The integration of new technologies into a school setting can be seen as an inevitable process. In that regard, the educational institutions that start to integrate technologies, not only to gain a competitive advantage in the education market, they also allow increasing the efficiency of the learning process, and reduce costs.
Computer networks and electronic resources are among the necessary technological assets that attract new students, and allow schools to reduce paper costs. Other advantages can be seen through the possibility to integrate multimedia resources into the curriculum. Qatar Independence School has set on the path of integrating Information Technology (IT) into the school context.
Having already fully equipped computer labs, the school intends to expand and integrate the labs into a unified system connected to the internet, with a digital attendance record, and touch screen test system. In addition to computers in the labs in the proposed system, wireless access will be provided through Wi-Fi hotspot zones. With security aspects being the main focus of such a system, the present project documents the process of designing and implementing security control through fingerprint facilities in the computer network in Qatar Independence Schools.
Requirements and Technologies
Primary Research
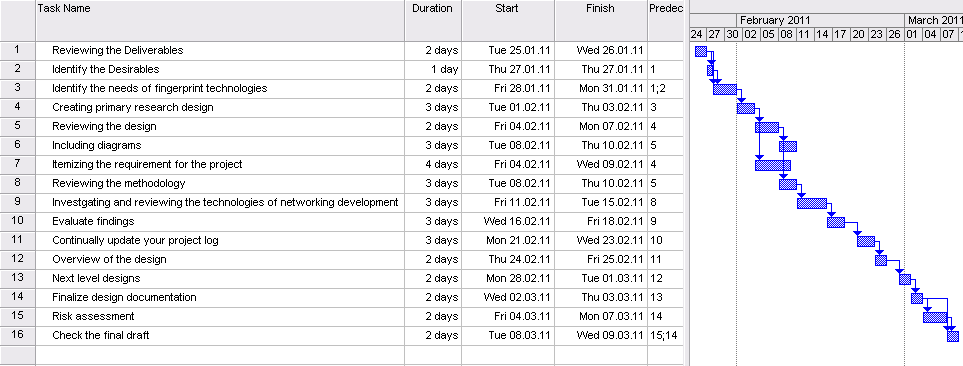
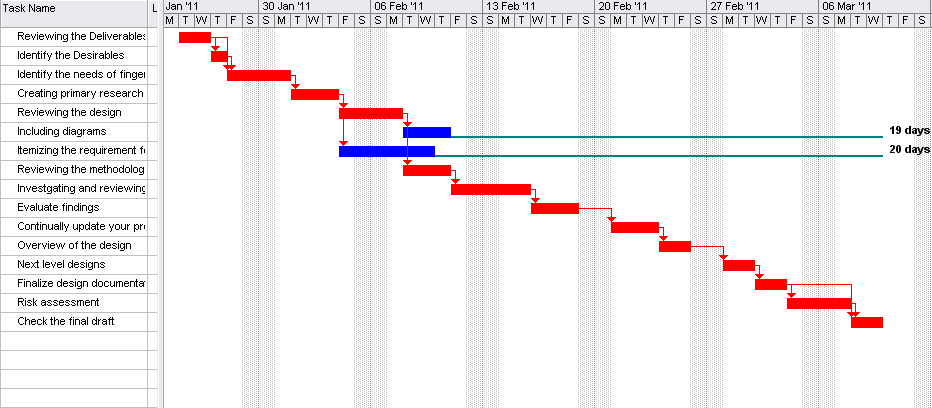
In order to identify the requirements for the project, a qualitative research was conducted, in which a series of unstructured interviews with various IT analysts and representatives of computer security field were held in order to identify feasible requirements for the proposed system. The basic outline of the interviews can be seen below.
- Describe the implementation of a fingerprint facility in a school.
- The parts of the system.
- The main precautions.
- How is it justified?
- Factors for
- Factors against
- Other means of security.
- Touch screen tests.
- Typical scenario.
- Other usages of the devices.
Accordingly, eight interviews were conducted during the span of 10 days, during qualitative data were collected from the main participants of the study. The result of the interviews mainly outlined several common themes and patterns in terms of the design of the proposed security system. These themes and patterns can be seen through the following:
- Most respondent s agreed that third party separate solutions will be a cheaper and more feasible acquisition.
- The authentication procedure using fingerprints should be differentiated through different purposes and different terminals.
- Passwords and other knowledge-based security measures are not sufficient means to manage security in applications.
One of the main arguments supporting fingerprint authentication was through evident through flexibility and speed. One area of arguments justifying the use of a fingerprint identification system is being fast in input. Many experts cited the example a comparison between the time required for a password input and a fingerprint scan.
Considering the fact that Qatar Independence School has 320 students and 45 instructors, the time delays for inputs can pose a real issue in terms of efficiency and flexibility. Categorizing the essential part of the system all respondents s acknowledged that fingerprint authentication facility can be seen as one of the most significant parts of the project. Answering the question on the main part of the system, John Summers, 36, independent IT analyst stated,
The main part in fingerprint identification is the scanner and the database with the templates. Everything else is a matter of providing an infrastructure to communicate between those two parts. Fingerprint authentication is as simple as that. Nevertheless, there were other parts as well which presence is vital for the system to function properly. Those parts included a database server, scalable and capable to manage many queries efficiently, a server that can serve as the core of the whole system, and wired and wireless infrastructure that will connect all the parts of the system together.
In that regard, one essential theme that emerged during the interviews is the compatibility between the different parts of the system. An example of the latter can be seen through installing a fingerprint authentication scanner which is not capable of integrating with Microsoft’s Active Directory. Accordingly, the compatibility between the SQL server, the server, and the fingerprint hardware should be also paid attention to.
Finally, the need to implement other means of security in addition to the fingerprint authentication can be dictated by the fact of using a network in general and a wireless network in particular. Answering the question on using other means of security, Rolanda Bayley, 29, an system administrator, stated,
Fingerprint authentication are necessary to protect access to desktop and laptops, but how about the wireless network. Using powerful access points to cover the school territory, users from outside might infiltrate the network. In this case, it is not about using free internet. It’s about protecting the databases of the school.
In terms of touch screen tests, the main analogy was drawn between the required devices and the products of Apple’s iPad. Nevertheless, all respondents agreed that the price of the device is a major factor for such purpose. The main direction suggestion was using low cost touch screen tablets, which are Wi-Fi certified and capable to integrate into the computer network of the school. Other usages identified by respondents included the following aspects:
- E-reading device for textbooks, electronic articles and lecture notes.
- Playing multimedia materials.
- Time management tool.
- A tool for taking notes.
Secondary Research
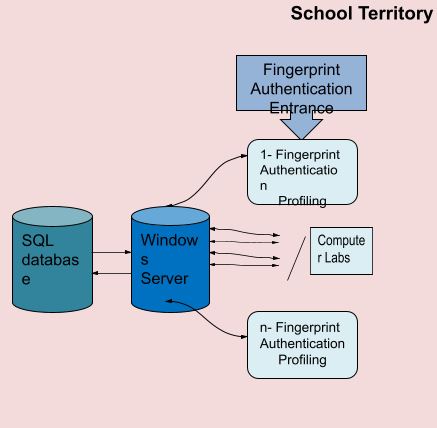
A review of literature on the technologies to be used was conducted for the purposes of the present project. In that regard, the main parts of the system can be divided between authentication terminals, a database, a server, and wired and wireless infrastructure. The computer lab desktop terminals will not be discussed within the scope of this project limiting the description to the processes and the interactions of the security system. The overall design of the system can be seen through Figure 1. In that regard, the technologies used include the following aspects.
Fingerprint identification
The technology behind fingerprint identification can be seen through two simple processes scanning and matching. The fact that human identifiers such as fingerprints have distinctive anatomical characteristics enables biometric recognition, which will provide better security and higher efficiency. In that regard, such identifiers cannot be “misplaced, forged, or shared, [and] they are considered more reliable for person recognition than traditional token- (e.g., keys or ID cards) or knowledge- (e.g., password or PIN) based methods” (Maltoni, 2009).
Two modes exist for the operation of fingerprint authentication facilities. The first mode is the enrolment mode, i.e. the mode in which the fingerprint is acquired, and then its feature extracted and stored in a template in the database (Seshadri and Avulapati, 2010). The second mode is the authentication mode, i.e., the mode in which the acquired fingerprint will be matched with existing templates, and according to which scores, certain security policies will be applied (Seshadri and Avulapati, 2010).
It should be noted that the first phase is a one-time phase that will be performed for students and staff in Qatar Independence School, while the second phase is a continuous day-to-day security procedure. The connection of the fingerprint authentication system to the server can be seen through Figure 2.
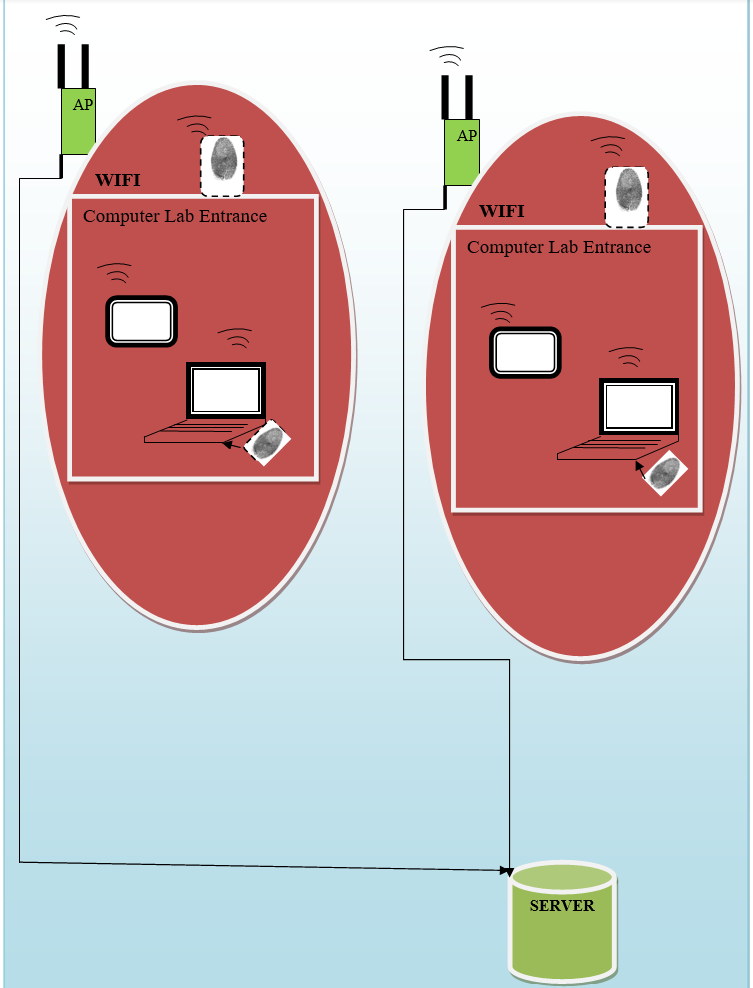
In order to mitigate the risks of potential failure of the fingerprint authentication system, the computers will be capable of authorisation using passwords. Such possibility will be saved for system administrators for the case of emergencies and computer check ups. It should be mentioned that the labs in this context are reserved for desktop PCs, which will be connected wirelessly to the network.
Although being stationary, as opposed to touch screen tablets, the utilization of wireless connection will allow expanding the number of computer labs without substantial investments in the wired infrastructure. Accordingly, fingerprint authentication devices will be attached to the desktops in computer labs (see Figure 2).

Database
The database contains profiles of each student along with staff personnel with a fingerprint identification template matched to it. Microsoft SQL Server 2008 will be used to create, store and manage data contained in the profiles. Such data will be stored in databases which are scalable and can be even shared between several organizations (Harbaugh, 2010).
In that regard, considering the fact that the Qatar Independence Schools are considering increasing the number of students enrolled, SQL Server can serve as platform capable of handling massive databases, integrating all the data and managing all user queries. Accordingly, combining SQL Server and Windows Server will enable the school to create a centralized data centre, easily upgradable into a more powerful structure if necessary (Microsoft, 2010).
Server
The core of the system can be seen through Microsoft Server 2003. One of the main tasks of the server can be seen through providing network access for connected terminals (Boswell, 2003). An essential element of the implemented technology is the usage of security policies. The security policy can be defined as a collection of rules and instructions that control computer systems and their components, network cohesion, secret and confidential information, etc. In the context of the present project, security policies can be seen as elements of a template to which fingerprints can be attached.
Using user and group policies the administration of the school can limit the rights of these users and groups to perform certain actions (TechNet, 2005). The assignment of permissions can be implemented through either groups or roles in Microsoft Server 2003. The logical roles that can be assigned might include teachers, IT staff, students, administration, etc. The roles can be seen as a collection of tasks supported by an application (MSDN, 2008a). The stages of forming such policy can be seen through either assigning users directly to roles, or collecting users in groups and then assign them to roles (MSDN, 2008a).
The information of group policies can be stored in group policy containers (GPC) in the corresponding template, which can be seen as an area in Active Directory (AD). Utilizing authentication software compatible with AD will allow managing policies and groups, loading profiles and accounts, linking passwords, and others, to be performed in seamless manner within a single system.
Wi-Fi
Wi-Fi technology enables the connection of different devices wirelessly over the air. In that regard, such technology will make the organization of the network structure in the school easier, and at the same time will eliminate the necessity for the devices to be connected to the network in specific places only (Figure 2). The principle of work can be seen through putting several access points throughout the school territory, which will enable all Wi-Fi certified devices to connect to the internet. The certification aspect will ensure reliable connections and security over the air for the devices connected to the network (Wi-Fi Alliance, 2006).
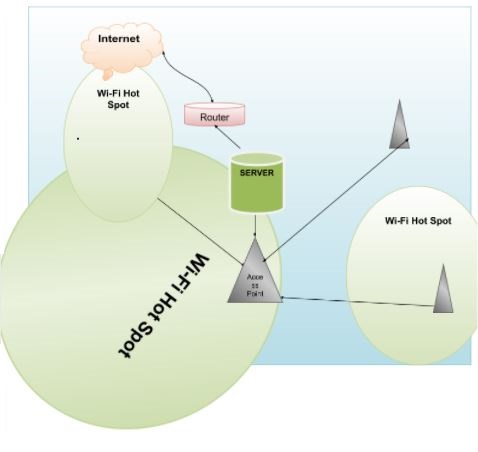
The distinction between finger print authentication and standard methods of security over Wi-Fi can be seen in that the standard methods, e.g. Wi-Fi Protected Access (WPA) security (Wi-Fi Alliance, 2004), can be seen through different application. WPA can be used along with MAC filtering to control access of unauthorised devices, while fingerprint authorisation will link any processes, activities, achievement , etc, of the student to his/her unique profile, controlled by fingerprints.
Touch Screen Tablets
The definition of tablet PCs can be seen as “a portable computer equipped with a touch screen and special pen that allows users to ‘handwrite’ on the screen” (Xiang et al., 2009). Several other variations might exist, including internet tablets, such as Apple’s iPad. The main differences can be seen in the system of control and their usage as handwriting devices. Nevertheless, the main principles of such device are the same, a touch screen, light weight, and connectivity.
The benefits of touch screen tablets might conform to the findings of the primary research, where their use include such aspects as recording presentation slides with notes and audio recording, assessment through receiving, marking, and returning assignments, and using as an interactive teaching aid (Xiang et al., 2009). A study conducted to review the technological aspects of using wireless tablet PCs revealed that students are “overwhelmingly in favour of introducing Tablet PCs to lecture rooms and distance education” (Xiang et al., 2009).
The alternatives to Apple’s iPad, which are either available or ready to be available, include options such as Knowledge Now (KNO), an education oriented low-cost tablet PC, and Marvell prototype (Tsotsis, 2010, Charbax, 2010). Other options can be seen through various Android-based tablet PCs, available from different vendors (Light in the Box, 2010). The connection of the tablet PCs within the system can be seen through Figure 2.
Minimum Requirements
The main software requirements for the project are mainly composed of Microsoft products family. The following family of software products were selected for the system:
For the server:
- Microsoft Server 2003 Standard Edition
For Laptops and Desktop:
- Microsoft Windows XP
For the database server
- Microsoft SL Server 2008
For the Tablet PCs there are no software requirements of the tablets themselves as they come pre-installed with a proprietary operating system (OS). Such system might be based on Android OS, Apple iOS, or Windows Mobile, or other tablets that might be used. Additionally, the choice of the tablet might require installation of software to sync the tablets with Desktops. In that regard, such aspect also depends on the choice of the tablets. Android-based tablets might be recommended in that regard.
The main hardware requirements for the project can be seen through the following aspect:
- Finger print scanners for desktop use (installed on PCs).
- Fingerprint scanner for attendance records (installed on school and/or class entrances).
- Wi-Fi Access points – devices for converting wireless and wired communication through transmitting radio signals (Mitchell, 2010).
- Touch screen tablet PCs.
Accordingly, the hardware requirements might include the minimum specifications for the operation of the Microsoft and SQL servers. According to the official requirements of Microsoft SQL Server 2008, the minimum hardware requirements include:
- Minimum: 1.0 GHz Pentium III-compatible processor or faster.
- Minimum: 512 MB for SQL Server Express with Tools, and SQL Server Express with Advanced Services (MSDN, 2008b).
Microsoft Server 2003 requires the following hardware specifications:
- Processor with minimum speed of 550 megahertz (MHz)
- 256 megabytes (MB) of RAM (Microsoft, 2005).
Additionally, each of the desktops in computer labs should be equipped with a certified wireless adapter that will connect the computer to the network through wireless access points.
Risk Assessment
Risks in IT projects cannot be excluded. In that regard, many of the risks associated with the current projects are foreseeable, and accordingly, can be identified and planned. The risks can be categorised into several types, which include risks external to project management and the organization, governmental regulatory changes, industry specific procedures, change-driven factors, emergencies, and others (Murch, 2001). The main risks associated with the current project can be seen through the following table:
Table 1: Risk Assessment.
Quality Management
The quality in the context of project management can be defined as “the degree to which a set of inherent characteristics fulfil requirements” (Phillips, 2010). In that regard, it can be stated that the quality implied in the context of project management is about the quality of the deliverables and the processes. For each of the deliverables in the projects there should be metrics used to measure the good of the service or the product. The value of the deliverables in this project can be seen through such factors as the value of the implementation, i.e. cost-benefit analysis, value of the service, the value of the experience, the value of the longevity, and the value of the reliability (Phillips, 2010).
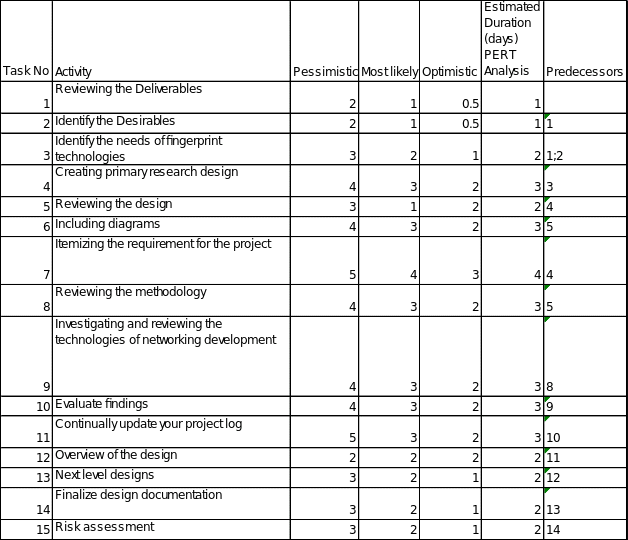
Experiments that will test the functionality and the service delivery of the project should be planned. Such experiments might include such aspects as authentication, breaking through the network, the stability of connection, and testing variations in the policies and rules for different users and groups. The schedules for testing should be organised in order to monitor the quality should correspond to each stage of implementation on a prototype of the system. The tasks to be tested and their schedules can be seen through the following table.
Table 2: Testing Schedule.
References
BOSWELL, W. 2003. Inside Windows Server 2003, Boston, Addison-Wesley.
CHARBAX. 2010. Marvell announces $99 Moby Tablet to Revolutionize Education. Web.
HARBAUGH, L. G. 2010. Review: Microsoft SQL Server 2008 R2. Web.
LIGHT IN THE BOX. 2010. Android Tablet PC. Web.
MALTONI, D. 2009. Handbook of fingerprint recognition, New York, Springer.
MICROSOFT. 2005. Windows Server 2003, Enterprise Edition: System requirements. Web.
MICROSOFT. 2010. SQL Server 2008 – Your Data, Any Place Any Time. Web.
MITCHELL, B. 2010. Wireless Access Point. Web.
MSDN. 2008a. Dynamic Groups in Windows Server 2003 Authorization Manager. Web.
MSDN. 2008b. Hardware and Software Requirements for Installing SQL Server 2008. Web.
MURCH, R. 2001. Project management : best practices for IT professionals, Upper Saddle River, NJ, Prentice Hall.
PHILLIPS, J. 2010. IT project management : on track from start to finish. New York: McGraw-Hill.
SESHADRI, R. & AVULAPATI, Y. K. 2010. High Performance Fingerprint Identification System. International Journal of Computer Science and Information Security. Web.
TECHNET. 2005. Local Users and Groups overview. Web.
TSOTSIS, A. 2010. Kno To Build A Single Screen, Education-Focused Tablet. Web.
WI-FI ALLIANCE. 2004. WPA Deployment Guidelines for Public Access Wi-Fi® Networks. Web.
WI-FI ALLIANCE. 2006. Wi-Fi CERTIFIED. Web.
XIANG, W., GOH, S., PATHER, S., MAXWELL, A., WANG, H. & KU, H. 2009. USE OF WIRELESS TABLET PCS AS AN EFFECTIVE LEARNING AND TEACHING ENHANCEMENT TOOL. Web.