Introduction
Mobile apps are increasingly being introduced following the recent improvements in the processing speed of smartphones and mobile devices. Similarly, the technological advancements have seen the mobile industry undergo tremendous changes from mobile operators to the integration of mobile apps such as government mobile apps, trends, and channels. The government mobile apps exist in two forms: enterprise-focused apps and citizen-oriented apps (Sharma et al., 2018). The former target the employees of public organizations and is limited to the firewalls established by organizations, while the latter are for external use.
The efforts to improve the government mobile apps started back in 2012 during the Obama administration. The aim was to add mobile apps to the federal government, a decision informed by the need to simplify the process of seeking government services. The plan was guided by the following four principles: establish information centered government targeting open data, create a shared platform in all agencies, adopt a customer-centric approach of data presentation and integrate the necessary measures to improve privacy and security. Below are some examples of government mobile apps recognized as being innovative for delivering information to people (USA.GOV, 2020).
Smart Traveler: The app was established by the state Department to help those planning to go on different trips abroad. The app was designed to give alerts and critical information on countries as well as how to contact different U.S. embassies.
FoodKeeper: The app was introduced by the U.S. Department of Agriculture with the aim of helping citizens find the necessary resources for food safety. Similarly, the app allows citizens to interact with food safety specialists by asking questions such as how long food can stay in the fridge before it becomes not suitable for consumption.
FEMA App: The app remains to be the best option when it comes to preparing for and responding to an emergency. It ensures the users receive timely emergency alerts and information during and after an emergency. Moreover, the app provides weather alerts, disaster resources, safety notifications, and tips on how to prepare for emergencies. Most importantly, FEMA has contact information for those looking for assistance, such as finding local shelters and recovery centers.
IRS2GO: The app was introduced by the Internal Revenue Services. It exists to help users track the status of their refund, make payments, as well as look for tax preparation assistance. IRS2GO comes with a variety of features which makes it easy to use.
myStudentAid: This app is best suited for those looking forward to joining college. It also allows students who qualify for aid or loans from the federal government to fill out the FAFSA application.
Most of these apps work well on modern mobile OSs, which features different security mechanisms. Once an app such as IRS2GO is installed, it only accesses files indicated in the sandbox directions. The errors made by developers in designing these apps create a gap in protection which gets exploited by attackers.
Federal Government’s Requirements and Recommendations
Mobile apps, just as laptops and desktops, require secure design and architecture applications. However, the only slight difference is that the process of creating reliable design and architecture for mobile devices is more challenging and needs additional security. Such devices are small in size and rely on a wireless connection, making them easy to steal. Once stolen, the culprit can easily access the most sensitive data. In addition to this, smartphones require more dynamic network connectivity, especially during calls and when connected to Wi-Fi. Therefore, the federal government’s first line of defense for mobile apps is to improve security. For instance, the use of transit encryption is needed whenever the app transmits username, passwords, and API keys. This type of encryption protects against snooping and data interception since mobile devices rely on open Wi-Fi access points.
Developers often deploy TLS inform of HTTPS in order to protect the users. Many users are advised to utilize industry-standard methods, instead of adopting less secure strategies as highlighted by Razaghpanah et al. (2017). Another method that has proven effective in safeguarding the apps is zero-trust security; it defends devices sufficiently, especially for government agencies. Zero trust security is increasingly becoming popular among users because of its basic principle of assuming that nothing on a network is safe. In general, the process of evaluating mobile apps security should be based on organization-specific requirements that the app must meet before approval.
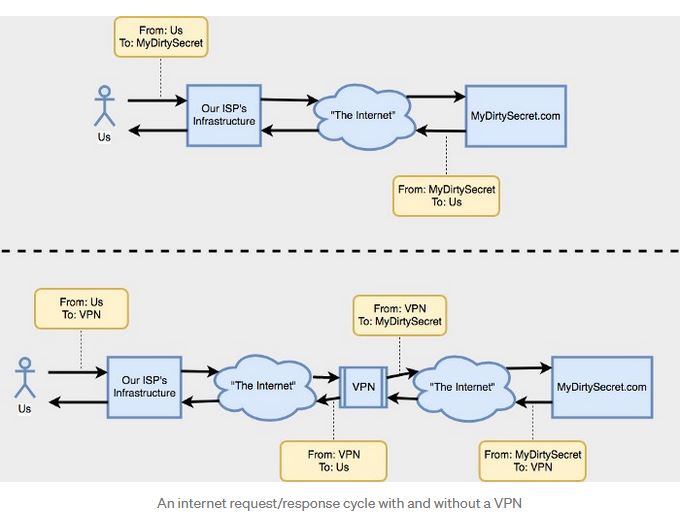
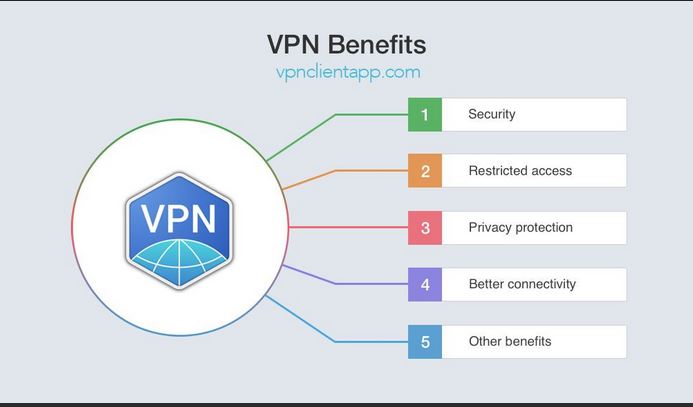
The first recommended mobile app security system is Virtual Private Network (VPN). Grechishnikov et al. (2019) described VPN as a security system that allows the mobile device to create a secure connection with other networks. As seen in the figure below, the use of VPN helps the user encrypt online activities such as “MyDirtySecret” and, in the process, ensuring one remains anonymous. It is important to note that VPN is not only limited to public networking system but also works with partnered networks. A good example is where two companies decide to communicate via VPN technology without any public network connection. Figure 2 further shows some of the benefits of using Virtual Private Network.
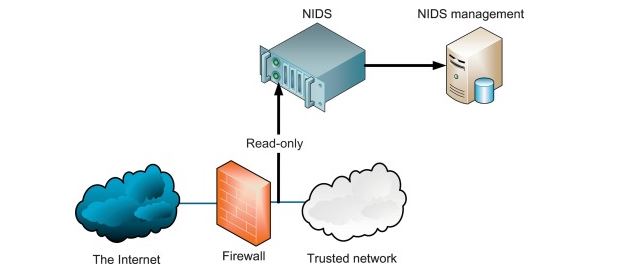
The second security system for consideration in this paper is Intrusion Detection System (IDS) which is used to detect threats in the incoming network traffic. An IDS helps with the identification of threats by constantly monitoring networking pattern of traffic flow. The main advantage of IDS lies in its ability to detect malicious activities and, at the same time, alert either the IT experts or other threat controlling systems. This happens mainly in mobile-to-mobile connections where the intrusion detection system identifies malicious activities in the networking connections.
Industry’s Recommendations for Security Architectures and Risk Reduction
People around the globe use mobile phones for communication, work, and private businesses. This means that such devices require applications that can store sensitive and valuable information in their databases. Therefore, keeping this information secure remains a top priority. Most of these devices contain critical information in the form of pictures, address, contact, and text messages. Any attempt to access sensitive data might cause a lot of damage to the user. The consequences of mobile device attacks are more disastrous than those of computers and laptops.
Mobile app developers should strive to familiarize themselves with the most reliable and productive practices in order to develop long-lasting solutions. Similarly, they need to have a clear understanding of how mobile apps will be used and on what platforms they will be operating. For instance, they need to be aware that the malicious program can target both the client and the devices. The industry experts must also ensure mobile devices are secure with good encryptions.
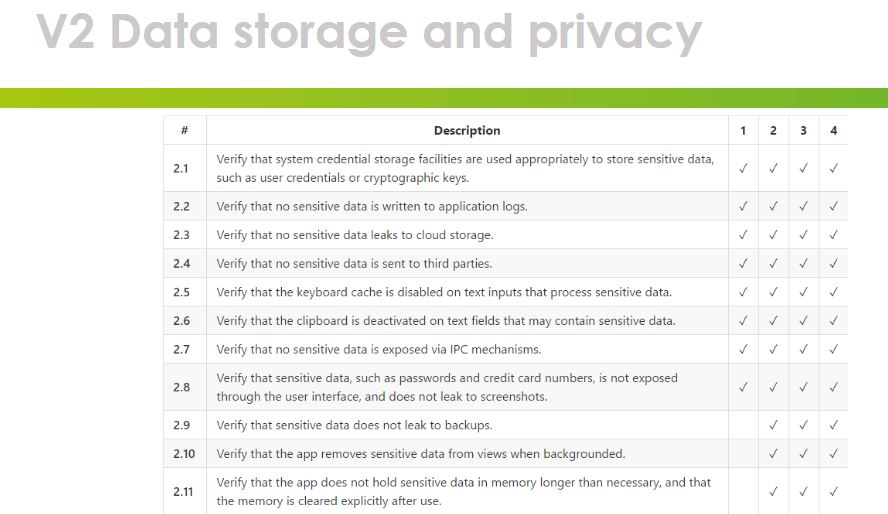
This discussion recommends the use of the OWASP Mobile Application Security Verification Standard (MASVS). Mobile software architects and developers can use it to develop secure mobile applications and security testers. MASVS comes with four strict security verification levels and a set of reverse engineering requirements (Figure 3 and 4). Security verification level 1 requires a mobile application to comply with basic needs related to code quality, dealing with sensitive data and interaction (Matos, 2016). A testing process must be introduced to help verify the security controls. Level 2 features advanced security controls, which require mobile app developers to adopt a threat model and prioritize security during the design phase. Before deployment, the controls must be verified using white-box testing to ensure they are effective and reliable. This level is recommended for applications that handle sensitive data.
Security verification level 3 has mechanisms that offer in-depth defense and resiliency. According to Matos (2016), the level adds “another layer of protection for apps that process sensitive data” (p. 8). By implementing it, users stand a better chance of preventing unnecessary tampering of the app. Lastly, an application with level 4 verification security tends to have strong software protection; it also has strong resiliency against attacks and reverses engineering attempts.
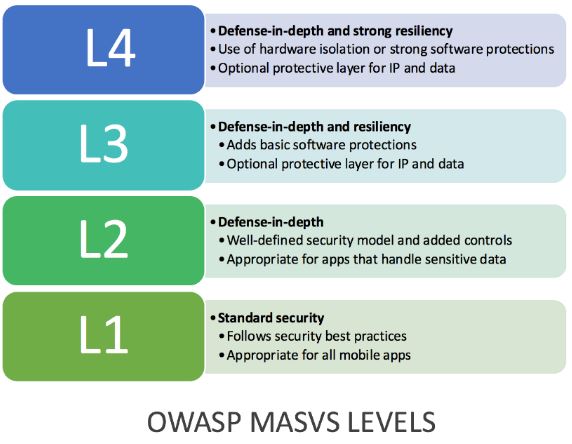

Each verification requirement indicated in figure 5 above comes with various descriptions that guide the implementation of security controls at different security verification levels. For instance, at Architecture, design & threat modeling (V1), the developers must comply with the security measures put in place. At level 1, all the key components of the app must be identified with a clear reason as to why they should be included in the app. At level 2 to 4, the architecture should be well-defined and ensure the code follows the right structure. In general, MASVS is the best option because it gives a clear guidance on what to look for in a mobile application.
Best Practice Recommendations for Building Security
The recent improvements in the processing power of smartphones have increased the number of mobile applications in the market. Most of these apps are one-click away; can be accessed on Google Play Store, Windows Store, and Apple App Store. With the steady rise of the mobile app economy, companies and global enterprises are considering the option of using this technology to improve performance and productivity. In fact, many businesses and individuals who never used apps before are embracing the new norm. However, there is a critical issue that both businesses and individuals must consider if the apps are secure. Below are some of the best practice recommendations for building secure mobile apps that provide government information and services.
Source Code Encryption
Developers of government mobile apps should ensure they include the tools to detect and address security vulnerabilities during the initial stage. Similarly, they must ensure the apps are robust enough to avoid unnecessary interference and reverse-engineering attacks; such threats damage an organization’s reputation (Kachot, 2020). In other words, source code encryption will ensure the app is unreadable since most of the code is on the client’s side.
Penetration Tests
It is imperative for developers to run a thorough QA and security check by subjecting the app against multiple generated security scenarios before deployment. A good example is pen testing which prevents security risks associated with mobile apps (Kachot, 2020). The aim of a penetration test is to help detect loopholes in the system which, if left unchecked, might develop into potential threats to mobile features and data.
Secure the Data-in-transit
People rely on government apps for information and different services. This means that the information transmitted is quite sensitive and must be protected against data theft and privacy leaks (Kachot, 2020). One way of safeguarding such information is by using a virtual private network, which employs strict security measures in order to protect user data.
File-Level and Database Encryption
Mobile apps are designed to store confidential data in the local file system and in a sandbox. The problem with data in the sandbox is that it might not be effectively encrypted; thus, creating a gap for potential vulnerabilities (Kachot, 2020). Therefore, the best way to secure sandbox data is by using SQLite Database Encryption Modules when implementing mobile app data encryption. Alternatively, the developers should consider using file-level encryption across all platforms.
High-Level Authentication
The high number of security breaches being witnessed today is caused by a lack of high-level authentication. According to Kachot (2020), developers should “design the apps in such a way that it only accepts strong alphanumeric passwords” (p. 3). In addition to this, users should be encouraged to change their passwords to avoid unnecessary breaches occasionally. For more sensitive data, it is advisable to use biometric authentication (fingerprints or retina scan) to strengthen security.
Minimize Storage of Sensitive Data
Developers should adopt the option of storing data in the device local memory to protect sensitive data from the users. However, users are advised against storing sensitive data in order to minimize security risk; it is necessary to use encrypted data containers if a person must store data. In addition to this, developers should encourage users to use auto-delete features which automatically remove data to minimize the log. Overall, app security issues should be a top priority for designers to reduce the damage linked to malicious activities.
Conclusion
The recent advancements in technology within the mobile industry have led to a high number of mobile applications being introduced to the market. Government apps, which exist in two forms (enterprise-focused and citizen-oriented apps), are increasingly being targeted by cyber attackers. Some examples of government mobile apps include: FEMA, FoodKeeper, and Smart Traveler. These apps require secure design and architecture because they work on small devices (mobile phones), which are easy to steal. Therefore, the federal government’s first line of protection is by improving security. One way of achieving this is through the use of transit encryption which protects against snooping and data interception.
The discussion also offered several recommendations for mobile app security architecture which included Virtual Private Network (VPN) and Intrusion Detection System. The former, as discussed above, allows the mobile device to create a secure network connection with other networks. The paper recommended the use of MASVS for security architectures and risk reduction. MASVS has four strict security verification levels and a set of reverse engineering requirements that ensures the right security measures are adopted. For instance, security verification level 3 comes with mechanisms that offer in-depth defense and resiliency. Lastly, the discussion also highlighted several best practices for building security. They included source code encryption, penetration tests, and file-level and database encryption.
References
Bettilyon, T. (2018).Do VPNs actually protect your privacy?Medium. Web.
Conrad, E., Misenar, S., & Feldman, J. (2016).Eleventh hour CISSP®: Study guide. Syngress. Web.
Grechishnikov, E. V., Dobryshin, M. M., Kochedykov, S. S., & Novoselcev, V. I. (2019). Algorithmic model of functioning of the system to detect and counter cyber attacks on virtual private network. Journal of Physics: Conference Series, 1203(1), 12-64.
Kachot, D. (2020). Top 8 best practices to develop secure mobile apps. Clarion Technologies. Web.
Matos, J. (2016). Introduction to OWASP mobile application security verification standard (MASVS). Web.
Razaghpanah, A., Niaki, A. A., Vallina-Rodriguez, N., Sundaresan, S., Amann, J., & Gill, P. (2017). Studying TLS usage in Android apps. In Proceedings of the 13th International Conference on Emerging Networking Experiments and Technologies (pp. 350-362).
USA.GOV. (2020). Mobile apps directory: USA.gov. Web.