Introduction
Management of knowledge and information has become one of the biggest concerns for organizations in the current competitive business environment. For a long time, most of the large organizations depended on mainframe and minicomputers to store their data. However, this has changed with the progressing technologies in the communication sector. According to Dimon (67), most of the organizations currently use numerous personal computers at workstation to disseminate information as needed within their set-ups. However, several challenges have been witnessed due to the use of numerous computers as opposed to a single mainframe computer. Different experts and scholars have given their views on the importance of having systems that are able to meet the objectives they are developed as a way of helping the firm remain competitive.
In the United Arab Emirates, many companies have been struggling to find the best approach to managing information in their systems. It is on this basis that many firms have found it necessary to develop Enterprise Social Networking systems to enable their appropriate management of information. Several firms have come up with the systems to solve this problem. They have accepted Enterprise system management concept as a solution to the management of knowledge and information in an organization. IBM was one of the firms that first developed enterprise systems management software to help firms that were moving from the use of mainframe computers to numerous personal computers. Microsoft also came up with software that would help organizations professionally manage their information using enterprise systems management concept. This white paper focuses on how to implement Private Enterprise Social Networking for the Union National Bank in Abu Dhabi branches.
Problem statement
The Union National Bank is one of the leading financial groups in the United Arab Emirates. Since its inception in 1982, this bank has experienced a massive growth to become one of the biggest financial institutions in this region. This bank has been keen to provide its customers with their needs in a special way. According to Dimon (48), this bank has had massive market growth due to its policies that are sensitive to offering value to its customers. However, this brilliant performance of the firm has always included challenges when it comes to managing information. This firm has a group of very dedicated employees who always strive to meet the needs of their customers. However, their duties are at times interfered with due to the internal information-sharing system. It would fail at times because of the server problems or inability of one computer to relay the needed information to other computers. When this occurs, it forces the employees to stop attending to the customers until the problem is fixed. This situation does not only waste time for the customers, but also employees who are forced to sit and wait for the systems to be up and running once again. Such issues are always brought up by the lack of proper information management systems within the organization.
According to the online interview the researcher had with the top management of this firm, it is apparent that the Union National Bank has been negatively affected in the past by system failures (Borge 78). The manager clearly stated that the time lost when the system went down always resulted in massive losses for the firm. For a long time, the management has not realized the benefits of enterprise social networking systems as one of the ways it can use to enhance internal communication sharing. This research would, therefore, try to find out how this problem can be permanently eliminated from this firm through the implementation of a private enterprise social networking system.
Enterprise Social Network Trends
There has been a rising need to share information amongst people working within a firm or people with common business interests or activities. According to Dimon (67), enterprise social network has been used to create a forum where people with common interests and working in different locations can share pieces of information they consider vital. However, there is an emerging trend where firms use enterprise social networks to allow the free flow of information among the workforce. Large organizations may have different departments, which have different functions. Each department would have professionals in specific fields. These officers may need to share information to ensure the smooth running of the firm. Enterprise social network offers an opportunity for them to share the necessary knowledge for the common interest of the company. The diagram below shows the trend that has resulted in the current smart enterprise social network.
It is clear from the diagram that the need for better information management tools and systems has seen enterprise social networks evolve over the years to become what it is now.
Social Network Platforms
Dimon (62) stipulates that enterprise social networks could never have been a reality if it were not because of the social network platforms available today. The emerging trends in this field have seen several social network platforms currently being used. Tibbr is one such platform that is common in the business community. which is always considered secure, flexible, powerful, and intuitive. Members are always assured that there will be no intrusion into their shared communication.
Jive platform is another one that has grown very popular in the recent past, especially among the business community. It creates a platform where business partners, employees, and customers can connect, communicate, and collaborate to achieve a common interest. The platform is very popular with marketing teams when reaching out to their customers.
Yammer, which was launched in 2008, and later sold to the Microsoft Company in 2012, is another very popular social networking platform. It was originally meant to help in internal communication within firms, especially by departments. However, the scope of this network has broadened, as the market needs to rise. The following diagram shows the components of an enterprise social network.

These components work together to enhance information and knowledge sharing within an organization.
Understanding the product design
Fee (76) says that technocrats with knowledge of the system may best understand the design of enterprise social network platforms such as Yammer. The management of the Union National Bank needs to comprehend the product design before it can commit to implement the system as a way of enhancing knowledge and information management within the firm. According to Fee (89), understanding product design is always essential when dealing with new systems within a company. The management should have a clear plan on how this project should be implemented and understand some of the basic principles of enterprise systems management.
Basic Principle of Enterprise Social Networking (Yammer)
The choice of Yammer is made due to the efficiency of the platform since Microsoft acquired it. It is important to observe the basic principle of enterprise social networking within an organization. The focus of this enterprise social networking should be viewed to be able to determine its real worth. This system seeks to find a way in which departments and individuals within an organization can share information and knowledge easily, collaborate while undertaking activities, and find fast solutions to problems that may arise in the firm through information sharing and researching a much simpler way. This can be done using various tools that are available from several software companies. As Golomshtok (88) stipulates, it is significant to specify what a firm seeks to achieve with enterprise social networking. This scholar says that some people have considered enterprise social networking as the same as social media networking. However, Flynn (27) argues that social media is an extension of enterprise social networking. In this white paper, social media does not fall under the scope of the research. The focus is on internal communication between departments and individuals within the firm.
This new system will help ensure that the system administrator, that can be a mini-computer, appropriately serves workstation computers. According to Motiwalla (90), it is always important that all the personal computers used in the workstations are monitored for any threat. Traditionally, it would be the responsibility of the system administrator to monitor other workstation computers and eliminate any problem once it is detected. This process can take as long as 6 minutes for each workstation. For a large company such as the Union National Bank, which has hundreds of workstations, it may take months for the system administrator to monitor all the workstations. This may put this firm to a great risk because computer threats can arise at any moment. Software engineers, therefore, developed new systems that are proactive. In this case, the system administrator would be alerted if there is a threat to any of the computers. It would then address the issue as raised. However, this was still not good enough.
The system that is proposed for this firm is automatic. It uses an agent that is fixed on each of the workstations and will constantly monitor the workstation, detect any threat, and address it immediately. It would then relay information to the system administrator regarding the problem that was addressed so that further actions can be taken on the workstation and such threats are avoided in the future. The current system has the capacity of addressing any issues that may arise on its functionality. This system is automated, meaning that any issue that may arise concerning this system such as malware will be addressed with no intrusion from the administrator’s side (Olson 67).
How the product works
According to Norton (39), one should keep in mind how this system works to be able to determine how effective it can be to this firm, especially speaking about this system in its entirety. When talking about how this system works, the first approach will be to analyze the process of its operation free from any interruptions that may be caused by the malware within the system. The second analysis issue will be to determine how the system works when delivering service to various departments within an organization. The officers at the workstations may not be interested in understanding how the automated system functions to counter malware because this only concerns system engineers within the company. They only need to be aware of how the system enables them to manage data that is relevant to their operations.
However, both aspects of how this system works will be described. The first aspect will consider how it automatically detects threats and errors and handles them to avoid any disruption of the entire system. This part of the system will eliminate cases where the system goes down because of malware. One of the main issues raised by the management of the Union National Bank was that at times employees are forced to stop serving customers because of the system problem.
Pan (83) explains that the management server works with monitored computers at various stations to ensure that any problem within the system is addressed as soon as it is detected. The agents installed in each of the monitored computers will relay alerts about the state of the workstation computers. The management server will relay this alert to the console, which will in turn relay a configuration updates back to the management server. The management server will direct this configuration to the monitored computer at various workstations to address the issue that was identified. This would take place in microseconds. As a result, the monitored computers at the workstations will continue working without any form of interference due to malfunction that is caused by a virus or any form of breakdown. This means that this system will be able to address the issue of the bank and eliminate any cases of failure to attend to the customers. The software engineer or any other technician who is responsible for managing the system will also be able to determine the condition of each of the monitored computers at the workstations. In case any of them needs some form of repair or a complete overhaul, the agent will forward this information to the management server.
The technician will get the information from the management server and issue appropriate instructions on the action to be taken to ensure that the system works smoothly. After understanding how this automated system works to protect itself from threats and eliminate any form of failure, one also needs to learn how this system functions to enable various departments and employees within the firm to manage information and knowledge.
According to Alus (78), management of information refers to the process of making information available to all users who need it within the firm, how to refine it if this is necessary, and its storage for future use in a way that is secure. Security must be provided to avoid a scenario where classified information reaches people who are not meant to access it. This may cause serious consequences to the firm. The individual employees within the firm such as tellers or supervisors will have a workstation, which was described as monitored computers. It is at this desk that these officers will expect to get all the information they need to take different actions. For instance, the supervisor may need to know the transactions made by all the tellers who are under him or her. This officer will not be required to visit every workstation to determine the transactions made by the tellers. The diagram below elaborates on how this system operates to share the data.
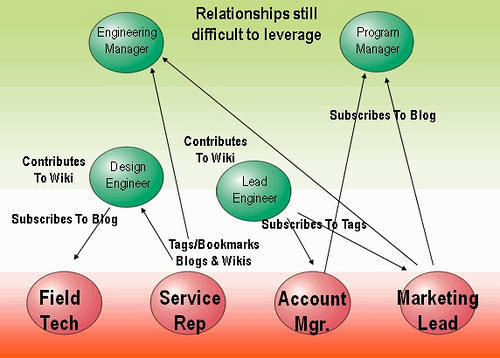
The above diagram sheds the light on different stakeholders within a firm who would play different roles in order to ensure that this system works successfully. As shown in the diagram above, any activity of the individuals in this system would be reflected in the database of the company. This information will be made available to the workstations of other stakeholders within this firm instantly. In other words, all the activities done by the service representative will be available to the accountant in case any transaction should be carried out to that effect. Similarly, the management will know activities done by the marketing unit in case there is a need to act upon it. This means that at no moment one will try to manipulate the system by withdrawing more than what is in his or her accounts.
This information will always be accessible for other relevant users of this system in real-time. Given that this system works in a wide area set-up, all the databases of this firm in various geographical locations will be able to use this information when needed. Immediately, this data is made available to the wide-area network, thus it will be fed on the application server. At this server, the necessary data refining will be done. For example, when a customer applies for a loan, it is necessary to determine his or her financial history with the firm and the capacity to pay back the loan. Such classified information of customers is not always readily available in the wide area network of the company. They are always kept safely in the database server. The application server will then search for this information from the database server and then determine the creditworthiness of the customer. After this information is made available at the wide-area network, workstation officers can access it and make the appropriate action. Also, the application server will refine all the raw data into information that can be used to make decisions. The refined data will then be sent to the database server.
Dimon (79) argues that to enhance the security of this system, each of the workstations will have a password that its user must enter before using it. In other words, only officers permitted to work at the station will be able to feed and retrieve information through that particular workstation. Again, the system will be keen to ensure that information fed or retrieved from a particular workstation has a clear history for future reference. This means that at no particular time an individual will retrieve or feed information through workstation A and claim that the information history can be traced from workstation B. This realizes security within the organization as each officer assigned workstation will be given a private password used to access the monitored computers. They will be responsible for all transactions taking place in that particular workstation. The application server is only available to the top management of this firm. The same case applies when dealing with the database server. All the classified information of this firm is kept in these servers. The diagram below further defines this system and how the wide-area network makes it possible for different departments in different geographical locations to share relevant data.
Based on the illustration on the above figure, it is clear that when this information comes from each workstation, it is fed into the wide-area network then makes the information available at the database of the firm. These databases will be accessible to other databases in other countries in a secured storage area network. Storage area network will make the information available to all databases on the firm in all regions as long as they are configured to the main database of the firm appropriately. The diagram above shows how three cities in the United States can easily securely share information through this system. It is also important to understand how the server works to ensure that all the data fed into it are safe and can safely be accessed when needed.
The above diagram shows how information gets into the server, how it is managed while in the server and storage enclosure back-pane which logically stores the data and acts as the backup storage center.
How the Product Solves the Problem
Implementation of private enterprise social networking for the Union National Bank is a costly venture that must have clear benefits to the firm. According to Borge (67), the implementation of this system may demand that the firm purchases special equipment that is necessary to make it functional. Some of the firms selling the software such as IMB and Yammer charge a lot of money, and the system must be able to deliver the intended service to the customers. The system must be able to solve some of the problems that are identified within the firm. It is only through this that the project will be considered viable. The following are some of the benefits that this system offers to the users.
Benefits to the firm and other stakeholders
This system must have clear benefits to the firm to be considered as worth investment it shall need. The researcher made direct contact with the management of the Union National Bank at its Abu Dhabi branch to determine some of the issues that they had in their management of information. The management was very categorical that the biggest problem was the frequent failure of the system due to a problem at the server or one of the computers within the system. They stated that this was costing them a lot, especially in cases where employees were forced to wait for the system to become active once again. The management also informed that this affected their ability to offer customers services appropriately in line with the mission statement of the organization. This system comes to solve this problem. The following are some of the direct benefits that this firm stands to gain if it successfully implements private enterprise social networking in its systems.
- Increased capacity of the tellers to deliver on the tasks assigned to them. The management units of this firm that were contacted by the researcher stated that employees working at the teller’s were not able to maximize their ability in delivering efficient service to customers because of the frequent failures of the server. This new system will eliminate this problem. Employees will be able to give their best to the clients.
- The system will increase the capacity of the supervisors to guide and direct other officers within the firm. The current system does not have applications that can allow managers to monitor every activity taken by every employee while in the firm. This means that some employees may underperform but the management may only realize this later when analyzing their output. With this new system, however, the management will be able to determine their output while at the station without making physical visits. This makes supervision much easier. Employees will be forced to deliver because of the fact they know that they are constantly under supervision (Flynn 67).
- Customer experience will be improved considerably. Cases, where customers are forced to wait in long queues without getting services due to problems with the server, will be eliminated. They will be served much faster and this will increase their satisfaction with the services offered by the firm. As Borge (92) observes, satisfied customers always act as evangelists to a company. In other words, they will not only come for more services but will also convince others to visit the firm and share their good experience. This will help the firm increase its market share.
- The information of this firm will be safe. This system offers the firm an avenue through which it can safely store its products. The safety starts from the workstations of the employees and to the storage servers. It is easy for the management to determine the person who could be leaking classified information of the firm by tracing the history of the information. This will deter such actions.
- Information processing and sharing is made less complicated through this system. This means that all departments within this firm can easily share relevant information whenever this is necessary.
- This system also benefits owners who will find it easy to access the necessary information from the firm to determine its progress.
Conclusion
The discussion above has demonstrated that this firm will need to implement this project to improve information and knowledge sharing among its employees. Yammer platform will be the most appropriate application for this firm which will come at a cost. However, the benefits of this system are massive. From the discussion above, it has been made clear how this system works to protect itself and to deliver services to the customers in this firm. The paper proves that this system is secure and the Union National Bank will be assured that intruders do not access its classified data easily. The management will also be sure that employees who are not loyal to the firm are easily identified when they try to sneak out classified information of the firm. System failure will also be eliminated because of its automated nature.
The detailed description of how this system works makes it clear on how the employees will be able to use this system to undertake various duties. It also elaborates on how the information will be made available to individual employees, departments within a branch, and branches located in different places. The discussion also demonstrates that the system will make this firm more efficient. It will be able to serve its customers in a better way. This will increase customers’ loyalty towards the firm, a fact that will help it increase its market share. Also, the system will enhance the supervision of employees, besides making it more convenient for all the relevant stakeholders to access the information they need about the firm.
Works Cited
Alus, David. Enterprise Risk Management. Singapore: World Scientific, 2008. Print.
Borge, Stein. Managing Enterprise Systems with the Windows Script Host. Berkeley: Apress, 2002. Print.
Dimon, Ron. Enterprise Performance Management Done Right: An Operating System for Your Organization. New York: Cengage, 2013. Print.
Fee, Jess. 10 Enterprise Networks to Improve Company Communication: Intelligent Social Managing Tools. Web.
Flynn, Nancy. The Social Media Handbook: Rules, Policies, and Best Practices to Successfully Manage Your Organization’s Social Media Presence, Posts, and Potential. Hoboken: John Wiley & Sons, 2012. Print.
Golomshtok, Alexander. Net System Management Services: Berkeley: Apress, 2003. Print.
Motiwalla, Luvai. Enterprise Systems for Management. Upper Saddle River: Pearson, 2012. Print.
Norton, Ann. E2 – Enterprise Management. Oxford: Elsevier, 2009. Print.
Olson, David. Enterprise Information Systems: Contemporary Trends and Issues. Singapore: World Scientific Publishers, 2010. Print.
Pan, Shan-Ling. Managing Strategic Enterprise Systems and E-Government Initiatives in Asia: A Casebook. Singapore: World Scientific, 2004. Print.
Schrage, Michael. The Real Power of Enterprise Social Media Platforms. Web.
Verhage, Lambertus. Management Methodology for Enterprise Systems Implementations. Delft: Eburon B V, 2009. Print.