgerald, 1995).
Business Risk Assessment: Includes a detailed assessment of the practices followed by the business units with respect to risk management. The risk assessment team should conduct detailed interviews using standard questionnaires with senior representatives of the business units to understand the risk management practices of the individual business units. (Moore, 1995).
Single Point of Failure Analysis (SPOF): identifies the most vulnerable business process. A SPOF is the weakest link in a business process. Each SBU must identify the SPOFat their locations. (Moore, 1995).
Risk Matrix: Analyzes the identified risk, derived by qualitative analysis of various threats and vulnerabilities to business processes through threats and vulnerabilities analysis, business risk assessment, and SPOF analysis. The risk areas are classified as Very High-Risk Areas, High-Risk Areas, Medium Risk Areas, and Low-Risk Areas. You can also recommend mitigation measures for each risk area identified (Moore, 1995).
BCP Solution
The following solution has been proposed to get the operations started once the fire has been doused and the network is ready for recovery.
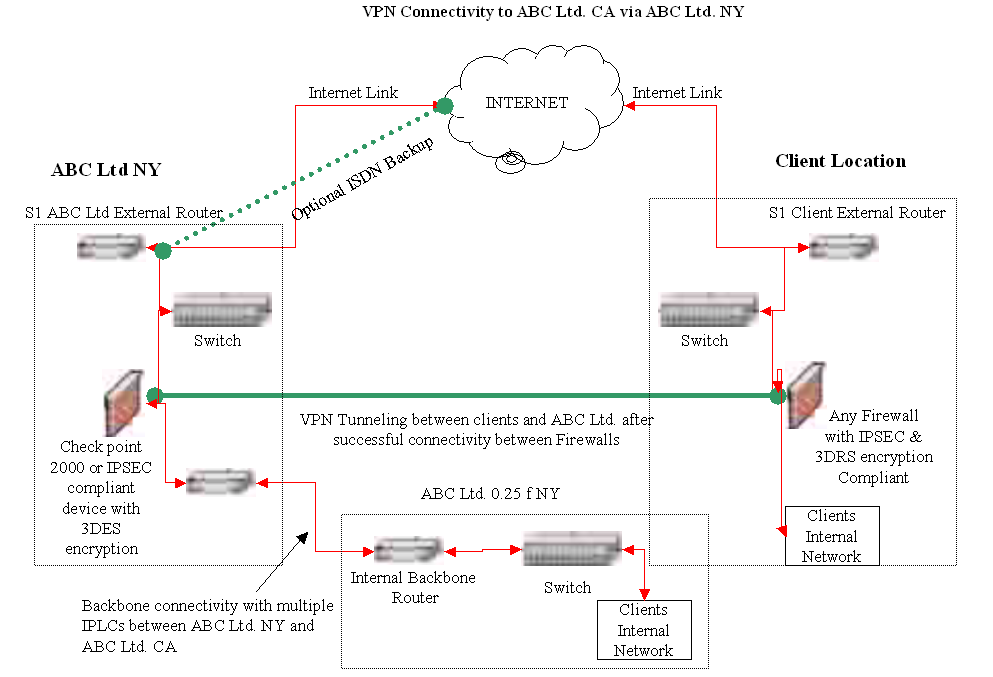
The network diagram as shown above is designed to provide redundancy between ABC Ltd. NY and the client location. An optional OSDN backup line is proposed along with firewalls. An internal Backbone router has been proposed with a switch that would be connected to the Client Internal network. A fire fall has been proposed of either Checkpoint 2000 or IPSEC complaint with 3DES encryption. The system data is stored in storage area networks and allows for quick restoration in the event of a fire. The fiber optic networking would be designed for Class IV fires and suitably hardened (Lavell, 2004).
Scenario 3- Hacking and Virus Exploit
A network security administrator has seen in the system log, a few attempts by unauthorized users who have tried to log in to the system. The system administrator has terminated the login attempt manually a few times, but there are fears that the hackers will ultimately hack into the servers and compromise the system. The plan is to build a honey pot to trap the intruder and harden the system by using firewalls and proxy servers. This will help in not only trapping the hackers but also allow the network to be recovered in case the hackers damage the network before the intrusion is detected. The BCP will also stop data from flowing out to the hackers (Botha, 2004).
BCP Solution
An intrusion Detection System (IDS) will be installed to detect unauthorized access attempts by hackers. The system will serve as an alarm system and the main intention of IDS is to provide a warning that illegal activity is happening or has happened some time back (Crothers, 2003).
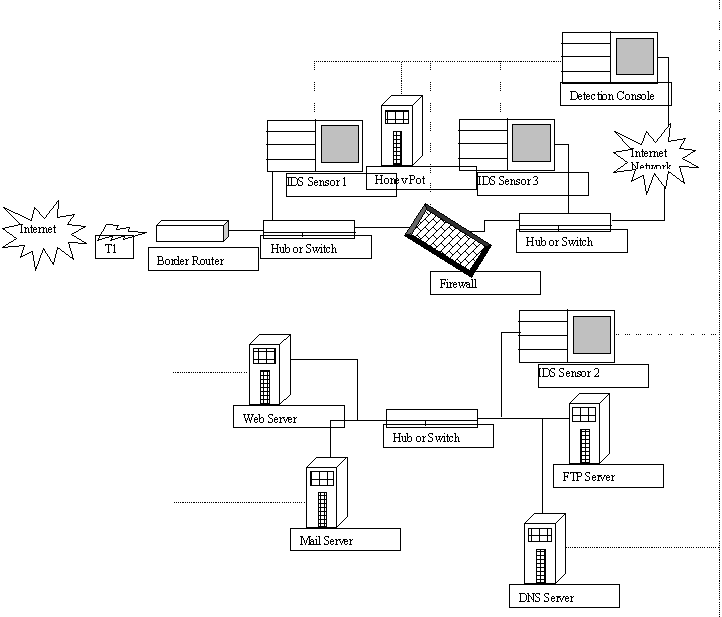
A firewall is used to protect the internal network and create a demilitarized zone and this will isolate the corporate servers from being accessible to the public. There will be three intrusion detection sensors that will monitor the network traffic for signs of attack or malicious activity. The solid lines in the figure are the actual network connections. The dotted lines represent the secure communications that are used to pass detection information from the network and host-based intrusion detection sensors to the master detection console. (Crothers, 2003).
Conclusion
The paper has discussed the process of BCP implementation and has examined three scenarios in a large IT company where BCP has been implemented. In Scenario 1, BCP has been provided for a natural disaster, in scenario 2, it has been performed for a large fire breakout while in scenario 3, the BCP has been proposed to recover from a hacking and virus exploit.
References
Botha Jacques. Rossouw Von Solms. 2004. A cyclic approach to business continuity planning. Journal of Information Management & Computer Security. Volume 12. Issue 4. pp 38-51.
Broder James F. 2002. Risk Analysis and the Security Survey, 2nd edition. Broder. Boston, MA: Elsevier Science. ISBN: 0750670894.
Crothers Tim, 2003. Implementing Intrusion Detection Systems. Wiley Publishing Inc. ISBN 8126503688.
Edwards Frances L. 2006. Businesses Prepare Their Employees for Disaster Recovery. Journal of Public Manager. Volume. 35, Issue. 4; pp. 7-13.
Fitzgerald Kevin J. 1995. Establishing an effective continuity strategy. Journal of Information Management & Computer Security. Volume 3. Issue 3. pp: 105- 138.
Lavell Joan L. 2004. Business continuity plans: An overview. Journal of Investment Compliance. Volume 5. Issue: 2. pp: 75-86.
Mick Savage. 2002. Business continuity planning. Journal of Work Study. Volume 51. Issue 5. pp. 95-123.
Moore Pat. 1995. Critical elements of a disaster recovery and business/service continuity plan. Journal of Facilities. Volume 13. Issue 9/10. pp: 195-236.
Appendix
A1. Table of Disaster Levels
The following table provides a classification of different levels of disaster. (Lavell, 2004)