Secure Interaction Designing, a vital component in today’s world of interface designing is the practice of designing a system, which aims at safeguarding the interests of the legal end users of the computer system. Various concerns have cropped up during the past times, which include the likes of viruses, malwares, spywares and phishing apart from traditional issues like online tracking systems and involuntary revelation of personal information.
In order to save the user from harm, the software’s behavior must be in coherence with the anticipation of the user. Thus attending to security issues need an understanding of the user’s perception of working of the system. If not, the user would not have the means to foresee and comprehend the outcome of his actions. Consequently, secure systems must implement security judgment founded on the grounds of user-oriented events but at the same time should permit those events to be articulated in well-known forms. (Gupta, 2007)
How admonition fits into an overall security strategy
Security can be implemented by means of employing two approaches, namely: security by designation and security by admonition. In the Security by designation approach, subsequent to a user’s triggering an event, the system takes the suitable actions linked with security issues. For instance, double-clicking on a folder icon would lead to rendering the contents of the folder. While in Security by admonition approach, it would present notifications, which the user needs to attend to and take suitable action, based on his judgment, from the available options offered by the system, and the system would display a caution message when the user attempts to proceed with an action, which might cause harm. This paper looks into the intricacies of the Security by Admonition approach and its effectiveness as a security strategy. (Pramod, 2007)
Providing security as a component of the product or service package has increasingly become a trend amongst vendors who consider this as a vital element of their business strategy. However, in many security features, the concluding security-related decision is left to the end-user. According to experts, this policy originates in a clash between offering security and usability, where security typically encumbers and usability generally aids the user in accomplishing a job. (Gupta, 2007)
Successful implementing admonition as a security measure
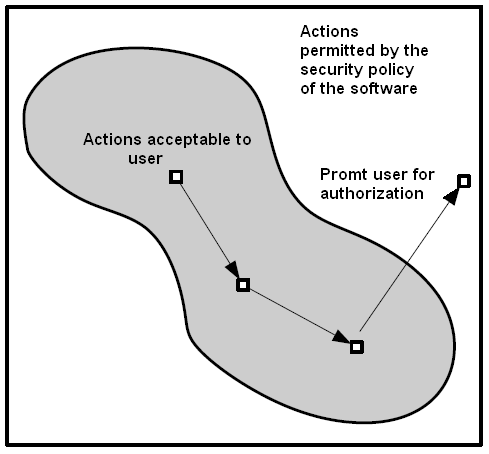
The above figure exemplifies a method employed to surmount the previously mentioned conflict. The security strategy symbolized by the rectangle incorporates a wide range of activities, which the user might find either adequate or else improper. Each time the user takes a course of action, which may be undesirable for him, but at the same time is allowable as per the security policy, the system calls for user affirmation of the action. This approach, entitled as security by admonition, leaves the ultimate decision to the end-user. (Pramod, 2007)
Some illustrations of these notifications are the firewall popping up a dialog box requiring the user to authorize a process on a certain server requesting access to run on a particular port, the Internet Explorer phishing filter offering a caution message to the user that the webpage being navigated might be unsafe and the Firefox browser requiring heightened privileges with regards to some signed JavaScript code. Security by admonition policy relies on the understanding of the end-user regarding security and his computing knowledge to take proper decision. (Gupta, 2007)
The admonition approach allows a user to intervene instead of the system taking a security-related action, which might hinder the task of the user. However, an issue in the policy of admonition is at what time to warn and under what circumstance to proceed. The following figure explains this conflict.
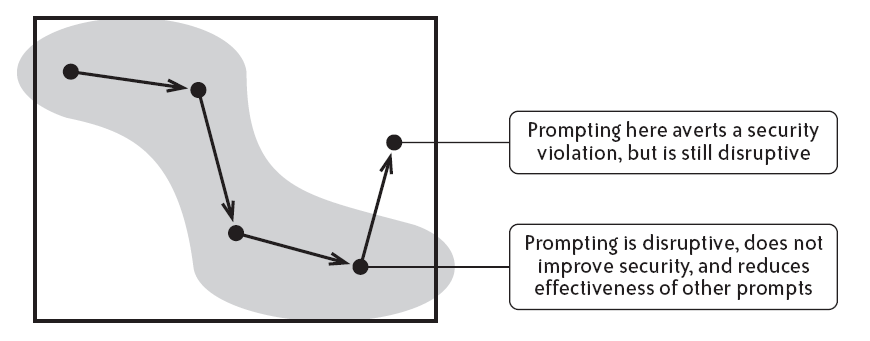
The effectiveness of admonition as part of a security system
Providing too little caution exposes the user to potential hazards whereas on the other hand presenting the user with too many caution messages vexes the user. The greater the incongruity between acceptable and permissible actions, the more difficult it is for the system to tradeoff between security and usability. (Gupta, 2007)
Another issue in this policy is the aggressiveness of designs in the form of compelling users to respond to a prompt. It generates a lot of annoyance amongst users at times. Effective designs should be conspicuous by their proximity and importance instead of their aggressiveness, which gets in the way of the accomplishment of user tasks. Examples of good designs can be the appearance of a transient bar in browser windows that doesn’t obstruct the view of the page as a display prompt would, displaying information on the cursor trail, or reminders concerning passwords emerging beside a password field when it is active. (Pramod, 2007)
Security by admonition as a successful IT security strategy can be analyzed in two distinctive methods. Firstly, as a social process, which makes entities act in a deliberate way based on social, conduct or secondly, with computer systems that plainly request an answer to a question. Social engineering can be considered as one of the most influential instruments in a firm’s IT security policy.
As children, everyone has been educated to differentiate between correct and incorrect. The admonition is a policy simply based on that teaching. Its effectiveness depends on how well systems are designed and to what extent the balance between security and usability is achieved. To confront the challenges thrown up the admonition approach is not an effortless job for multinational corporations. However, overall it presents a relatively low outlay alternative as compared to existent complex security structures, which may give it an edge above the others. (Pramod, 2007)
References
Gupta, Ashok K, Uma Chandrashekhar, Suhasini V. Sabnis, Frank A. Bastry; 2007; Building secure products and solutions; Bell Labs Technical Journal; 12, 3, 21-38; Alcatel-Lucent; Bell Labs, Murray Hill, New Jersey.
Pramod, Hari, V. Koppol, Ashok K. Gupta, Dor Skuler; 2007; A service-delivery platform for extending security coverage and IT reach; Bell Labs Technical Journal; 12, 3, 101-119; Alcatel-Lucent; Bell Labs, Murray Hill, New Jersey; Bell Labs, Cornelius, North Carolina.