IT Audit and Testing
Windows Operating System
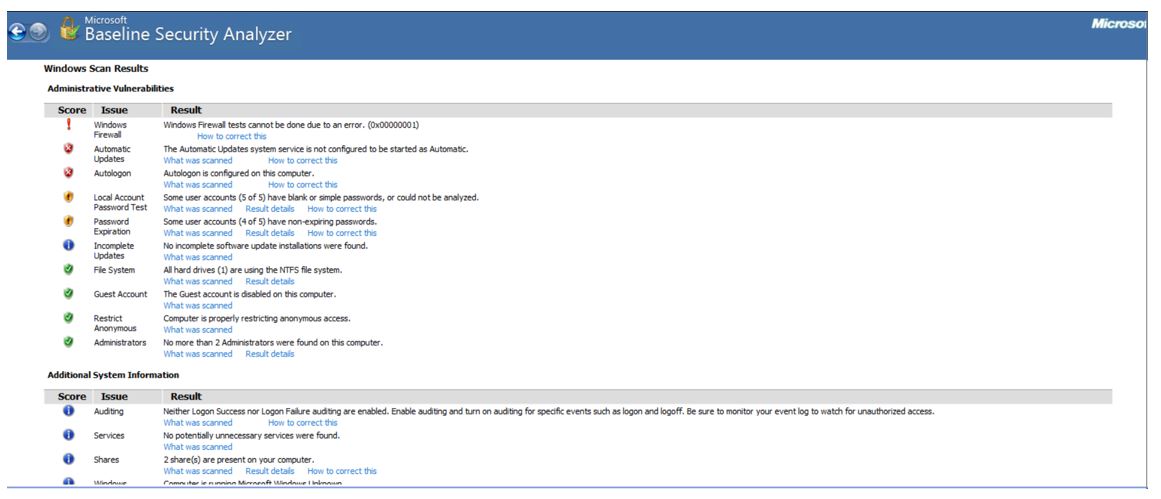
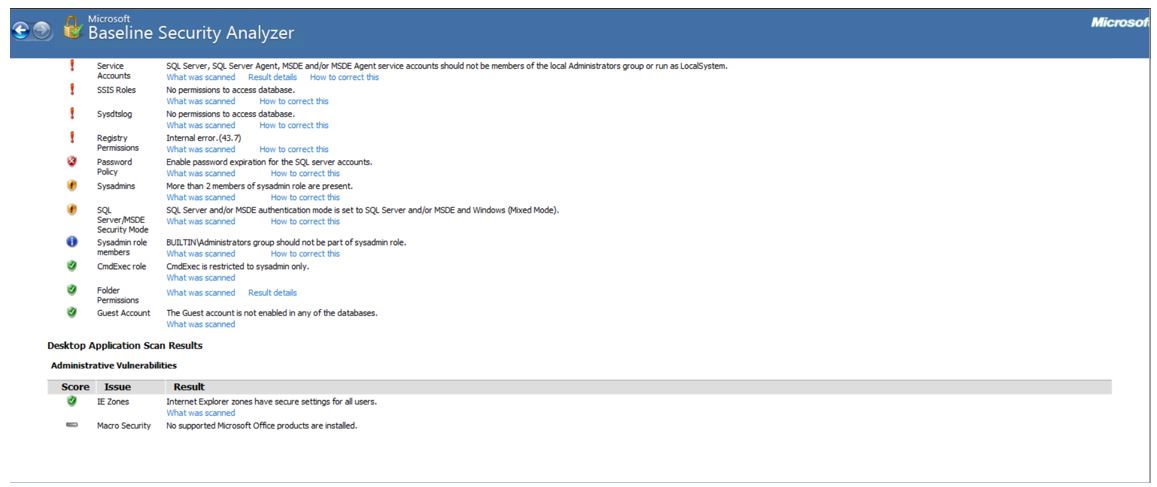
As seen from Images 1-4, some of the most serious security issues include the MBSA’s inability to test Windows Firewall due to an error. The MBSA detected that the Automatic Updates system service is not configured even though the best practice is for it to be started as Automatic. The security check discovered that autologin is configured on this computer, meaning that anyone who is able to obtain access to the computer can retrieve all the computer’s contents. The MBSA failed to run a local account password test. It discovered that some of the users of this computer have blank or simple passwords, and four out of five of them use non-expiring passwords. To improve the security of this computer, it is recommended to enable password expiration for the SQL server accounts.
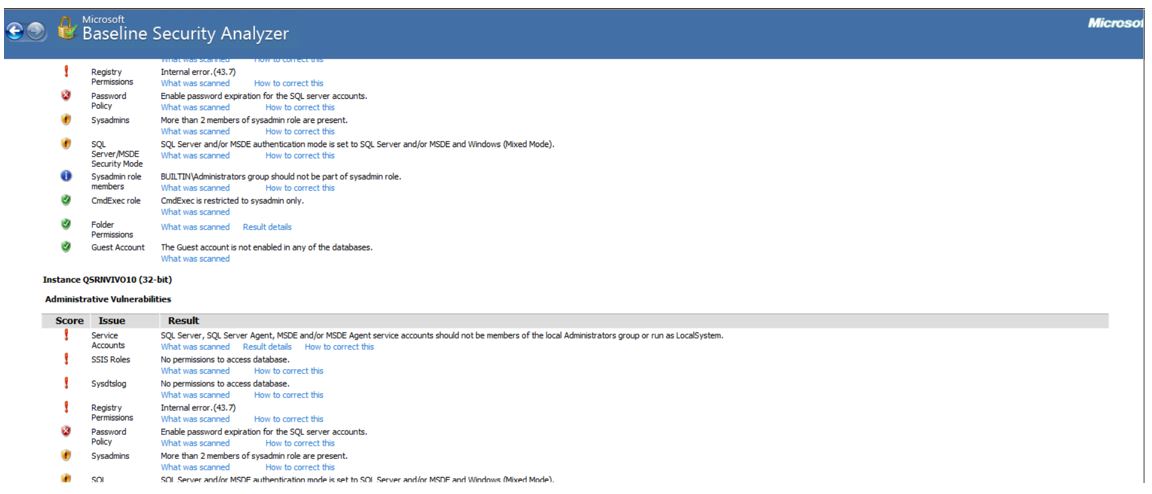
On the positive side, the MBSA reported that other common administrative vulnerabilities have been avoided. For instance, as per the report (see Image 1), all hard drives (1) are using the NTFS (New Technology File System) file system, a proprietary journaling system developed by Microsoft. This computer does not support guest accounts and restricts anonymous access, which improves its security. On top of that, as Instance QSRNVIVO10 has shown (see Image 4), guest accounts are not permitted on any of the databases. Lastly, this computer is run by no more than two administrators.
The additional information obtained during the MBSA check has shown that neither login success nor logon failure auditing is enabled. It is recommended to enable auditing and turn on auditing in the case of specific events such as logon and logoff. This measure would be helpful with monitoring the event log to identify unauthorized access. As for unnecessary services, none were found during the check. For some reason, the software was unable to figure out which version of Windows was used and reported that the computer was running Microsoft Windows Unknown.
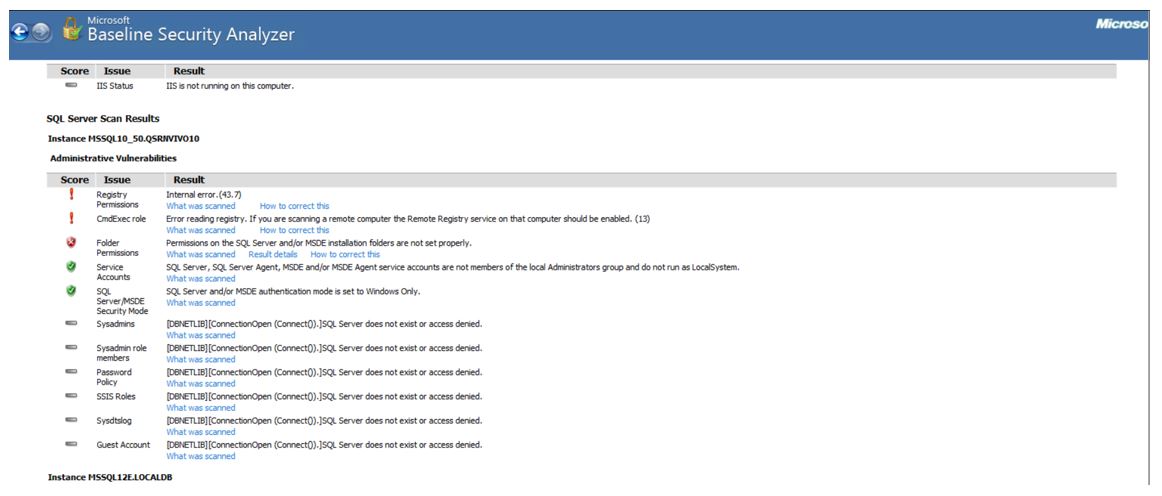
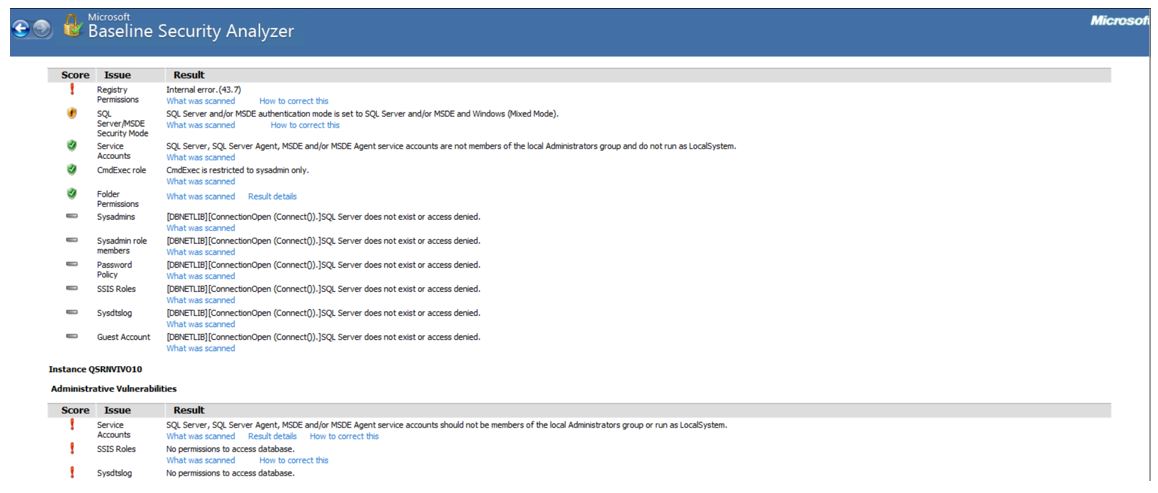
SQL server scan has demonstrated one vulnerability and two positive results. Firstly, it turned out that the permissions on the SQL Server and/or MSDE installation folders were not set in the best way possible. On the other hand, Instance MSSQL12E.LOCALDB (Image 3) suggests that folder permissions are in perfect order. Further, the SQL server scan has shown that SQL Server, SQL Server Agent, MSDE, and/or MSDE Agent service accounts were not members of the local Administrators group. This implies that they cannot run as LocalSystem, which would be a threat to the security of the computer.
The same results were obtained as reported by Instance MSSQL12E.LOCALDB (see Image 3), so the check was passed. Lastly, the MBSA has found no issues with SQL Server/MSDE Security Mod. The report shows (see Image 2) that SQL Server and/or MSDE authentication mode is set to Windows Only. However, as seen from Image 3, SQL Server and/or MSDE authentication mode is set to SQL Server and/or MSDE and Windows (Mixed Mode). The last check by Instance MSSQL12E.LOCALDB concerned the CmdExec role, and it was passed as it was restricted to sysadmin only. In summation, this computer requires some improvements to enhance its security and protect it from threats.
IT Security Risk Management at the UAE Bank in Dubai
Insider Threats
Step 1. Risk Framing
- Task 1-1. Risk assumptions.
Insider threats pose serious risks to financial institutions. This issue encompasses all kinds of threats that come from employees, third-party partners, set up contractors, and other freelancers. Anyone who has access to the banking environment can eventually take advantage of its vulnerabilities. For the managers of an organization, the wrong assumption to build an IT security strategy around would be that this problem does not apply to them. The UAE Bank in Dubai operates on the assumption that as much as it wants to trust all the individuals involved, statistically, the majority (60%) of cyber-attacks come from within (Marous). Therefore, the UAE Bank of Dubai chooses to take this issue with utmost seriousness and develop its IT security strategy accordingly.
- Task 1-2. Risk constraints.
Insider threats are fairly difficult to identify and prevent. The reasons for attacking a company from within show a significant variance. Hueca et al. explain that insider threats may be driven by motivation, opportunity, or rationalization (4). For example, an employee struggles financially or has sick relatives, which drives him or her to gain access to the company’s resources illegally. Sometimes, the system itself provides an opportunity for someone with malicious intentions (for example financial record databases can be accessed, searched, and manipulated without such events being logged). Lastly, there may be rationalization taking place (for example a contractor attacks a company because they think that they were not paid fairly). As seen from this classification and examples, insider threat detection has everything to do with understanding people’s psychology as well as the work environment dynamic. The latter is often impossible as individuals typically prefer to keep their motives to themselves.
- Task 1-3. Risk tolerance.
Risk tolerance defines to which degree a financial institution is ready to accept risk, be it expressed in either qualitative or quantitative terms (Hopkin 89). Risk tolerance is used as one of the key criteria in the decision-making process (Hopkin 103). The emergence of the new economy in which the existing risk-reward relationship has become much less predictive and more complicated makes defining risk tolerance quite difficult. In the banking sector, compliance risk tolerance may be the most prominent type. Financial institutions operate in environments characterized by relentless changes that often concern legislation. It is recommended that dynamic banking systems keep their compliance risk tolerance close to zero. In other words, the UAE Bank in Dubai cannot and should not tolerate any incidents that undermine its legality, insider threats included.
- Task 1-4. Priorities and trade-offs.
Drawing on the previous point, it is safe to assume that one of the top priorities for banks is meeting regulatory and compliance requirements. Previously, many financial institutions used to choose the reactive mode when it came to regulations and compliance. In other words, they would only change in response to regulatory orders, audits, or other pressure. It is essential that the UAE Bank adopts a proactive approach and establishes a stronger connection between legislation and its business strategy.
A trade-off, in this case, would be operating costs that might not be as low as a bank would like them to be. Marous reports that operating costs reduction ranks third among the top priorities for modern banks, especially for large organizations such as the UAE Bank in Dubai. Marous explains that financial organizations put a lot of time and effort into cutting costs wherever possible. However, sometimes these efforts are exerted without proper understanding of how short-term financial gains affect the organization on the whole. The UAE Bank cannot and should not cut risk management expenses as safety is vital to the organization’s operations and reputation.
Step 2. Risk Assessment
- Task 2-1. Threat and vulnerability identification.
The two main types of insider threats are called turn cloaks and pawns, the first of which is malicious and intentional and the second are unwilling participants. Turncloak is an insider (employee, third-party partner, contractor, or freelancer) who abuses his work privileges (Hopkin 201). It could be for-profit or sheer entertainment – this type is driven by all sorts of motives. A pawn, on the other hand, is a normal employee who might be unfortunate enough to let an error slip, which is later exploited by a turn cloak. Some of the mistakes that a pawn might be responsible for happening are losing gadgets with company data, sending a sensitive document to the wrong person, or installing malware. Insider threat indicators fall into two categories: digital and behavioral (Hopkin 152). Among the digital indicators are downloading or accessing large amounts of data for no apparent reason, accessing sensitive data outside one’s job function, and accessing data that is outside of a person’s normal behavioral profile. Behavioral indicators include attempts to bypass security, staying at work overtime, having a history of violating corporate policies, and discussing resignation.
- Task 2-2. Risk determination
Ignoring insider threats may lead to many unwanted effects for the UAE Bank in Dubai. For instance, a malicious employee may sabotage systems and send proprietary data to contending companies, which in turn, will take advantage of the access to unique technological solutions. Another possible situation would be an insider obtaining access to customers’ financial records and manipulating them for personal financial gains. Lastly, some insiders might want to abuse their work privileges to pursue their non-financial interests. An example would be illegally retrieving staff personal data to stalk female coworkers. A company that allows it to happen without taking proper measures risks not only losing its valuable employees who no longer feel safe but also ruining its reputation for both potential employees and customers.
Step 4. Risk Monitoring
- Task 4-1,2. Risk monitoring strategy and risk monitoring.
Insider threat monitoring strategy needs to include two elements: human resources management and technology. As mentioned above, employees’ ulterior motives remain concealed, which makes it difficult to predict whether any of them could potentially have malicious intentions. Firstly, the employment process needs to include extensive background checks. Secondly, the human resources department together with other relevant professionals might want to assess how much risk each person or team poses based on their work privileges such as access to databases, use of proprietary software, and others. As for the second aspect, banks should consider having better visibility on user activity by installing relevant monitoring software. This measure could be expanded into a full-fledged intelligence-based approach. Such an approach could employ AI and machine learning tools for detecting abnormal activities and fraud.
Malvertising
Step 1. Risk Framing
- Task 1-1. Risk assumptions.
Recent statistics have revealed that one in every one-hundred online advertisements are malicious (Sullivan). While at first glance, this share might not seem to be anything significant, as explained by Sullivan, more than 20% of user sessions may include interactions with malicious or disruptive ads. For this reason, the UAE Bank of Dubai does not dismiss the danger of malvertising.
- Task 1-2. Risk constraints.
The efficiency of malvertising detection is contingent on two factors: employees’ digital literacy and cybercriminals’ efforts to avoid detection. Employees’ online activities are generally not easy to control without resorting to micromanagement, which complicates predicting possible attacks. At the same time, cybercriminals have been putting a great deal of effort into earning a good reputation among third-party vendors and designing ads in a way that they are not distinguishable from harmless ones.
- Task 1-3. Risk tolerance.
As with any other bank, the UAE Bank of Dubai’s success relies on the degree of trust that its customers are ready to put into it. A disruption caused by malvertising and subsequent leakage of data or other adverse outcomes might compromise the bank’s reputation. For this reason, the UAE Bank of Dubai should adopt the policy of zero tolerance for safety threats.
- Task 1-4. Priorities and trade-offs
As mentioned in the previous section, any company faces a conflict between cutting costs right now and investing more into aspects that have the potential of yielding benefits in the long run. Safety concerns should not be treated as a trade-off: they need to be a priority, even if it means piling up more costs.
Step 2. Risk Assessment
- Task 2-1. Threat and vulnerability identification.
Malicious advertisements can seize users’ attention in two ways. The first scenario is when a user is manipulated by a pop-up ad or an alert and clicks on it by accident (Dwyer and Kanguri 29). The second scenario is somewhat trickier: the attackers employ drive-by download techniques, which expose the user to malicious content while the hosting website loads (Dwyer and Kanguri 29). Once the malvertisement identifies a vulnerability, it installs info-stealing malware or ransomware onto the victim’s computer.
- Task 2-2. Risk determination.
The consequences of exposure to malvertising are two-fold: the attacks may impact both the stability of the banking system and on a larger scale, the company’s reputation. While browsing the Internet, the bank’s employees may come across malicious ads and unknowingly let them take advantage of their computers’ vulnerabilities. An alternative scenario would be malvertisement making its way on the bank’s official page. In this case, the page’s visitors will suffer from exposure and likely associate the bank with poor safety standards.
Step 4. Risk Monitoring
- Task 4-1,2. Risk monitoring strategy and risk monitoring.
The Malvertising monitoring strategy needs to rely on two aspects: human resources management and technology. Firstly, bank employees need to be educated on safe Internet use and become familiar with suspicious ads, redirects, and other online activities. The staff needs to be knowledgeable enough to make smart decisions on a daily basis. The second part of the strategy should include the implementation of cutting-edge ad scanning systems for faster and more efficient malvertising detection. For all its efforts, the security team should still operate on the assumption that they cannot prevent 100% of all attacks. Therefore, there needs to be a standardized plan in place that would describe in detail how to handle the aftermath.
Works Cited
Dwyer, Catherine, and Ameet Kanguri. “Malvertising-A Rising Threat To The Online Ecosystem.” Journal of Information Systems Applied Research, vol. 10, no. 3, 2017, p. 29.
Hopkin, Paul. Fundamentals of Risk Management: Understanding, Evaluating and Implementing Effective Risk Management. Kogan Page Publishers, 2018.
Hueca, Angel L., et al. Exploring the Motivation Behind Cybersecurity Insider Threat and Proposed Research Agenda. 2016. Web.
Marous, Jim. Top 10 Strategic Priorities for Banking in 2017. 2017, thefinancialbrand.com/62711/top-10-strategic-priorities-for-banking-in-2017.
Sullivan, Laurie. Malvertising Found In 1 In Every 100 Ad Impressions.2019. Web.