Management Summary
This proposal details the implementation of the RFID prisoner tracking system within the Australian prisoner system. Basically, the system utilizes medical grade RFID chips which will be placed into prisoners as a means of tracking their movement throughout the prison which would result in a faster and more efficient method of prisoner tracking.
The benefit of the Identchip tracking system is the ability to track prisoners wherever they are in the prison in a simple and cost effective manner that does not rely on scaling up the number of surveillance cameras of guards in order to locate a particular prisoner. Initially, a test will be conducted in the Sydney Prison system in order to prove the effectiveness of the system. During the first 3 months, the project team will inspect the prison, setup the main control room and servers after which the project team will talk with the guards and give them a brief orientation on how the system would work. After that, it is estimated that it will take 8 months to implement the rest of the project which will consist of installing the RFID readers and scanners, placing in the new prison doors, training the personnel at the prison and finally injecting the prisoners with the RFID chip. The overall cost of the project is estimated at $744,652 which does not include miscellaneous and additional costs that the company may incur during the process of installation.
Company Profile
Company Introduction
Silent Hill Prisoner Control Inc. aims to improve the current methods of prisoner tracking within the prison system of Australia through the use of embedded RFID technology. The IdentChip, a small innocuous device no bigger than a grain of rice, can be surgically inserted within the skin of a prisoner enabling a safe and efficient way for prison staff to access the personal history of prisoners as well as track their movements within the jail without having to track them via CCTV cameras and prison personnel. The RFID system can also limit the ability of prisoners to enter particular areas of the prison by keying the RFID frequency emitted by the chips to the door locks which helps to minimize instances where prisoners inadvertently get a hold of the keys to a restricted area of the prison.
This document has been created in response to the Gotago project in order to create an effective prisoner tracking solution for the Australian prison system. As such, this document aims to provide a detailed description of Silent Hill Incorporated’s proposed RFID tracking system which will be utilized to monitor the activity of prisoners as well as restrict their movements to designated areas of activity. The primary goal of this paper is to show that the solution proposed by Silent Hill Inc. is plausible and that it would be able to resolve the security and monitoring needs of the Australian prison system.
The introduction of this paper will start off by discussing the contents of the proposal, the scope of the project, its objectives, the stakeholders involved as well as the general requirements of the project itself. After this, what will be discussed is the background of the solution and how it is applicable in the case of Australia.
At this point in the paper, the proposed system for implementation will be identified along with a top level overview of the proposed solution and its architecture. After which a detailed specification of each component and its purpose in the solution will be conducted in order to clarify any potential issues with the project. The components that will be discussed are separated into two distinct categories, namely functional and system components. The RFID tracking software will be the primary functional component while the system components will consist of the RFID readers, the embedded chips as well as the servers that are to be used to monitor and record prisoner activity.
After the proposed system of prisoner tracking has been introduced, this paper will then subsequently identify the implementation and support plan necessary for bringing this project together. This will involve the testing procedure, the staffing requirements and the general progression of the implementation procedures. A Gatt chart will be utilized in order to show the implementation schedule that will be utilized in this project.
Lastly, this paper will conclude by showcasing the estimated cost of implementation as well as the annual cost of maintenance and support. By doing so, this paper will be able to properly showcase the effectiveness of the proposal and make subsequent recommendations regarding the way in which full scale implementation can be accomplished.
Project Team
Silent Hill Prisoner Control Inc. project team is composed of (Naif, Naif2, Naif3) who can be considered as a group of highly skilled experts in the development of RFID based tracking systems. The previous experience of the group has been in the development of innovative solutions in embedded patient records in RFID chips as well as their commercial application in package tracking as well as in the automated toll booth system used in many of today’s highway systems.
Case Study Background
The Verichip, a small innocuous device no bigger than a grain of rice, was debuted in the latter half of 2004 as being a safe and efficient way for hospitals to access the medical history of a patient so as to speed up treatment and recovery. In a way, the advent of this particular type of technology could be thought of as a medical milestone, the future of medicine so to speak wherein doctors, EMTs, nurses and various other medical personnel can quickly and accurately diagnose a patient’s current condition based on their medical history should the patient be unconscious, unable to speak or is relatively unaware of their own history of medical care. From the point of view of medical practitioners, the use of medical “chips” is “a positive facilitator of medical care since not only can doctors respond quickly and efficiently to a patient’s condition but they can avoid utilizing particular medicines, procedures or methods of treatment should the patient’s medical record reveal a possible adverse reaction to the intended procedure”. Despite these apparent advantages, privacy concerns are at the forefront of the debate against their usage by the general public due to the potential for disreputable individuals to gain access to a patient’s private records.
It is based on the design specifications of the Verichip that Silent Hill Inc. is creating the Identchip which is a small, innocuous device that will be inserted into prisoners so as to provide an immediate means of identification and tracking. The technology has proven to be effective in not only enabling a person’s records to be stored on a device no larger than a grain of rice, but also allows accurate identification given the unique digital signature that each chip has.
The main innovative feature of the IdentChip is that it is an inconspicuous method of tracking and control that is not immediately visible to prisoners. One of the main drawbacks in tracking prisoners and preventing their escape is that it is necessary to keep them in sight. Unfortunately this is not possible in all cases due to sheer amount of TV cameras and screens necessary to keep an eye on every single action of each prisoner. This is neither feasible in terms of the amount of personnel needed as well as affordable due to the amount of video surveillance that would need to installed. A more budget friendly solution would be to track the prisoners via a system where the RFID chip “checks in” to scanners that are scattered around the prison perimeter. This in effect allows a seamless monitoring process without the need for a visual of the prisoner’s current location. Not only that, it allows for immediate identification of a prisoner since each RFID chip can be configured to release a particular signal that is unique to that chip.
The end result is that this allows an immediate and efficient method of prisoner tracking wherein the personnel at the jail can track and observe the frequency of unusual behavior without the prisoner knowing that they are being observed. Furthermore, such a system helps to prevent fights from breaking out within the prison premises since it allows the prison guards to determine if a prisoner is in an area where he/she should not be.
The corridors and doorways of prisons can be equipped with RFID readers which enable inmates to enter only into specific cells and corridors. Not only that, it can be utilized to track the number of meals they have, the amount of time they spend out in the yard as well as other facets of prison life. Combined with a server system that handles the verification and identification process, a separate system would be running in the background which helps to track the frequency of behavior and creates “red flags” when an unusual amount of time is spent by one prisoner in an area where they should not be. Repeated instances of this would result in an investigation leading to the possible prevention of a breakout in progress.
Larger tracking devices, such as the ankle monitors used for home confinement, are far too bulky and expensive to utilize. There is a limited capacity for freedom of movement (i.e. being able to take a shower and do other activities involving the body) as well as makes prisoners know that they are being tracked resulting in a greater likelihood of them focusing on some means of removing the ankle monitor in order to accomplish particular activities. Issues related the cost of the ankle monitors also need to be taken into consideration since one ankle monitor can cost as much as $450 with larger costs being associated with monitors that require a longer range (as needed in the case of prisons since inmates need to be able to move from one area of the compound to the other for eating, exercise, personal hygiene, etc.). The last problem with ankle monitors is the fact that they need to be charged on a daily or weekly basis in order to function properly. This creates more logistical issues that need to be tackled and creates the potential for prisoners to go untracked by them simply neglecting to charge their monitors. When taking all these factors into consideration, it can be seen that the Identchip developed by Silent Hill Inc., is a superior product as compared to an ankle monitor since it enables a prison to track inmates through a smaller device that cannot be easily removed.
In order to test this system, an initial preliminary test will be conducted in the Sydney prison system. This entails surgically inserting the chips in the form of a short 1 minute procedure wherein the prisoners will be informed about how they will be tracked and monitored. RFID sensors will be attached in various corridors and a test group will be used to try cell doors that respond to RFID tracking. Once the group is satisfied with the results and the viability of the project, a full scale implementation will be conducted in the remaining prison systems within Australia. It is estimated that full completion of the system will take approximately 3 years given the need to modify the doors of the facilities, installing the RFID scanners, placing in the server and tracking system as well as training the personnel of the facilities regarding how to use the system.
It is estimated that the total cost of the project will be $744,652. This cost is related to the necessary equipment and programming architecture that would need to be put in place to ensure the effectiveness of the system. The cost of the project includes the cost of hardware and software installation as well as the preliminary injections of the RFID chip into the current prison population; however, this does not include future costs associated with new prisoners entering into the system and the need to insert new RFID chips into them.
It is the belief of the team from Silent Hill Prisoner Control Inc. that through the implementation of this system, a more efficient and effective method of prisoner tracking can be created which can result in a safer prison system.
Scope
In Scope
This proposal will focus on Silent Hill Inc’s recommended solution to the prisoner tracking problem of the Gotago project. This paper aims to meet the requirements established by the Gotago project which will encompass aspects related to the design of the project, the type of technology that will be utilized and the means of implementation that will resolve the aforementioned tracking issue.
The following list outlines what the researchers consider the necessary scope of the project and its intended solution:
- Software and hardware that directly relates to the operation of the RFID tracking system. This will include devices that send signals that can be tracked by readers as well as the necessary software to identify what particular set of designated codes relate to a particular prisoner and a log of their activity.
- The ability of the RFID tracking chip to immediately allow guards to identify prisoners based on information in the chip itself. This relates not only to the capacity for the chip to store information but also entails the capacity to distinguish multiple chips in a single area as well as the ability to “hone in on” a particular chip when in a crowd.
- Staff training that would be necessary in order to implement the system. This entails training the staff of a prison system regarding the capabilities of the RFID tracking system and how it can be utilized by both a control room (i.e. the main tracking center) as well as by individual guards utilizing a hand held tracking device.
- Management of the project during the design and implementation states as well as ensuring ongoing management after the project has been completed.
- Installation of the proposed solution at the testing location. This entails creating the main monitoring room, installing the readers and having to place the trackers into the prisoners themselves.
Out of Scope
It is at this point that this paper will outline what is outside the scope of the project and will not be discussed in the proposal and will not be included in the Gatt chart scheduling or in the proposed budget.
- While this paper will recommend the type of staff required to run the tracking system, any staff needs associated with guards or administrative services have been deemed as being outside the scope of this project and will not be expounded upon.
- Any office material that will be purchased or rented that is not directly involved in the implementation of the project.
- The financial issues of the individual prisons (i.e. costs related to food, added security, guards, etc.)
- Training for staff that falls outside of the original scope of the project.
- The Identchip will be implemented primarily within Australian prison system. As such, potential implementation that falls outside of the scope indicated (i.e. implementation in other countries) will not be addressed.
- Issues pertaining to legislation involving proper care and ethical treatment of prisoners will similarly not be tackled in this paper.
Assumptions
It is the assumption of this project that through the implementation of the Identchip system, tracking prisoners will be easier and a lot more effective as compared to present day methods which will help to not only reduce costs but increase the capacity of security personnel to monitor all aspects of prisoner activity thus leading to the prevent of any attempts at escape or violence
Objectives
The objectives developed by the research team are as follows:
- To assess the requirements of the Identchip system and propose a solution for the current issue of prisoner tracking in the Australian prison system.
- To discuss in detail the various aspects of the proposed system, its components, the processes that will go into its implementation as well as the necessary hardware, software and manpower needed to ensure its operational effectiveness.
- To provide a sufficient costing report, a conclusive summary of the project as well as an implementation plan for the Gotago project.
Stakeholders
Corporate Social Responsibility (CSR) can be classified as a form of corporate self-regulation which is integrated into the business model of a particular business or enterprise in order to ensure a degree of compliance to ethical standards, laws and regulations within their chosen market. The end goal of this particular method of ethical business practice is to ensure that a company or organization has a positive rather than negative impact on communities. Thus, when it comes to implementation of a better way of prisoner tracking, it should be done in a manner that does not adversely impact members of the local community. It is based on this that the following are the stakeholders involved in the project:
Silent Hill Inc.
It is the vision of Silent Hill Inc to develop a system of prisoner tracking that will enable prisons to cut down the cost of surveillance (i.e by hiring fewer guards) while at the same time increasing the prison’s capacity to monitor it’s prisoners. Thus, it is currently developing its Identchip system which promises to be a game changer for prisons all around Australia. Overall, Silent Hill Inc. is aiming to become a leader in the field of prisoner tracking.
Australian Government
Through the implementation of the Identchip prisoner tracking system, the Australian government will be able to save significant amounts of money on the cost of prison operations. This in turn could go towards improving the conditions within prisons such as better access to medical care and more productive activities (i.e. classes so that inmates can learn skills which they can apply outside of prison). It is expected that once the Identchip system has been successfully implemented, this will result in altered operations for local prison systems towards more efficient and effective prison management without having to scale up personnel.
Prison Staff
Through the implementation of the Identchip prisoner tracking system, the job of the support staff will be that much easier since they will be able to immediately monitor and restrict the movement of prisoners throughout the facility. By knowing where all prisoners are at all times, this helps to reduce the need for a block by block examination of the entire facilities of the prison and makes their job safer since they do not need to be among the general prison population to conduct a daily headcount of the prisoners.
General Public
By putting in place a system that makes prisons more secure, the general public will greatly benefit from fewer instances where wanted criminals have broken out of jail. Though the public will not be informed how the system works, they will be assured that such a system results in safer streets with the assurance that dangerous convicts will remain behind bars.
Requirements Analysis
The following list will showcase the requirements of the Identchip and its supporting system as required by the project. What will be shown are the various functioning and nonfunctioning requirements of the system and how they are meant to operate.
Stakeholder Requirements
Identchip Identification Record
- Each Identchip must link to a complete record of the prisoner via the serial number on the chip which entails their block number, cell assignment, list of prior offenses, level of danger, prior escape attempts and time till release. This is for guards to be able to immediately identify prisoners on sight without wasting time by checking on the prison’s information database.
- The Identchip must have its own unique identifying digital signature to allow handheld and wall mounted scanners to immediately distinguish prisoners. Such a feature is important given the need to distinguish who is who through the scanning process.
- The Identchip must have a corresponding facial match in the database that must be updated on a yearly basis for long term prison inmates. This is due to the various changes to a person’s physical appearance that may occur during incarceration (i.e. growing facial hair, getting thinner, fatter, etc.). Accurate visual identification is important for prison guards especially in cases where there are multiple prisoners in one area
- The Identchip must be implanted sub-dermaly to such an extent that obvious tampering in order to get rid of it (i.e. cutting one’s arm open) would be immediately apparent. This is to prevent prisoners from summarily removing the chip in order to avoid identification.
Cell Block and Cell Access Registration
- The Identchip will be utilized to replace the current need to have multiple guards in various entrances and exists in order control the flow of prisoners from one area of the prison to another. Utilizing automatic doors that have RFID readers on them, this will limit the ability of prisoners to gain access to other parts of the prison without the appropriate RFID code.
- Unauthorized personnel without the correct RFID registration will be barred from entering specific sections unless an override is utilized within the master control room of the prison.
- Access to cells and washrooms within the prison system will similarly be restricted based on the RFID registration of a prisoner with specific time slots being allotted for particular batch numbers. If a person does not belong to batch that is supposed to use a facility at a particular time they will not be allowed entry.
- Prisoners will be informed how they are prevented from utilizing facilities at a particular time (i.e. via the Identchip system). They will be informed that they are being monitored and that the monitoring personnel are also the ones that limit access.
Meal Registration
- Similar to the concept utilized in automatic toll booths, each prisoner will have a record of the amount of meals that they are allotted for the month which will be tracked by the system through their Identchip. This is to prevent instances where prisoners go back multiple times in line in order to obtain more food which they then sell to other inmates.
- The meal ticket registration system also helps to track unusual activity from a prison in instances where they avoid eating for prolonged period of time which can be utilized as an indicator for potentially adverse behavior (i.e. a potential escape attempt or drug use)
Medical Requirements
- Along with an individual’s prison record, the Identchip must also link to a full medical history of the prisoner.
- The medical information must indicate any prior health issues, allergies, operations, complications and other data that would be necessary in order to implement proper medical care during an emergency.
- These medical records, similar to the case of the Verichip, must be easily accessible via a scan at the prison’s medical center.
- The information therein must be updated on a yearly basis after each full physical examination or during instances where a specific type of medical treatment needed to be implemented.
System Requirements
Location History Information
- Through the IdentChip, a record must be kept of the various locations that a prisoner has been in on a daily basis.
- Pattern recognition software will be implemented in order to determine whether any unforeseen deviation occurs in a prisoner’s regular movement pattern which could be an indication of a potential escape attempt or adverse action (i.e. attempting to kill another prisoner).
- The system must be able to hold a record of a prisoner’s movements for up to a month to ensure proper pattern recognition can be implemented.
Yard Activity Monitoring
Prisoners are allowed to go out into prison yard every few days for exercise, however, such instances often result in violence in between members of opposite gangs. To prevent such an issue, it is necessary to monitor prisoners who are affiliated with rival gangs and implement a tagging system so that the prison guards know when to schedule activities to prevent and adverse associations.
Server Backup
Due to the possibility of power failure, system error, hardware malfunction or any other possible problems that could affect the integrity of the data collected, the information that has been collected by the server will be backed up to an online cloud based network so as to ensure data integrity.
Solution Overview
Solution Introduction
It is the vision of Silent Hill Inc. that a prison system can be created wherein prisoners can be tracked at all times, where their actions can be monitored and restricted without direct human intervention and, as a result, create a more cost effective and efficient prison system. In order to achieve such a goal, new applications to present day technologies were taken into consideration with the Identchip system coming out as a result of exhaustive research and testing. Overall, the tracking system can be broken down into two specific sections, namely: the functional components of the project and its system components. The functional components represent the physical processes that go into enabling the tracking system to meet its goals while the system components refer to the technology that was utilized in order to get it running in the first place.
Solution High Level Description
Functional Components Overview
There are 3 functional components utilized in the Identchip tracking system, these are composed of the Prison Registration Center, the RFID Chip Implantation Center, the Cells and Prison Facilities. Together, these functional components were as a means of enabling the use of the Identchip as well as tracking and restricting the movements of the prisoners.
Prison Registration Center
The purpose of the prison registration center is to create the inmate designation profile that will be correlated with the RFID chip that will be implanted into the prisoner. The center will act as the initial drop off point for new prisoners before they are allowed to join the general population. Their picture will be taken as well as any relevant information (criminal, medical or otherwise) will be placed into a designated chip frequency code. The registration center will serve as the place where prisoners will be processed and sorted according to the degree of their crime (i.e. life imprisonment, 10 years, 5 years etc.) and their block and cell assignment will be given to them. Prior to being admitted into the medical chip implantation center, all prisoners will be examined for any hidden weapons and will be briefed that they will be given an RFID chip in the next center which will be utilized to track all their movements while they are inside the prison. This should deter them performing adverse activities (such as escape from the prison) when they know that they are being monitored at all times.
RFID Chip Implantation Center
The RFID chip implantation center will act as the location where the RFID Identchip will be inserted into the prisoner. The chip, no larger than a grain of rice, will be inserted into the prisoners via an injection which they will be informed of beforehand. The frequency number of the chip will be tagged to the prisoner’s newly created account resulting in an immediate registration within the system. A preliminary scan using a handheld scanner will be done to make sure that the chip is functioning properly after which the prisoner will be introduced into the general population.
Note: Taking into consideration the fact that there are already prisoners within the Australian prison system; the process that has been described will be revised to a certain degree wherein the prisoners will be informed that they will be given a chip that will be inserted in their bodies upon which the Identchip will be inserted into their bodies.
Cells and Prison Facilities
The cells and prison facilities will act as the primary method of controlling and limiting the movements of the prisoners. In combination with the normal bars, walls and guards that ensure prisoners stay within the facility, RFID readers and scanners will be scattered around the facility. Access to particular areas will be limited to people having the correct RFID frequency. This will result in limited access to prisoners resulting in fewer human guards needed in order to contain and control inmates.
System Components Overview
After going over the functional components of the system, the following details the system components that will be needed in order to implement the necessary services. In examining what particular components to utilize, it was determined that repurposing present day technology in order to serve the needs of prisoner tracking was more effective than simply trying to create the technology on our own. While this paper will delve into much greater detail on how each component operates in the systems components section of this paper, the following acts as a brief description to help introduce readers into their different functions.
Identchip Tracker
The Identchip tracker acts as the primary component of the system since it is the primary means by which prisoners will be tacked. Each chip will emit a unique identifying frequency that will enable immediate identification once a prisoner passes through a reader or is scanned by a handheld scanner. Since the Identchips are placed within the prisoners themselves, this prevents their removal without obvious tampering and enables a method of 24 hour surveillance no matter which section of the prison they go to.
Silent Hill Inc. believes that this method of prisoner tracking would stand out from the crowd of current methods of inmate surveillance since it does not rely on external means of charging (the chip can be activated via and RFID signal) and the fact that it does not require extensive amounts of personnel in order for it to be effectively implemented.
Identchip Scanners
Identchip scanners will come in the form of wall mounted or floor level scanners that constantly scan people that pass through them for the identifying signal that is unique to each Identchip. To save on costs, these scanners will only be present in critical juncture areas that prisoners have to pass through in order to get from one part of prison block to another. Other applications of the scanner technology come in the form of door based scanners that are cued to a specific RFID signal on a prisoner’s chip to grant access or the handheld scanners that will be given to guards to allow immediate identification via targeting a specific prisoner in a crowd.
Servers
After examining various examples which dealt with the various aspects of RFID tracking and scanning, it was noted by the researcher that the processes behind the tracking system were not that intricate after all. This was due to the fact that the program would basically work through an expanded “If-Then-Else” program range. This means that if a person possessed the correct RFID frequency they would be granted access to a section of the facility. Also, recording the movements of prisoners would be as simple as taking note of it in a log book and searching for patterns of movements. It is based on this that two separate server systems will be utilized. The first system will deal with logging movement and tracking patterns while the second system will focus on preventing and granting access to particular areas of the facility. By separating the system into two servers, this ensures that failure in one system will not carry over into the other.
Network
A WLAN connection will be necessary in order to transmit the data from the readers to the server. Utilizing a secure localized Wi-Fi network, the readers will transmit the data they receive in real time to the system in which the needed tracking and authorization software will immediately analyze the data and perform the necessary function. Do note that a Wi-Fi network was chosen for this method of data transmission due to the need to minimize the availability of cables, wires, etc. to the general prison population.
Data Storage
Given the limited amount of prisoners within each prison, a large storage capacity will not be necessary, however, the server will include a Network Attached Storage (NAS) device to house the data collected regarding inmate movement activity after which the information within will be purged after the one month period is over to make way for new data.
Future Enhancements and Value Added Components
Future Enhancements
The limitations of the RFID chip will be detailed in this section and will showcase how its use in the system does come with a few vulnerabilities with the necessity of future enhancements in the form of RFID readers with a longer signal reach or RFID chips that emit a stronger signal
Lack of direct access
One of the main problems with utilizing the Identchip as compared to external tracking devices is the fact that there is no direct physical access between the chip and those monitoring it. This means that if the chip malfunctions the ability of the system to track the prisoner would cease. In order to get it back up and running again, it would be necessary to inject another RFID chip into the prisoner which could cause problems. Taking this into consideration, the lack of direct access and the inability for the chip to be replaced is a serious flaw in the system that needs to be taken into consideration during the implementation process. One way of preventing future problems would be to place multiple chips into other areas of the prisoner.
Lack of sufficient range
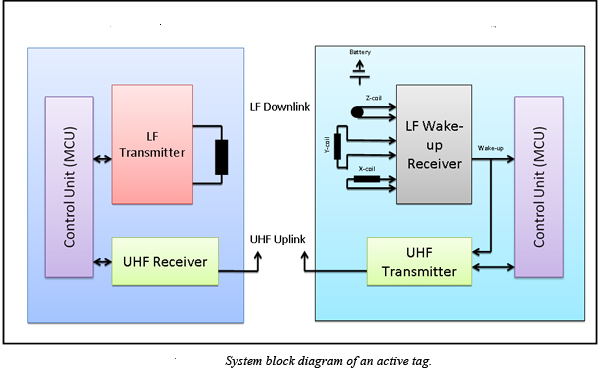
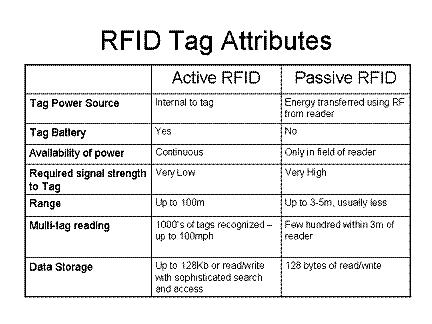
Another issue that needs to be taken into consideration is the lack of sufficient range on the Identchip. Given its limited transmission capability, the RFID chip is only capable of transmitting up to a maximum of 5 meters which severely limits the capacity of the system to effectively track prisoners after a certain distance between them and the tracker has been reached. Do note though that this is not an inherent limit of the RFID tracking system in general, rather issue is primarily due to the passive RFID chip that was selected as the primary tracking component of the Identchip system. Active RFID tags with their own independent power source (i.e. an internal battery, circuit, etc.) are capable of interacting with readers at a much great distance with active RFID tags that can be tracked up to 100 meters or more. Unfortunately, passive systems are utilized in the case of this project given the need to insert the tracking mechanism directly into prisoners thereby preventing them from removing the chips without causing significant physical harm by literally cutting open their hand in order to get it.
As seen in the illustration below, the range of the scanners is highlighted in blue and showcases how large areas of the prison can potentially result in a prisoner going untracked for a significant period of time. Areas where this can occur are the prison yard, exercise area and cafeteria wherein the large size can work against the ability of the reader and chips to sufficiently interact with one another.
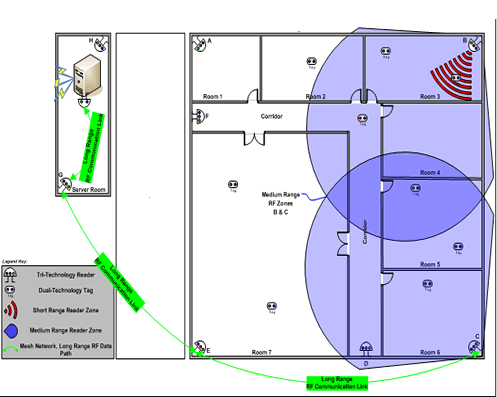
Scalability of Solution
While at the present the technology does not exist, in the future it may be possible to devise a passive RFID chip that can emit a signal that is larger than 5 meters in range. The same can be said for RFID readers with a much better range as compared to those currently utilized in this project.
Network
Requirements Analysis – Network
The Identchip scanners act as the primary means by which the prison system will be able to track the movements of prisoners. These wall mounted readers will be placed in several strategic locations to ensure sufficient coverage over most of the prison facilities.
Network Overview and Design
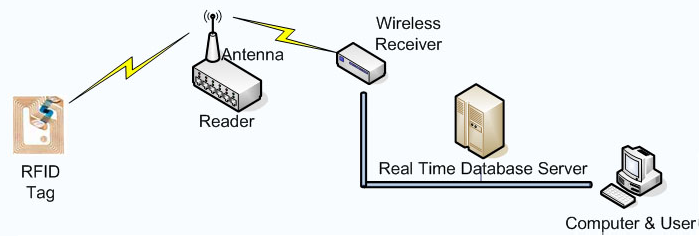
- ARPT System – the proposed system that will be utilized in this project uses the ARPT system (Active Reader, Passive Tag) wherein the readers that are placed along the walls of the prison send out what can be defined as an “interrogator signal” to the various tags within its immediate vicinity. Since prisoners are equipped with a passive tag system (due to the lack of a sufficiently powerful active power source), this means that the entire detection process is dependent on the range of the tag to the reader since the tags themselves lack the capacity to constantly send out an authentication reply.
- Use of wireless receivers for data transmission– Due to the necessity of preventing the loss of data integrity within the system due potential tampering (i.e. damage to the transmission wires due to the activities of prisoners), the system utilizes a system of wireless receivers and transmitters in order to exchange information from the reader to the database of the prison. Through the implementation of such a system, this helps to limit the potential for tampering while at the same time increases the ability of the system to transmit from a variety of locations without having to rely on an extensive collection of wires and cables to exchange information with the main server.
Physical Infrastructure
Process
Based on the RFID transmitter schematic shown above, the following is an example of the process that would be implemented when a prisoner who has the Identchip embedded in their right arm proceeds through a hallway with RFID readers. This section is meant to depict a step by step process of how the RFID tag interacts with the general environment, how it is queried, how the information is sent and how it results in movement restriction throughout the prison compound.
Prison Registration Center
With the idea of creating a more efficient means of prisoner tracking and registration, Silent Hill Inc. developed the idea of creating a registration office that will act as the point of first contact between a the prisoner and the Identchip tracking system. The registration center helps to alleviate the issue of creating proper tracking records by creating a means by which prisoners can be easily registered into the system via an “assembly line” that allows a more efficient means of tagging. What must be understood is that the idea behind the creation of a registration center was in part a result of attempting to determine how prisoners can be properly “tagged” without them removing the devices. Not only that, there are issues with creating individual records and associating them with an RFID tag without the prisoners actually being there. One of the potential problems that might arise from such a practice is incorrect record tagging wherein the wrong RFID tag will be associated with the wrong prisoner. Since a prisoner’s medical records and prison file are associated with the unique RFID tag that is placed in them, should the wrong tag be inserted, this can create problems in terms of proper identification and tracking. To avoid such an issue, the idea for the registration center came about where the RFID tracking chips can be immediately inserted after a prisoner’s record has been created.
Process
When prisoners arrive at the registration center the following processes will be implemented in order to fill out their prison record.
- Fingerprint scan. Prisoners will be required to provide a finger scan for the purpose if identification and evidence in case any “incidents” (i.e. theft, murders, etc.) occur within the prison grounds where they are suspected of having a hand in.
- Picture ID. After getting their fingerprints, prisoners will also be required to sit for a photo ID that will be part of their prison records. This is a necessary requirement given the need for immediate visual identification during tracking as well as being able to compare the RFID identity tag with the face of the prisoner.
- DNA records. Aside from getting a fingerprint scan and picture ID, it would also be necessary for the prison to collect a DNA sample from the prisoner. This is to create another level of identification so as to ensure that in the event of a natural disaster, fire, or other calamity that might result in the death of prisoners, records would exist that would enable proper identification. It should also be noted that the ability of the Identchip to tracking prisoners is limited to the confines of the prison itself. Should a breakout occur, proper DNA records would be necessary in order to re-identify escaped prisoners who may have altered their appearance.
- File Creation. Once the processes that have been described above have been completed, the registration center will create a record of the prisoner which will include their name, prison sentence, cell block, and crime. This record will be associated with the unique RFID tag that will be placed on the chip and associated with that prisoner’s records.
RFID Chip Implantation Center
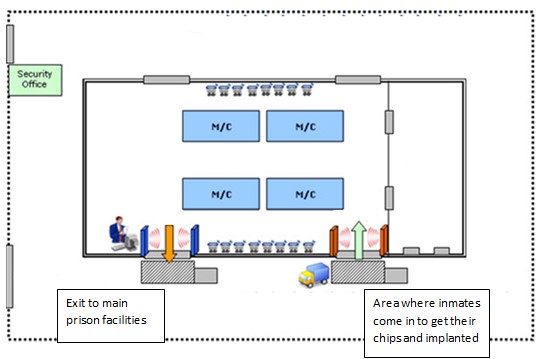
Introduction
As seen in the chart above, the RFID implantation center has 4 specific areas where prisoners will be processed and implanted with the RFID chip.
- Information station. In this section, the prisoners will be given a short orientation regarding the purpose of the injection. They will be told that it is an RFID shot that is meant to help control their movements within the prison. The injection will contain the RFID chip meant to track the movements of the prisoners.
- Injection station. In this section, prisoners will be injected with a coded RFID chip into their right hand. The coded frequency of the injected chip is unique to that chip alone and will allow immediate identification of the prisoner.

- Testing Station. Under the premise of performing a short x-ray of the prisoner’s chest to look for any abnormalities, the nurse at the station will examine if the RFID chip is working properly by performing a cursory scan of the prisoner. Should the scan work properly and the prisoner properly identified, the individual in question will be escorted to the orientation section of the implantation center.
- Orientation Section. In the orientation section of the implantation center, prisoners will be given waterproof wrist bands with a random set of numbers and a barcode imprinted on the band. The prisoners will be told that the wristband and the numbers placed on it will act as their “keys” within the prison which enable them to access their cells, get food and enter other parts of the prison facility. In reality, the barcodes on the wristbands are actually useless in that it is actually the RFID chip placed inside their right hand that acts as the actual “key”. The wristbands are merely to give the impression that they are what the prison is being used to access the cells of the prisoners when in reality it is actually the chips that were placed into their hands.
Cells
Introduction
Tracking and limiting the movements of prisoners begins in their cells where they will spend a vast majority of their time in prison. This section will show how the RFID reader and tracker are utilized to isolate prisoners into specific cells and prevents other prisoners from entering into the cell with them (unless in cases where there is more than one prisoner assigned to a particular cell).
Sensor
As seen in the example above, each cell comes with an RFID reader that is located on the wall right next to the entrance. In order to enter their cells, prisoners are going to be told to raise their wrists to the scanner in order to get inside so that the wristband they were given can be read. In reality, what is being read is actually the RFID chip that has been inserted into their skin.
Functions and Process
- Interaction between reader and system. The interaction between the reader and system is actually pretty straightforward. Once the prisoner raises their hand and the RFID chip in their hand is read, a query is immediately sent to the server that handles authorization for cell block assignments. It will compare the RFID signal from the chip to the assigned RFID designation for that particular cell and will grant access should a match be confirmed. In cases where a match is not confirmed, a beeping sound will alert a prisoner to the fact that they cannot enter the cell since they do not have the proper RFID access frequency.
Aside from this, an alert will be created within the system and logged into the prisoner’s movement records. While an initial failed entry does not warrant immediate intervention from the guards, repeated attempts to access the cell will create a secondary alert that will appear on the monitors in the control room that will warrant a visual inspection via video cameras to determine whether direct intervention by prison guards is necessary.
- Interaction between reader and cell door. The interaction between the reader and the cell door is on a very limited capacity wherein all that is needed is confirmation from the system that the correct RFID frequency is on the prisoner’s hand for it to be opened. Do note that the gap that allows prisoners into the cell is quite small (big enough for a single prisoner to get through but far too small for multiple individuals) there are sensors located on the top of each prison cell door that confirms whether a person has entered or exited the cell. Once the motions sensors have confirmed that a single person has entered, the prison cell doors will immediately close. However, this particular aspect of the system and the necessary RFID function to open the door can be overridden by the control room during instances where an inspection of the prisoner’s cell fro banned substances is conducted.
- Limitation on the number of prisoners per cell.The necessity of limiting the number of prisoners per cell is due to incidents where cellmates have attempted to injure one another due to a variety of possible disputes. By limiting the number of prisoners per cell to one or two, this decreases the potential for the number of cell related incidents that may occur. It also makes it far easier to track prisoners by limiting the number of prisoners per cell.
Cell Block Access and Monitoring
Introduction
This section details how inmates will be tracked and monitored while they are outside of their cells and are accessing various parts of the prison. It will showcase how the monitoring devices interact with the prisoners and how access is granted or denied in specific scenarios.
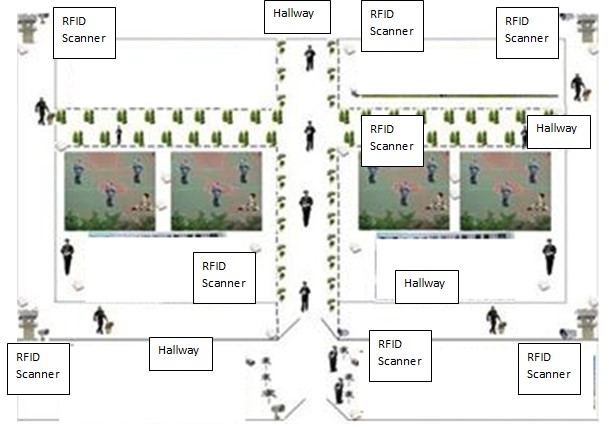
As it can be seen in the example above, the RFID tracker in the corridors and various areas of the prison are wall mounted and placed out of the reach of the prisoners. They continuously send out a query to the various tags which tend respond via a signal they emit which helps to distinguish one tag from another. By placing each reader in various corridors of the prison that a prison has to go through, the system is thus able to track their movements in real time via continuous log data regarding places where the RFID trackers have mapped their movement.
Limitations to the System
Do note though that the scanning system does come with significant limitations that need to be taken into consideration. The first of these limitations is the limited scanning range. While active RFID tags, such as those in various cars, have their own battery power and can thus release a more powerful signal, the passive RFID chip based on Verichip technology has a limited transmission range with a maximum of 5 meters. While it is superior to certain extent to other passive RFID chips in that it can be self-powered via the body heat of the prisoner, the fact remains that the necessity of its small size limits its capacity to broadcast a signal. Taking this into consideration, most corridors and prison areas will either need to be interspaced with wall mounted readers every 15 meters (a daunting and expensive solution) or readers should just be placed in areas which are unavoidable (i.e. junctions in prisons that are in between the various cell blocks). After careful evaluation of the choices and budgetary limitations that are sure to arise, it is the recommendation of Silent Hill Inc. that the latter solution be advocated instead of the former given that the natural barriers and corridors that have been built into the prison design should act as a satisfactory means of enabling better prisoner control.
Functions and Process
- Tracking. Tracking utilizing the corridor based readers occurs through a “logging” mechanism instead of in real time. The inherent issue with real time tracking is that it would require a far larger tracker than the RFID chip since the components would need to be more complex. The various micro trackers that are often seen in movies, cartoons and television shows are actually fictitious in nature given that an effective real time tracking mechanism would need to be able to emit a far stronger signal. Such devices, while available, are often half the size of a standard mobile phone and inserting them into prisoners without them realizing it would of course be difficult. It is based on this that each time a prisoner passes by a scanner within a corridor, their location is immediately logged into the system which will have indicate the precise time, location and date of movement. Such a means of tracking can be considered appropriate within the context of the prison due to the limited amount of locations that a prisoner will be capable of going.
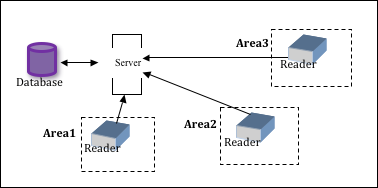
Design
As seen in the diagram provided, the design of the system is pretty straightforward. Once an inmate approaches the range of the reader, their RFID chip is scanned and is unique identifying marker is searched for within the system. Once the system matches the identifying market on the chip with the one in the system, the movement of that prisoner is logged within the server and then placed into a map grid that is unique to that particular prisoner. When queried regarding the movement of a particular prisoner, two windows will appear: one will show the log history of the prisoner’s movements while the other will show a virtual representation of the movement of the prisoner based on his/her logged movement within the prison. Through this system, every area that a prisoner goes to, their movement patterns, habits and other information related to their normal times of entering and exiting a particular part of the prison can be tracked. This can be invaluable in determining whether they are actively trying to escape by being in areas that they are not supposed to be in or if they were guilty of a murder within the prison (which at times does happen) by being in a particular area when it occurred.
Identchip Tracker
Introduction
This section will detail how the RFID “Identchip” will function, the justification for placement in the right hand of the inmate, its interaction with the readers and the inherent limitations of the technology.

Functionality and Process
- Construction. The RFID Identchip, given its size, has two main components: its integrated circuit which is used for storing and processing information (i.e. the RF signal that is being broadcasted by the readers) and the antenna that is used for receiving and transmitting signals to and from the reader. Combined, these two parts act as the means by which the Identchip is able to function without the use of other extensive components. An example of the Identchip can be seen below and showcases the individual parts of the chip.

- How information on the chip is queried. Information on an RFID Identchip is queried via an RFID reader sending an encoded signal to the chip. Once the RFID chip receives the query from the reader, it responds to the signal with its identification number, tag designation, etc. and other relevant information that is on the chip. Do note that with present day technology the total amount of information that can be stored on the Identchip is limited to 128 bits. As such, this limits the capabilities of the tracking system to add more extensive identifying information onto the chip. Thus, the only means of tracking within the system itself is via a set of serial numbers which are then associated with the prisoner’s prison file and medical history.
- Placing the serial number on the tag. There are actually two methods by which the RFID Identchip can acquire its serial number which is then assigned to the database The first method is that assigned serial number transmitted by the tag can be assigned within the factory that created it or the tag can have read/write capabilities wherein specific data within the chip itself can be included via a special encoder. For the purpose of this project, the latter method has been chosen due to the possible problems that may occur should an error occur in the factor and repetitive serial numbers are used in the tag. By having the numbers assigned within the prison itself, this adds an extra level of security in ensuring that there will not be issues of mistaken identity when tracking the movements of a prisoner.
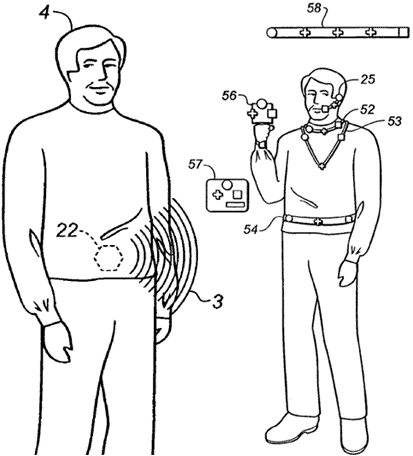
The following is an illustration of the various areas on the body where Silent Hill Inc. considered placing the RFID chip. While each section had its merits such as areas 52, 53 and 25, it was decided that area 56 would be the best choice. The reason behind this choice was connected to the fact that injecting a chip into the hand would be less intrusive as compared to placing it into other areas of the body. Furthermore, by placing it into the right hand of the prisoner this lessens that amount of discomfort connected to the presence of the chip since the prisoners were informed that they are being tracked by the chip, however, it still needs to be removed later on and placing it in a hard to reach location could cause problems during the procedure.
Before proceeding, it is important to note that there are two RFID scanners that are utilized in this project, the active and passive scanners.
- Active Scanners – these are the scanners that are utilized in the various doorways, entrances and other blocked off areas within the prison that require a prisoner to actively identify themselves to the system before they are allowed to pass through the doorway.

- Passive Scanners – these are the scanners that continuously track the prisoners through the various facilities they enter and log their location within the system.

Frequency: 920-925MHz (902-928MHz American Standard)
- Protocols: ISO18000-6B, ISO18000-6C (EPC GEN2)
- RF transmitted power: 0-30dBm (configurable)
- Reading distance: 1m to 25m
The reason why there is a separation between the scanner systems instead of one entire passive system that grants access based on how close a prisoner is to a particular doorway, is due to the logistical and security issues that would come about with such a system design. Simplifying the system into two separate components that monitors and grants access lessens that logistical burden and allows the prison system to utilize far less server capacity as compared to a system that both tracks and monitors at the same time. There are also issues related to the potential that should another prisoner stand close enough to someone else when one door opens, they would be able to gain access when they should not be able to do so.
Process Stages
Initial Stage of the Process
The initial stage of the process involves a prisoner walking down a corridor with a relatively innert RFID chip. As explained earlier, since this project utilizes a passive RFID medical grade chip, it does not actively transmit a signal and is only capable of transmitting once it comes into contact with an instigating query from an RFID reader. In this particular stage the prisoner is for all intents and purposes “absent” from the system since they have yet to be detected and “logged in”.
Detection by the System
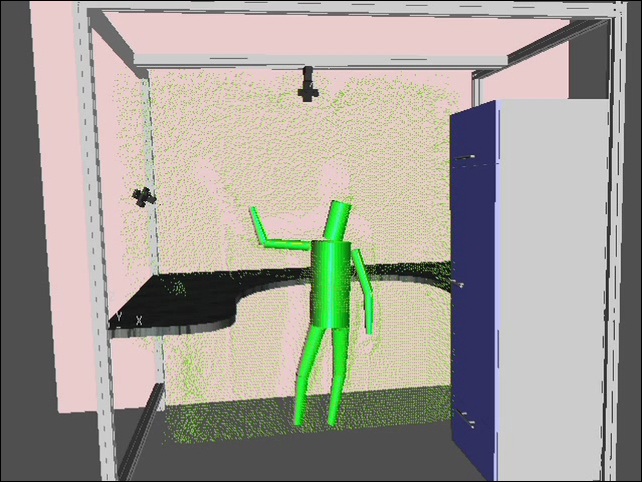
In the illustration above, the “green spray” seen enveloping the character in the photo represents the interrogator signal sent by the RFID readers within the prison hallways. Detection in the hallway system occurs when the signals sent out by the RFID reader encounter an RFID chip. The interrogator signal basically acts as pulse that activates the antenna in the chip that causes the microchip inside to relay its information back through the antenna and towards the RFID reader. It is normally the case that the information provided consists of the chip’s serial number which is utilized as the primary means of identification.
System Information Transmission
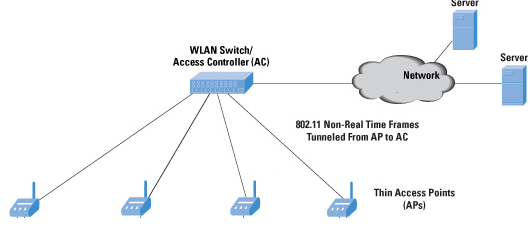
The transmission of information within the system utilizes a WLAN in order to avoid having the use of extensive wiring within the prison complex. As soon as the RFID readers have sent out a signal and received a response to a query from an RFID chip, the serial number that was sent is sent to the access point of the RFID reader after which it is sent to the WLAN Switch access controller. It is at this point that it is sent directly to the servers which then authenticate the serial number via an examination of the prison records. Once a match has been found, the date, time and area information is placed in log which enables the prison officials to examine the location of the prisoner at any given time of the day.
System Log Creation
After the data from the wireless transmitters has been sent to the server, a system log is created which details the movement of the prisoner. An example of this can be seen below:
As explained earlier due to the limitations of the system, real time assessment of the prisoner’s location is not possible given the need for active RFID tagging when passive tagging is utilized. To get around this dilemma, each time a prisoner enters into the range of scanner the system create a log which then is translated by the software into progressive locality estimation. Progressive locality estimation refers to the software determining where a prisoner is at any one time based on the rate of system log ins that they have go through within particular sections of the prison.
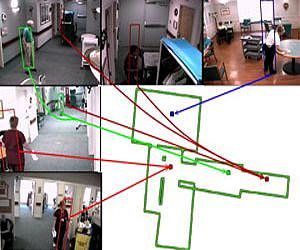
An example of this can be seen in the illustration below using some volunteers for the project:

As you can see, each movement of the “prisoner” (i.e. a volunteer in this case) is represented as a series of dots on the street yet when they are combined they become a variable movement pattern into a certain direction. By utilizing the system logs as “dots” on an overlay of a prison map (as seen in the example below), a tracking line can be created and represented on the system screen which helps to track the movement of prisoners throughout the various facilities they enter and exit.
While Silent Hill Inc. acknowledges the fact the real time tracking via the use of larger leg transponders would be more effective in terms of knowing the precise position of a prisoner, the fact remains that they are far too cumbersome and susceptible to tampering. Not only that, they require a constant recharge which may not be possible to monitor effectively within a prison environment, it is based on this that the Identchip developed by the company presents itself as a far more viable option.
Going back to the topic of log creation, the example bellow illustrates how an ordinary log is created in the system:
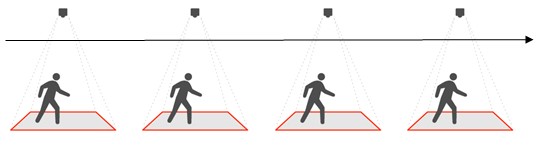
As a prisoner enters into the range of detector one, system log one is created, as prisoner enters the range of detector two, system log two is created. This process continues throughout the movement of the prisoner within the system until they return back to their room. Basically, a log is created when a prisoner exits the range of one detector and enters into the range of another. While there are discrepancies to this system, such as a prisoner remaining in between two sensors and thus remaining undetected, the fact remains that by positioning the readers in critical juncture areas, even if a prisoner did not move, they could still be tracked to their present location based on the last system log that was created.
Network Security
The configuration guidelines for external data communication in the case of this project focus on a completely secure WLAN connection with no direct access to the internet. The reasoning behind this configuration is the fact that the best way to ensure protection from hackers is to keep the system independent from the internet and thus unreachable. The only other method by which the system could be penetrated is via an internal device connecting to the network and attempting to take over the system or insert some form of malicious code.
Physical Security
Read/Write Capacity of RFID Chips
There are currently two types of RFID chips that can be used in humans, these are the read only RFID chips and the read/write RFID chips. The read only RFID, as their namesake indicates, can only be read by scanners and cannot be edited in any way by an external device. These are the most secure type of RFID device since they prevent numerous forms of external tampering. The second set of RFID medical grade chips are the read/write chips which, as their name suggests, can be both read and written onto by an external device. Ordinarily, a read only chip would be the most suitable for use in the case of the RFID tracking of people, however, issues related to proper record keeping and creating a more “unique” system of serial numbers more suitable to sequentially track prisoners requires the need for read/write RFID chips. This of course introduces the potential that the chips themselves could be potentially overwritten. However, while there is the very real potential for this happening, the fact remains that tampering with the chip by physically removing it from the body in order for it to be overwritten (RFID chips need to be in contact with “leads” inside a writer in order for its serial data to be overwritten) would become immediately obvious as seen in the picture below.

Other methods of tampering come in the form of an external reader/writer that has the capacity to overwrite the chip information without the chip being inserted physically into the reader. However, due to advances in RFID technology, newer RFID chips now have a “locking” mechanism that prevents external data overwrites. Physically rewriting the content in the chip is possible, however, as seen in the example above it would require the removal of the chip in its entirety.
Logical Security
While prisoners have limited access to technology, it is not inconceivable to think that one day they may discover the presence of the RFID chips and try to implement some way of altering them or causing them to malfunction thereby “masking” their presence from the automated scanning systems within the prison. In order to preserve the integrity of the data within the chip, the following security mechanisms have been developed in order to determine whether tampering has occurred:
- Passive Authentication (PA) – use of database queries to determine the last sighting of a chip in a designated area
- Utilizing the daily “log ins” (i.e. Identchip notifications) of prisoners within the database, the system will determine whether a system log in is excessively late within the day or has not been done at all. A missing log in time based on that prisoner’s monthly habits is indicative of a tampered of malfunctioning chip and, as such, an alert will be created by the system to the control room to inform guards that a prisoner has not logged in to the system within an appropriate amount of time. These alerts can be set to either morning or evening and will act as a means of immediately determining whether a chip has malfunctioned within the confines of the prisoner’s cell or within the prison itself. Once the prisoner has been identified, a sweep will be conducted to determine where the prisoner was last seen and an immediate examination of the chip will be conducted.
- Active Authentication (AA) – routine inspection of guards of prisoners prior to entering certain sectors of the prison to determine whether the chips are working
- Active authentication involves the prison guards utilizing hand held scanners at various areas in the prison to conduct a routine examination of the wrist bands given to the prisoners when in reality they are checking whether the chips are working properly or have been tampered with. An investigation can be conducted in a quick and simple manner by the guards merely using the hand held scanners to send a query to the system regarding the status of an implanted chip. This query can contain data related to the authenticity of the serial number associated with the card and whether the picture in the prisoner database matches the appearance of the prisoner. This method of active authentication helps to prevent prisoners from making it appear that their RFID is working when in reality it is not.
- Database Redundancy Control (DRC) – scanning of chips to determine whether numerals have been changed based on active presence of prisoner identity within the database.
- Database redundancy controls is an automated feature within the RFID scanning system which examines whether an RFID chip has been tampered with via serial number identification. Similar to the Active Authentication system, the DRC acts more as a passive system that does not require direct human assistance in order to examine the state of a chip. In cases where an RFID chip is detected by the scanner and a query is sent to the chip, the lack of a sufficient authentic response that matches a profile in the database will warrant an immediate investigation in order to determine the cause. This comes in the form of the system alerting the control room which will then alert nearby guards to search the area for a prisoner with a chip that has been identified as being tampered with.
Limitations of the RFID Chip for Security
Due its small size and limited capacity for any form of effective processing, the Identchip lacks the means to perform complex or even simple methods of self-diagnostics. As a result, it is incapable of determining whether it has been tampered with and relies almost entirely on outside examination to investigate and possible anomalies. It should also be noted that various studies have shown that a sufficient enough electrical charge from an outside source could “fry” the simple system of an RFID chip which can result in either data erasure or the chip being rendered permanently inoperable. There are no solutions to these limitations and, as such, they need to be taken into consideration when designing the various protocols related to the access of prisoners to the needed equipment that would manifest such issues.
Hardware
Hardware Overview

The SDiD can be described as a Radio Frequency Identification (RFID) Secure Digital (SD) Card, which can be placed into the SD slot of a laptop, reader or basically any device that has a compatible SD adaptable slot. The reason the SDiD is being utilized in this project is due to the fact that it offers RFID read / write capabilities at the fraction of the price normally associated with purchasing a factory grade RFID encoder. Some of the applications of the writer include, but are not limited to, reading and writing RFID tags that are within a close proximity to the reader and do not have write protection enabled on them. SDiD will be utilized in this project as a seamless management solution for real-time RFID identification and labeling within the registration area of the prison. The serial number that will be generated for the tag will be written by the SDiD on to the RFID chip at which point in will be placed into the prisoner in the insertion center. Do note that the RFID tag information generated by the SDiD can be communicated in real-time to the tracking database through the RFID readers that will be placed in various strategic locations throughout the prison.
The following are the specifications and price of the SDiD
Radio Frequency Identification (RFID):
- ISO 15693 compliant
- ISO 14443A compliant
- Supports NXP I-CODE®
- Supports NXP I-CODE® SLI
- Supports NXP MIFARE®
- Supports NXP MIFARE DESFire®
- Supports Texas Instrument Tag-it™ HF-I
- Read, write and search RFID tags
Price: $150 (x4).

While this would normally be placed in the software section of this project, placing the development kit here was more appropriate given its association with the SDiD reader/writer. This development kit basically acts as the primary method by which the information from the RFID chips and readers are interpreted by the system and created into system logs.
The Software Development Kit (SDK) comes with the following applications to help launch the needed application for the prison:
- Binaries
- Header files
- Drivers
- Demo applications (for comparing the usability of the developed program for the logs)
- Sample applications with the full source code which would be necessary to help in the development process for the log program needed by the prison.
Overall, it can be stated that the development kit delivers a great Application Programming Interface (API) which helps to simplify the development process that can be used in this project. This can greatly enhance the speed that a programmer can familiarize himself with the technology
Price: $300.

With the necessity for efficiency in processing the information from the RFID readers, the project team chose the Lenovo ThinkServer RD630 2594-A3U Rack Server as the main server to be utilized for the Identchip tracking system.
The following are the features of the system:
- Enhanced manageability tools and scalability that would enable the prison to upgrade the system should it need more server capacity due to an increase in the prison population
- .The server features an Intel Xeon E5-2660 2.2GHz Processor and 16GB of DDR3 memory which supposedly delivers superior system performance which will be needed given the sheer amount of location logs and tracking that will be conducted.
- It comes with 8x Hot-Swap Bays which the project team can utilize in order to install up to 8 hard drives for optimized data management of the prison data.
Price: $1,649 (x3).

The TS140 Thinkserver will act as the secondary server that primarily deals with the access requirements of prison doors and other locations within the prison. While it runs on the same network as the rack server, the TS140 will not be connected to the RFID readers, nor will it take part in the passive method of RFID tracking. Its primary concern will be granting access via active recognition in the system via the touchpads that will be utilized as the main interface.
The following are the main components and features of the system:
- Processor: Intel® CoreTM i7-4770 Quad Core Processor (8M Cache, 3.40GHz – 3.90GHz) 84W
- RAM: 32GB (4x8GB) DDR3 1600MHz | Hard Drive: 3 x 3TB 7200rpm HDD in RAID 5
Price: $1,411.

The Iomega Storcenter can be considered one the best methods of network storage since it was built specifically for event logging and providing up-to-the-minute updates on the status of the various systems that are connected to it via the network. The following are the features of the device:
- SSD Support: For IO intensive applications, the px6-300d can be fitted with solid state drives to boost performance.
- RAID Support: RAID 1, 10, 5,and 6 with hot spare, automatic RAID rebuild and hot swap. RAID 0 and JBOD mode also available.
Price: $2,121.

With the various servers that will be in use at any given time, it would be necessary to balance the load from the RFID readers and scanners to ensure that they are not placed all into one server which would result in the very real possibility of a server crash due to an excessive influx of information. It is based on this that a load balancer is needed so as to prevent a server crash that could potentially bring down the entire system.
Features:
- Hardware load balancer appliance (single unit) – small, light and powerful Load balancing device :
- 3 million+ concurrent connections.
- 700 SSL TPS, great starter unit restricted to 16 servers 4 VIPs x 4 RIPs
Price: $1,995.

This is a router necessary for routing the information from the RFID readers to the necessary network servers.

In order to be able to accurately read and transmit information, the ideal RFID reader for this project is the LRA RFID reader. One of the advantages of utilizing this system is that the receiving and transmitting paths are separated and use different frequencies which helps to prevent mix ups when it comes to transmitting large amounts of data over a short period.
Some of its features include:
- Transmitting power which is between 100mW-500mW
- Multiple-protocols for a wide array of possible uses in the prison (which is important given the need for flexibility in the field)
- Fast response time when it comes to reading tags
- Multiple-tag reading (a needed feature given the various prisoners it has to detect within a short span of time)
- Lastly, it has a directional antenna and water-proof design which is useful since it may be placed in the prison yard to keep track of prisoners there.
Specification:
- Frequency: 920-925MHz (902-928MHz American Standard)
- • Protocols: ISO18000-6B, ISO18000-6C (EPC GEN2)
- • RF transmitted power: 0-30dBm (configurable)
- • Reading distance: 1m to 25m
Price: $900 (x50).

The RFID Identchip, given its size, has two main components: its integrated circuit which is used for storing and processing information (i.e. the RF signal that is being broadcasted by the readers) and the antenna that is used for receiving and transmitting signals to and from the reader. Combined, these two parts act as the means by which the Identchip is able to function without the use of other extensive components. Information on an RFID Identchip is queried via an RFID reader sending an encoded signal to the chip. Once the RFID chip receives the query from the reader, it responds to the signal with its identification number, tag designation, etc. and other relevant information that is on the chip. Do note that with present day technology the total amount of information that can be stored on the Identchip is limited to 128 bits. As such, this limits the capabilities of the tracking system to add more extensive identifying information onto the chip. Thus, the only means of tracking within the system itself is via a set of serial numbers which are then associated with the prisoner’s prison file and medical history.
- Each Identchip must link to a complete record of the prisoner via the serial number on the chip which entails their block number, cell assignment, list of prior offenses, level of danger, prior escape attempts and time till release. This is for guards to be able to immediately identify prisoners on sight without wasting time by checking on the prison’s information database.
- The Identchip must have its own unique identifying digital signature to allow handheld and wall mounted scanners to immediately distinguish prisoners. Such a feature is important given the need to distinguish who is who through the scanning process.
- The Identchip must have a corresponding facial match in the database that must be updated on a yearly basis for long term prison inmates. This is due to the various changes to a person’s physical appearance that may occur during incarceration (i.e. growing facial hair, getting thinner, fatter, etc.). Accurate visual identification is important for prison guards especially in cases where there are multiple prisoners in one area
Price: $5 per chip (x100).

The scanner based security door is a heavy duty prison door meant to withstand severe punishment from inmates. It has bullet proof glass, 2 inches of steel and is electronically controlled via the wall mounted system seen adjacent to it on the screen. This door is an effective means of controlling prison populations by limiting access to critical areas to only authorized personnel. Within the context of this study this security door will be utilized on all prison cells to prevent access by unauthorized prisoners and will also be utilized to limit their capacity to enter into select areas of the prison based on the RFID serial number on their tags. Aside from the RFID tags, the only other way to open these doors is via a manual override from the main control room. Manual overrides can also be utilized to lockdown certain doors resulting in RFID tags or any other method of identification being unusable to open them. This is a security feature meant to prevent prisoners from merely capturing an unfortunate guard and using his thumbprint to activate the door.
Price: $1,500 per door (x100).
Software
Software Overview

When it comes to managing the massive influx of log data that will be created by hundreds of prisoners being scanned by RFID readers at any given time, it is important for the system to have a certain “robustness” in its capacity to handle such loads while at the same time being capable of accomplishing other processes in an efficient manner. This is where Windows server 2012 enters the picture. It can be utilized by the project team to manage an entire network utilizing only a single server. As per the user guidelines of the software, the ability to manage and entire network through a single service helps to emulate the reliability and scalability of multiple servers at a lower cost which is a good thing considering the high costs of the project associated with the hardware that is necessary to monitor the prisoners. Other features come in the form of: a.) Automatic rerouting around storage , server, and network failures (useful when handling large data sets)
- Utilizing System Center 2012 R2, Windows Server 2012 R2 can provide an end-to-end software defined networking solution
- Other aspects of Windows Server 2012 is its capacity to help build scalable, high-performance systems which have highly available storage solutions using hardware that is pretty much standard in the industry. What this means is that Windows server 2012 is compatible with a wide range of hardware choices thus removing the possible limitations in hardware choices that a company would have originally had.
Another of the reasons why the Windows Management Framework was chosen as the primary server system instead of Linux is due to the fact that it provides a common platform for automation and integration which would help immensely when it come to automating the routine tasks of the Identchip tracking system with tools like Windows PowerShell.
Other aspects of the server which should help to simplify the process of deployment, comes in its ability to enable the project team (or the system manager) to manage the activities of the system across multiple servers through a single relevant dashboard in Server Manager. This helps to simplify the process resulting in a much easier method of managing the tracking network.
Price: $4.809

The following are the features that made the Microsoft SQL server the ideal choice when it comes to storing the necessary data within the system.
- The first feature that should be noted is its AlwaysOn Availability Groups–This particular feature which focuses on database mirroring enables users to fail over multiple databases in groups instead of individually which helps to track the failure while at the same time maintain data integrity since secondary copies will be readable, and can be used for database backups within the system.
- Another of the features that makes Microsoft SQL server 2012 an idea choice is Windows Server Core Support – This feature can be described as a GUI-less version of Windows that uses DOS and PowerShell for user interaction. While this does not seem like much at first, you have to note that this feature has a much lower footprint (50% less memory and disk space utilization as compared to other versions), and requires fewer patches than its previous iteration. Lastly, it is more secure as well which makes it an ideal choice for the tracking system.
- The last feature of SQL 2012 is its Enhanced Auditing Features-The advantage of this particular feature is that, users can now define custom audit specifications (i.e. instructions for examination) to write custom events into the audit log of their server. This new filtering features helps to give greater flexibility in choosing which events to write to the log which is invaluable in examining the current status of the server.
When taking all of the features that have been outlined so far, it can be seen that MS SQL 2012 can definitely streamline the development of the project and help to enhance reliability of the system so as to avoid problems in the future.
Price: $2,969.
Database
Requirements Analysis – Database & Data
Taking into consideration the fact that officials within the prison could potentially be dealing with some of the most violent criminals within the prison system, it would be necessary to ensure that the network has a certain “robustness” to it so that it can sufficiently support the capacity of the Identchip tracking system to determine the location of prisoners within the various facilities and to prevent them from getting into areas that they are not supposed to.
It is based on this that the network will require the following aspects in order to meet the needs of the Identchip system:
- Accuracy when tracking – when the system is tracking a prisoner in the various corridors of the prison, it would be necessary for a degree of accurateness to be done during the location log procedure. This entails that the network log accurately pinpointing the location of a prisoner at a given time and does not confuse them with any other person in the crowd. As seen in the illustration below, this entails being able to pinpoint a specific RFID tag serial number within the crowd of other serial numbers that enter and exit locations at any one time and focus solely on that person’s movement habits within the prison.

- Prompt Response Time – There should be minimal lag in between the period when an RFID tag is queried by a reader to the point that it is placed within the system log. While it is true that the Identchip system is not conducting a real time step by step tracking of the prisoner, the fact still remains that it is still necessary for the system to immediately update the tracking information of the prisoner whenever possible. A delay between the point of query to the moment it is placed in the system should only be a few minutes with a maximum allotted lag time of up to a minute depending on the degree of WLAN traffic at the time (i.e. when there are more than a hundred prisoners going through a particular area at any given time). A lag time of more than an hour is unacceptable since it creates an opportunity for the prisoner to implement some form of escape (i.e. hiding in a laundry truck, food delivery van or other means of exiting the facility).
- Availability of the Network– At any one point during its operation, the network should be able to work continuously and not be shut down for whatever reason. The reason behind this is quite simple, if the network were to shutdown this would entirely eliminate the capability of the prison officials to track and limit the movement of prisoners which could result in a mass escape or riot since it would be the RFID readers that are placed on the doors that limit the ability of prisoners to move. Should such a limitation be removed, it is very likely that prisoners that have been incarcerated in the prison for grievous crimes might escape en masse resulting in a hugely problematic situation for the Australian public. It is based on this that there must be system backups in place, both in the hardware and software side of things, to ensure that the network continues to function unabated.
- Scalability – Should the prison be expanded and more prisoners be added, it would be necessary for the network to be scalable so that it can handle the need for increased capacity.
- Verification – Lastly, the network must have a sufficiently capable verification process in place to ensure that it is tracking the correct prisoners and that it is granting access to areas only to people that should be there. This can be done by ensuring that there are multiple system redundancy programs in place that check the RFID serial number with the block and cell assignment of the prisoner.
Database Architecture
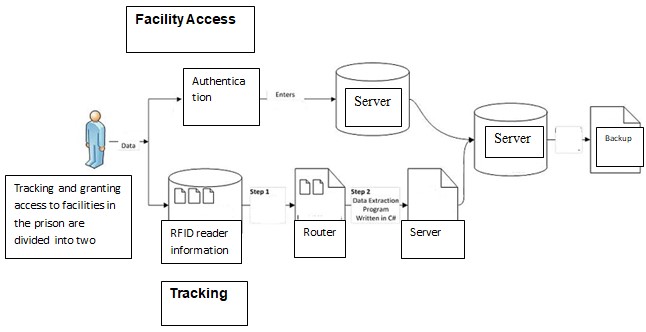
Data flow within the system is divided into two specific sections. In this system prisoners are classified as system “users” wherein they become the primary source of data within the system. There are two specific functions, facility access and tracking which are based on the actions of prisoners. The tracking system is pretty straightforward, information from the prisoner’s RFID chip is transmitted to the RFID readers after which it is transmitted to the system router and sent to its appropriate server. At this point, it appears as movement data on the control room interface after which it is sent to the backup server which tracks the long term movement of the prisoners. This system has no direct influence on the prisoner’s lives aside from tracking their movement. Limiting access to the various areas of the prison’s facility is handled by the facility access aspect of the system data flow. This aspect of the system works by comparing the RFID signal emitted by the RFID chips in the prisoners with their assigned facility designations in their prisoner profile. As a result, only prisoners with the appropriate serial number designation are granted access. Access is granted via the prisoners holding up their hands to the scanners that are located beside the prison access doors resulting in their RFID chip being read by the system. If the chip matches the serial number profiles that are allowed access, then the doors open and the prisoner is allowed inside. Should a prisoner attempt to gain access despite the fact that they are not assigned or allowed into that particular part of the facility, the scanner will emit a buzzing sound that indicates that they are not allowed in that part of the prison. At the same time an alert will be sent to the main control room indicating that an attempt at unauthorized access into a part of the prison was attempted.
DBMS
The database management software that will primarily be utilized is Microsoft server 2012. In conjunction with the RFID The SDiD™ 1020 Development Kit, the database will function similarly to what can be found in a majority of employee log creation networks which examine the time in which employees enter or exits the premises. The SDiD development software will expound on this through the use of a log that converts time and location data into a history of a prisoner’s movements. Thus, the development of an extensive database architecture is not needed in the case of this project given the limited actions necessary for the system to function.
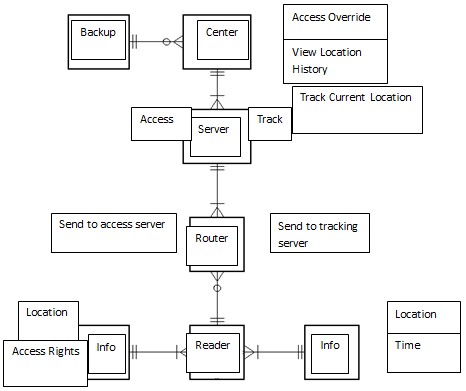
The following is an entity relationship diagram which details how the network operates and the various functions of its respective parts. The first phase of this system that is utilized is the ARPT system (Active Reader, Passive Tag) wherein the readers that are placed along the walls of the prison send out what can be defined as an “interrogator signal” to the various tags within its immediate vicinity. Since prisoners are equipped with a passive tag system (due to the lack of a sufficiently powerful active power source), this means that the entire detection process is dependent on the range of the tag to the reader since the tags themselves lack the capacity to constantly send out an authentication reply. The second aspect of the system involves the use of purposeful action on the part of prisoner to activate the sensor panels to enable them to access their cells and other parts of the facility. The servers act as points of tracking and confirmation of identity while the control room acts as the main point of access for overriding the commands in the server as well as seeing a graphical representation of the current location of the prisoner.
Data Integrity
When it comes to the integrity of the database, some of the issues that need to be taken into consideration are what may have happened to cause the issue, is it a software or hardware issue or is it a problem with the RFID chips. First and foremost the medical grade RFID chip was the chosen means of prisoner tracking for the RFID system since its simplicity actually gave it a degree of robustness in terms of being able to last for a long time without having to undergo significant levels of maintenance. Its size, no bigger than a grain of rice, is ideal in being implanted into prisoners without them being damaged and, as such, when it comes to data integrity issues the problem will normally be the result of a problem with the server. It is due to this that one of the possible solutions is the fact that only two specific operational servers will be active at any one time with the third being the fallback server should anything go wrong. As explained earlier, there will be one server system for prison tracking and the other for the RFID scanning using the prison doors. A third server could temporarily be utilized as a back up for both servers should something go wrong (software or equipment failure), however, this can affect the speed by which the server will be capable of reading all the data leading to lower performance outcomes.
Data Security
Limitation of Outside Access
To ensure strict data integrity and to prevent outside access into the system of the prison, a closed network system will be utilized in order to prevent any possible malicious hacking of the prison records which may result in altered serial number files. Various studies have revealed that the best method of protecting the integrity of a system from outside intrusion is to prevent the system from being accessed in the first place. Ordinarily this can come in the form of firewalls and multiple levels of passwords and security programs meant to deter outside connections, however, Denial of Service Attacks (DOAs) as well as various types of system exploits that have yet to be determined could be potentially utilized in order to access the prison records. This is of course unacceptable given the need to ensure that records remain untouched due to the possibility that the serial numbers associated with prisoner records could be randomized resulting in a worst case scenario where the RFID tracking system would be rendered useless. The best method of ensuring total and complete protection for the system is to eschew any form of cloud based operations and rely entirely on a localized server system that will handle the load of the various operations needed to keep the Identchip system running.
Backup and Recovery
Storage for the information collected by the RFID readers will primarily be accomplished by an Iomega StorCenter px6-300d Network Storage, 12TB 6-bay (6x2TB) device. A single Iomega Storcenter was determined as sufficient enough given the that the data from the RFID tracking are primarily text based and will not require that much room. However, as a precautionary measure the data stored that will be stored within the network storage device will be purged once a month to make way for new data. The reason behind this process is due to the fact that it would only be necessary to view a prisoner’s movement patterns for a month in order to determine whether he is habitually being in areas that he should not be. The system can just alert the control staff whether it occurs again and the proper sanctions be implemented. Not only that, given the methods of constraining a prisoner’s movements while incarcerated, a vast majority of the log would consist of normal habitual movements which are not needed by the system and could be considered nothing more than a waste of space. As for the process of updating data, this will primarily be handled by the Lenovo servers that will handle the prison identification records. This can be accomplished via an interface either in the prison registration center or in the main control room. This is the only instance where updating of data in the system is required aside from the normal process of the RFID logs being updated via the movements of the prisoners.
Business Continuity
Human Risks
Human risks to the problem primarily come in the form of security personnel who will handle the observation of the prisoners. This aspect can be resolved through proper training and due diligence
Technical Disasters
Technical disasters in the case of this project are resolvable given the backup systems of the prison and the fact that the main control room does have some redundancy systems in place to prevent mass escapes
Natural Disasters
Given the nature of this project, there is no feasible plan that can be developed in the face of natural disaster.
Business Continuity Plan
Power Outages
Power outages will be handled by the backup power system of the prison.
Equipment Failure
Due to the multiple readers and backup servers in the system, equipment failure is not that big of a problem since all parts can be easily replaced.
Excess Demand on Servers
Given the nature of the data utilized, excess demand on the servers is not that great of a risk.
Project Management
Project Implementation strategy
Framing the Project
One of the first steps necessary in creating a project team for the Silent Hill Inc. prisoner tracking rollout is to frame the project in terms of its goal, what resources are available, what is the timeline for each step in the process and how will responsibility be delegated to individual team members. For this particular project the following can be considered an outline of how the project should look like from inception to outcome:
- Creation of effective suppliers and supply lines to facilitate the supply the need equipment and software – this entails negotiating with various software makers and suppliers in order to acquire the necessary equipment to setup the system in the first place. This can entail negotiating the price and the installation fee, determining the most effective layout within the various prisoner facilities and performing an initial test to determine whether the software is in proper working order.
- Determining proper task division among members of the project team – this aspect of the project entails assigning responsibility to particular project tasks. For example, this can entail assigning some to handle the contractors who will install the RFID readers, assigning someone to setup the control center and install and test the necessary software as well as have some determine the most efficient means developing the med center where the injections will take place.
- Organizing appropriate employee systems to facilitate the process of proper transition between the current methods of prisoner tracking to the method wherein the Indentchip system is utilized – this aspect of the project involves training the necessary personnel in utilizing the Identchip tracking system so that they would be able to utilize the interface without any problems. This is an important aspect of the project since it would be necessary to ensure that the people in the prison actually know what they are doing otherwise it may lead to a series of unfortunate events.
- Establishing proper client relations – establishing proper client relations is one of the most important aspects of project management given the necessity of ensuring that client’s are properly satisfied with the project outcome.
Team Composition
Since the basic project outline has now been established for implementing the Identchip system, it now becomes necessary to determine the overall composition of the team and how it should be organized so as to ensure that the RFID tracking project is accomplished with relatively few problems. One method of organization that could be potentially utilized is the vertical approach, more commonly known as the “top down approach”. This particular method of manage involves the use of a strict hierarchy which is established with orders coming from the team leader getting passed to the appropriate team member resulting in that individual accomplishing the task given to them. Such an approach in managing a technology intensive project allows for a greater degree of control over the process of task delegation and compliance to an established plan. It is based on this that, the top down project management approach will be utilized to ensure that everything is implemented based on the given project approach that was developed.
Operation of Project Team
Client Relations
As mentioned earlier creating effective client relations is an important aspect for Silent Hill Ince. since the company needs good buyer reviews to better establish its business. It is due to this that one division of the project team for this particular venture needs to deal with establishing business agreements with other prisons in order to facilitate the sale of company’s Identchip process.
Liaison Group
One aspect of the project team must deal with developing proper agreements with the suppliers for the hardware, software and labor necessary to put together the project. The reason why a liaison group is necessary is due to the fact that proper agreements need to be created so as to ensure that no problems occur in the supply chain. Possible problems that may occur is that an insufficient amount of readers may be ordered, the network and database equipment could be faulty or that the software is having some issues during the installation process. It is due to possible problems such as these that it is necessary to have a liaison group that specifically deals with the acquisition side of the project.
Furthermore the liaison team will be responsible in determining how many RFID readers will be necessary within the prison and determine how this will impact the price and rate by which the project can be completed within an appropriate deadline. This can either involve them scaling backing or increasing the amount of readers within the prison depending on need and the overall size of the facilities.
Product Development
One of the necessary aspects of proper project management is to ensure that there is an adequate level of product development within the project. Product development also involves taking the initial product and seeing if it can be improved beyond its original capacities through the use of new technologies. This can mean utilized new scanning methods to increase the range of the readers, more cost efficient RFID scanners so as to lower the overall cost of the project as well as software modifications that can be implemented that would result in better tracking. The possible applications are potentially limitless and as such are limited by the will and the imagination to put them into effect.
Evaluation
As with any project, it would be necessary to evaluate the overall effectiveness of the implemented systems and determine whether there needs to be some form of repair needed. Evaluating whether the project has been properly put together within the context of the tracking system is important before the project goes live for daily operational use. If proper methods of evaluation are not implemented beforehand, this can result in various anomalies and errors that may occur during the live performance of the system. For example, if there is an issue with the RFID readers not being able to properly detect the Identchips due to either a problem with the chips or the readers themselves, this needs to be determined beforehand and not when the chips have already been inserted into the prisoners and having them join the general prison population. Proper testing and reviews need to be conducted beforehand to ensure that the product is 100% effective in being able to properly track prisoners. Otherwise, should any of them escape due to the errors in the system, Silent Hill Inc. will be liable for such problems and may have to refund the entire cost of the project.
Project Life Cycle Achievement
All projects are subject to a certain lifecycle as indicated by the inherent limitations of the project itself and as such it becomes important to determine whether the team either contributed towards meeting deadline objectives, going over the deadline or even completing the project earlier than expected. Technology based projects need to conform to set resource and time limits from creation to completion. Project teams that expend more resources and time than what is legitimately necessary can thus be categorized as inefficient and negligent since it is their responsibility to ensure that projects are able to stay within set limits.
Thus, in evaluating a project team on the basis of life cycle achievement it is important to determine whether they sufficiently meet the project outline which showcased all the necessary aspects in ensuring proper project completion. This can come in the form of financial planning tools, time sheets, completed project milestones, daily reports and logistics software which combines all this data in order to determine the current rate of project completion versus the rate in which the project team should have been working at. By examining the data from such tools it will be easy to evaluate whether the team was able to properly meet and accomplish specific project milestones within a given time frame and if it was able to meet the project deadline that was created at during the project planning stage. For the purpose of this project, a GATT chart will be utilized in order to showcase the necessary project development goals and timelines that are needed.
Project Plan
Phase 1 (3 months)
Preliminary Examination of Prison Facilities
The first action that needs to be taken care of is an examination of the prison facilities. This entails determining the amount of equipment needed, the placement of the readers and scanners, the general layout of the facility, optimal locations for the placement of the readers, the amount of prisoners currently in the facility and the ideal location for the main control room. This aspect of the project is necessary before the project rollout can begin since effective project management enforces the need for proper budgetary estimation as well as the creation of a timeline for completion. Do note that this practice is also necessary so that the current administrators within the facility can help to develop a planning framework during the installation phase of the project. What you have to understand is that the installation of the readers, scanners, and control facilities will occur within an active prison environment. This presents a level of danger to the contractors that will be hired to install all the necessary equipment. It is based on this that it will be necessary to temporarily transfer prisoners into other sections of the facility so that work within the prison can be done with little in the way of adverse interference on the part of the prisoners.
Purchasing the necessary hardware and software for the project
After the project liaison team has completed the preliminary examination of the facilities and has determined the amount of equipment necessary and the various locations for their installation, it would then be necessary to contact the necessary suppliers in order to immediately purchase the equipment and software to get things under way. The purchasing of equipment early on in the project implementation phase is an absolute necessity due to two key factors, the first being that the project cannot even start without the equipment while the second factor entails the need to determine early on if there are any problems with the hardware and software and seek immediate replacement. The sooner the equipment is purchased, the faster the project can be completed.
Phase 2
Setting up the main control room
The main control room can be considered as the “brain” of the entire system and, as such, it would be the first and most essential component to setup. As soon as the equipment has arrived, one of the first activities that would be needed is to setup the server, install the software and determine that it is working properly prior to the installation of the rest of the network. This process would involve setting up the correct software configurations, running a preliminary diagnostic on the systems, running a test on the tracking software and checking if there are any discrepancies or “bugs” in the system. While the tracking and access system is relatively straightforward by design and does not require excessive computational power, it is still necessary to evaluate its operational readiness to ensure that it will be capable of handling the influx of information that it will go through on a daily basis.
Meeting with the Prison Guards
Once the main control room has been installed, it would be necessary to talk with the various security personnel within the prison and brief them regarding how the Identchip system works and how it would make their jobs easier. Briefing the security personnel is a necessary aspect of the project since they will be the ones to take over once the equipment has been properly installed and the chips placed in the prisoners. Without proper briefing regarding the technology, it is likely that mistakes could be made that would result in problems in the future.
Phase 3 (8 months)
Implementation
The installation of all the doors, readers, and scanners within the prison system is estimated to take around 6 months due to the need to rotate prisoners into different areas of the complex to avoid direct interaction with the contractors. Initially, the scanners will be installed into the various walls and corridors of the system as outline by the examination conducted by the liaison team beforehand. Once the wall mounted scanners have been installed, that is when the contractors will install the new RFID controlled doors section by section until the entire process is complete.
Training
Once all the equipment has been installed, it would be necessary to acclimate the security personnel regarding their proper usage. This will involve training them on how to properly use the handheld scanners, how to track an employee utilizing the interface in the control room as well as how to access the RFID doors. Do note that as protective measure, all security guards will not have RFID chips implanted into them. Instead, the various doors that need RFID clearance in the facility will require a direct override from the main control room before a guard can enter and exit that particular area. This will require the guard radioing in his location to the control room and requesting to be let in to a particular part of the facility. The reason such a method has been implemented is to prevent prisoners that are seeking to escape from merely kidnapping a guard and utilizing his implanted RFID chip to get into and out of the facility.
Phase 4
Testing
Once the RFID readers, scanners and prison doors have been installed, it would be necessary to test if all the systems work as they should. The testing procedure is actually rather simple, all that would be needed is for a group of prisoners (around 15) to walk around the section where the scanners have been installed and test out the new prison doors and scanners. A successful testing procedure would entail all the prisoners being properly identified and appearing on the system. An unsuccessful testing procedure would normally take the form of only some of the prisoners being logged in the system while the others would be “invisible” so to speak. Proper testing is an important aspect of the project since it helps to determine whether major changes need to be implemented.
Review of Implementation Procedure
Once all the equipment has been examined, proper testing has been conducted and the main control room setup. It is now necessary to create a review of the implementation procedure of the project. This aspect entails the adherence of the project team to the budgetary needs of the project, its ability to deliver the full project within the estimated deadline as well as focuses on a review of the team’s performance during the event itself. This aspect of the project is rather important since it helps Silent Hill Inc. determine whether there are discrepancies or failings on the part of the project team that could have been avoided. By identifying problems and addressing them before proceeding to the next project, this helps to ensure that such problems can be avoided in the future which will result in a more effective and efficient project implementation procedure in the future.
Phase 5 (3 years)
Rollout to other Prisons
Once it has been confirmed that the implementation of the Identchip tracking system in the first prison (i.e. the Sydney Prison System) is a success, the other prisons in the Australian prison system will be next. It is in the opinion of the project team that when it comes to implementing the Identchip tracking system, it will be necessary to push through a phased roll out rather than a simultaneous development of all the prisons. The reasoning behind this is that each prison may have its own unique implementation method that may need to be taken into consideration prior to installing all the necessary equipment and software. It should also be noted that Silent Hill Inc. has a limited amount of personnel available to properly implement the prisoner tracking project per prison. The act of attempting to stretch out the personnel in order to cover all locations at once could result in problems with the overall quality of the completed project which would be unacceptable given the need to maintain total and complete control over the various inmates in the prisons where the tracking system will be installed. As such, when it comes to project timeline for a full scale implementation of the Identchip system, 3 years would be the approximate time for full system integration into all of Australia’s prisons.
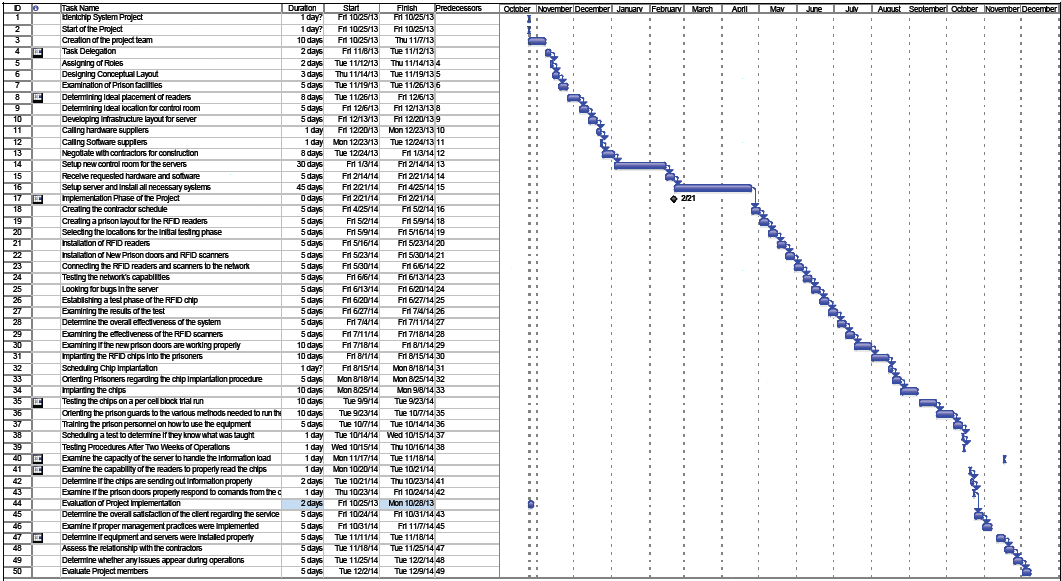
Human Resources
Training Plan
The training plan for this project is actually rather simple, the project team will schedule several “class sessions” while the equipment is being installed so as to familiarize the prison personnel with how the system works.
System Support
After the system has been installed and handed off to the onsite systems administrator and the various support staff within the prison, the issue of support after the product has been sold needs to be taken into consideration. Product support entails providing the necessary technical, maintenance and service level assistance that most electronic devices might need on occasion. Problems that may need the direct intervention of the company could come in the form of excessive delays in log creation, malfunctioning RFID readers, or instances where prisoners simply could not be tracked. When problems such as these occur, it would be necessary to immediately conduct support procedures to ensure the satisfaction of the client.
Management Support
Given the volatile nature of most prisons, there is a significant level of uncertainty as to the capacity of the project to be able to deliver on its promise of putting in place a system that can properly track and limit the movement of prisoners within a prison. What must be understood is that projects do not operate within a vacuum wherein decisions on specific operations within a particular system undergo eventual changes due to environmental forces (in this case a volatile prison environment). As environments and the factors that influence them change, so too do the objectives that drive a specific project. Failure to properly adjust a project’s objectives can lead to disastrous consequences for a company due to possible ramifications in terms of time and resources lost in supporting an objective that did not take into consideration changing events in the environment it is operating in. Taking this into consideration, this section delves into the various elements of project risk assessment and project assessment control so as to better under what factors need to be taken into consideration during the development and implementation phase of the Identchip system.
Project Risk Assessment for the Identchip System
First and foremost, it must be noted that in assessing any project it is necessary to focus on three specific factors, namely: identifying uncertainties, analyzing the risks, and prioritizing the risks by following these three factors, it is possible to minimize negative results in a project resulting in a successful product launch.
Identifying Uncertainties
The first step in the project assessment stage involves an investigation into the various uncertainties that cannot be controlled by the project team. These uncertainties often entail outside forces which can interfere with the project after it has been put into motion thus leading to the collapse of the project as a whole. Taking this into consideration, the following uncertainties have been listed as possible problems that may arise in the future:
- Failure of the network (though highly improbable) to handle the high amount of log data that is being transmitted to it on a daily basis. This constitutes the system being unable to properly track and log user data efficiently given the sheer amount of input (i.e. prisoner logs from passing by RFID readers). This is a system infrastructure risk that cannot be determined as of yet given the need to actually have the system up and running with all the prisoners inputting data via their normal movement in the prison.
- Failure on the part of the prison support team to properly utilize the tracking software. Despite the best efforts of the project team to train the various members of the prison support staff, it is still likely that some of them were unable to grasp the methods presented and will be unable to properly to utilize the system. This is a staffing risk given the fact that if they do not know how to properly utilize the system, this renders it useless.
- Additional protections on the scanners. While the project team will utilize the most durable RFID scanners for the doors of the prison, the fact remains that they may still be vulnerable to constant intentional abuse on the part of the prisoners in an attempt to destroy the means by which their movements are controlled. This is a hardware risk that the project team has no control over and similarly needs to be taken into consideration in the future should the problem arise.
- Necessity of independent power sources to keep the RFID system working in the event of a brownout. One of the main vulnerabilities of the system is that it is still dependent on electricity as a means of operation. Once that is taken away, the system is rendered useless. This aspect of the project can be categorized as a facility risk given the fact that the project team has no control over the backup power systems of the prison or if they even exist at all.
Analysis of Risks
When examining what could go wrong with the project, it is important to be as specific as possible so as to create a rough estimate regarding the likelihood of an event occurring and its potential impact should it manifest. This can help to mitigate the potential risks by putting into place the necessary plans to reduce their impact on the operational capacity of the system.
Prioritizing Risks
When it comes to the various risks encountered, it is necessary to develop some means of prioritization based on the probability of them occurring so as to minimize the chance of them occurring.
Mitigating Risks
Mitigating risks can be accomplished by either reducing the probability of risk occurring or minimizing its potential impact on the system by placing sufficient safeguards in place to prevent the problem from growing beyond the capacity of the project staff from controlling it. The following is a sample of the risk plan for the project and what risks the project staff have concurred have a chance of happening and what can be done to resolve them.
Legend: (1 Highest – 5 Lowest). Sample Risk Assessment Form.
Technical support / Customer Service
Technical support procedures usually entail members of the support staff of the prison calling an exclusive technical support number that belongs to Silent Hill Inc. The technical team at Silent Hill Inc. will be capable of handling software related support procedures via an end user interface within their computer system that focuses on a series of questions meant to determine the origin of the problem. For example, if the prison is experiencing problems with faulty or delayed logs the support representative would guide the support team over the phone regarding the proper diagnostic procedure to determine the origin of the problem and implement an appropriate “fix” utilizing the software tools that they have available. The user interface that the support representatives will utilize is the CARE customer service tracking assistant that is often utilized by various telecommunication companies in order to record the problem of a client and determine an appropriate fix via a set of walkthroughs that have been created beforehand. If, at the end of the walkthroughs, the problem still persists, it will be necessary to send over a technical support team to investigate the problem onsite and determine an appropriate fix for it. Do note that sending a technical support team is usually the final step when all other options have been exhausted given the cost associated with sending a team of specialists to fix a problem in a region that may be far from the location of the company.
Maintenance
Maintenance will be conducted on an “as needed basis” based on the need of the prison.
Service Level Agreements
On a support level, Silent Hill Inc. is required to provide support level services to the prison without charging them per call. The reasoning behind this is due to the variety of problems that may occur with the system and, as such, may require outside help in order to properly rectify the problem. Do note though that in instances where there has been blatant disregard for the procedures outlined in the instructions given for proper system maintenance and operation, Silent Hill will charge their client in order to remedy the problem due to the extensive amount of manpower and time that may be needed in order to fix the issue. Violations of the recommended operation include, but are not limited to, installing outside applications, removing essential system files, modifying the server system without first consulting the company and any such changes that could result in adverse consequences for the system. Aside from this, the company will also levy a charge for hardware and maintenance support for the various equipment that were installed within the prison. The reason for this is quite simple, daily wear and tear can happen to the various scanners, readers and doors utilized within a prison and, as such, it would be necessary to replace them from time to time. It would be financially disastrous for the company to absorb the cost of replacement, thus, charging the prison for replacing worn out equipment and even upgrading the current equipment when necessary is an essential aspect for the company’s operations.
Costs
This section of the report will attempt to forecast the total expenditure of the hardware, software and the consultation fee of Silent Hill Inc. Do note that this is merely a sample cost analysis and other costs may arise during the process of project implementation. As such, it should be viewed as a rough approximation of what the total costs may reach with the potential for a 10 to 20 percent increase depending on the needs of the project. These include, but are not limited to, the number of RFID readers necessary due to the size of the prison, the amount of personnel that would be required to install the system, added security for the contractors given the dangerous work environment, added server infrastructure requirements due to a larger prison population, greater levels of protection on the equipment due to employee tampering and other such concerns that may arise during the initial project examination done by the liaison team.
Initial Costs
The initial costs of the project constitute the needed hardware, software and labor necessary to setup the system in the first place.
Solution Infrastructure Costs
The solution infrastructure costs consist of the staffing and consultation fee cost for implementation.
Solution Implementation Costs
The following is the implementation price for the project; it details the labor, hardware, software, staffing and consultation price of all the necessary aspects of the project.
Recurring Costs
Recurring costs for the project are separate from the total costs since it involves costs related to equipment replacement which can range from $5,000 to $10,000 a year depending on the amount of damage done.
Total Cost
When going over the entirety of the cost analysis, it can be seen that the total cost of putting the project together is roughly $744,652 even with the cost of labor and consultation added. While initially this may seem like far too small an amount to implement a sufficient method of prisoner tracking, what you have to understand is that utilizing RFID as the basis behind the tracking method is actually a cost effective solution since it does not require an extensive and expensive server architecture in order to properly do its job. The 4 servers and the backup network storage device should be more than sufficient to handle the server load and can still be scalable should the system require more server capacity. Overall, it can be stated that based on the overall costs, the project can be stated as successfully devising a plan that can track prisoners within prison while at the same time being cost efficient in its design.
Benefits
Should the project prove to be a success and more Identchip system rollouts begin, it is expected that the benefit for this project comes in the form of safer prison systems within Australia.
Recommendations and Conclusions
The use of automated prisoner tracking systems can be described as the implementation of digital processes and technologies in order to increase the efficiency, reliability and coverage of internal and external government services and security to citizens (i.e. by keeping dangerous criminals off the street), while at the same time implementing a concept known as “lean operations” wherein wasteful spending, processes and methods of operation are in effect eliminated as a direct result of utilizing digitized procedures and systems to remove the “human component” which is usually the largest cost in maintaining a prison facility.
Basically, the use of automated prisoner tracking systems is a means of making the process of incarceration more secure by creating a means by which prisoners are monitored at all times which creates a far better means of ensuring that none of them ever escape. Thus, by utilizing the Identchip system in Australia’s jails, it creates the following positive effects:
- Greater citizen satisfaction in the way in which services are provisioned (i.e. making jails more secure through better monitoring).
- Fewer complaints regarding the inefficiency of government services (i.e. through the lower cost of prisons and fewer publicized escapes)
- Better connectivity technology and government operations which results in better efficiency and effectiveness
- Lastly, fewer resources wasted on inefficient processes and procedural “red tape”
For example, the automation of convict tracking in regions such as the U.S., and the U.K., through the use of electronic ankle detectors and house arrest considerably decreased the work force needed to keep convicts off the streets which resulted in a far faster method of knowing where convicts are at any given time and created a positive impact on local communities due to the greater security associated with utilizing this particular type of device. Electronic ankle trackers are a form of technology use which shows how the proper implementation of efficient, reliable and above useful IT systems results in a positive impact for both local governments and their citizenry.
As for government services, there has been an increasing trend in the implementation of technology based government services wherein people could avail of services such as health insurance, business registration processing, and taxation through the various online service platforms developed by government agencies in order to streamline such processes.
In fact it has been noted that one of the more interesting yet not at all surprising developments in technology use by governments has been a push towards having people conduct more and more of their inquiries and service requests online by making the costs associated with such online services far cheaper as compared to their “real world” service counterparts. For example, if the cost of a face to face small business registration within the U.S. or Australia would amount to $120. Its online equivalent on the other hand would be $50 or less. Thus, the implementation of electronic methods of prisoner tracking in the context of Australia’s prison system is in line with the continued trend of incorporating greater levels of technology in government services of which incarceration is one of them.
The reason behind why the Australian prison system should use automated prisoner tracking systems is quite simple, when it comes to a digitized process a government agency does not have to pay the costs associated with employee salaries, health insurance, facilities cost, electricity etc. A central control room can be hosted through a secure remote location with all the necessary data controlled and integrated through the server’s connection to a secure government network. In the long term, the Australian prison system will be able to save money by hiring fewer guards since the automated system already acts as a sufficient means of tracking and controlling the movements of prisoners.
While there are doubtlessly many merits to utilizing tracking systems and digitized functions, it must be questioned whether there are drawbacks to the implementation of such systems and whether it can truly result in a better functioning method of keeping prisoners in check.
The main issues related to the establishment of the Identchip tracking system are the following:
- Its inherently high costs versus the uncertain return on investment
- Low public interest in the operation of prisons
- Concerns regarding prisoner privacy
- Lastly, lack of sufficient initiative towards utilizing technology based services in prisons due to the current lack of examples wherein similar systems have been utilized in other countries.
Governments are in effect wasting millions if not billions a year on prisoner personnel. A better functioning government can be identified through its implementation of a system that creates a more efficient process resulting in greater citizen satisfaction yet what is being seen is the wide spread implementation of several operations that continue to expend more personnel into a prison system that is growing. What is needed is an approach that is scalable based on the growing prison population yet is not dependent on an increase in the amount of costs for guards to monitor the various prisoners. It is based on this that Silent Hill Inc. presents the Identchip system as the best solution towards building a scalable system that reduces costs for the government while at the same time products a more secure prison system.
The approach to a working and effective tracking system must follow the same line of reasoning seen in the case of the automation of convict tracking in regions such as the U.S., and the U.K. wherein there is actual and prolific usage of the system which results in satisfaction over the services provided. Based on this particular line of reasoning, it can be stated that with the way in which prisoners are being run at the present, it is unlikely that it will result in a better functioning means of prisoner control since money is being wasted on a massive scale on personnel. It is in this regard that one possible way in which to “fix” the current situation is to implement a method of “lean operations” wherein instead of a broad approach towards utilizing as many guards as possible to monitor prisoners, what would be done instead is to focus on a structured approach wherein the Identchip system is used as the back bone of prisoner monitoring. The way in which this could be accomplished is for the Australian prison system to judge whether the Identchip system can replace its current extensive workforce or if it would choose to continue operations as is.
Possible strategies that can be implemented to reduce the cost of the system comes in the form of implementing stricter budgetary allotments for Identchip tracking projects, the use of public-private partnerships in developing such systems in order to reduce costs and finally the implementation of sufficient methods of service analysis in order to determine which aspects of the system are essential and which are just a plain waste of money. It is anticipated that through the implementation of such considerations an efficient, effective and above all affordable means of automated prisoner tracking can be achieved which will subsequently result in a better functioning prison system. Overall, it can be stated that the RFID system is an effective method of limiting the ability of prisoners to enter particular areas of the prison by keying the RFID frequency emitted by the chips to the door locks which helps to minimize instances where prisoners escape as well as helps to create a better method of prisoner tracking as compared to present day operations.
Recommendation
Should you choose to implement our proposed system, we can actually set up a meeting with our technical team so that you can go over the nuances of the system, develop a means of implementation based on the current needs of your facility as well as determine the appropriate budget for installation on a per prison basis.
While it may be true that a proper electronic tracking system can lead to a better functioning prison, the fact remains that this can only be achieved through calculated and slow integrations of prisoner tracking into government run prisons rather than through a broad approach where the system is implemented on a large scale all at once. It is based on this that should you choose our system, we highly recommend a slow, prison by prison, roll out so as to ensure the quality and effectiveness of the installed systems.
References
Bray, A 2013, ‘Tracking physical assets: barcodes vs. RFID’, ABA Banking Journal, vol. 105, no. 2, p. 11.
Brusey, J, & McFarlane, D 2009, ‘Effective RFID-based object tracking for manufacturing’, International Journal Of Computer Integrated Manufacturing, vol. 22, no. 7, pp. 638-647.
Chen, J, Chen, M, Chen, C, & Chang, Y 2007, ‘Architecture design and performance evaluation of RFID object tracking systems’, Computer Communications, vol. 30, no. 9, pp. 2070-2086.
Chen, J, & Collins, T 2012, ‘Creation of a RFID Based Real Time Tracking (R-RTT) System for Small Healthcare Clinics’, Journal Of Medical Systems, vol. 36, no. 6, pp. 3851-3860.
Chien-Chang, H, & Jun-Hao, C 2011, ‘A Novel Sensor-Assisted RFID-Based Indoor Tracking System for the Elderly Living Alone’, Sensors (14248220), vol. 11, no. 11, pp. 10094-10113.
Cho, J, & Cho, M 2013, ‘Effective Position Tracking Using B-Spline Surface Equation Based on Wireless Sensor Networks and Passive UHF-RFID’, IEEE Transactions On Instrumentation & Measurement, vol. 62, no. 9, pp. 2456-2464.
Gutierrez, A, Levitt, J, Reifert, D, Raife, T, Diol, B, Davis, R, & Veeramani, R 2013, ‘Tracking blood products in hospitals using radio frequency identification: Lessons from a pilot implementation’, ISBT Science Series, vol. 8, no. 1, pp. 65-69.
Hinkka, V, & Tätilä, J 2013, ‘RFID tracking implementation model for the technical trade and construction supply chains’, Automation In Construction, vol. 35, pp. 405-414.
Jiahao, W, Zongwei, L, & Wong, E 2010, ‘RFID-enabled tracking in flexible assembly line’, International Journal Of Advanced Manufacturing Technology, vol. 46, no.4, pp. 351-360.
Lin, X, Lu, R, Kwan, D, & Shen, X 2010, ‘REACT: An RFID-based privacy-preserving children tracking scheme for large amusement parks’, Computer Networks, vol. 54, no. 15, pp. 2744-2755.
Martínez Pérez, M, Cabrero-Canosa, M, Vizoso Hermida, J, Carrajo García, L, Llamas Gómez, D, Vázquez González, G, & Martín Herranz, I 2012, ‘Application of RFID Technology in Patient Tracking and Medication Traceability in Emergency Care’, Journal Of Medical Systems, vol. 36, no. 6, pp. 3983-3993.
Narsoo, J, Muslun, W, & Sunhaloo, M 2009, ‘A Radio Frequency Identification (RFID) Container Tracking System for Port Louis Harbor: The Case of Mauritius’, Issues In Informing Science & Information Technology, vol. 6, pp. 127-142.
Öktem, R, & Aydin, E 2010, ‘An RFID based indoor tracking method for navigating visually impaired people’, Turkish Journal Of Electrical Engineering & Computer Sciences, vol. 18, no. 2, pp. 185-196.
O’Connor, M 2012, ‘A GUIDE TO RFID Tool-Tracking Solutions’, RFID Journal, vol. 9, no. 4, pp. 28-33.
Oztekin, A, Mahdavi, F, Erande, K, Kong, Z, Swim, L, & Bukkapatnam, S 2010, ‘Criticality index analysis based optimal RFID reader placement models for asset tracking’, International Journal Of Production Research, vol. 48, no. 9, pp. 2679-2698.
Reza, A, & Geok, T 2009, ‘Objects tracking in a dense reader environment utilising grids of RFID antenna positioning’, International Journal Of Electronics, vol. 96, no. 12, pp. 1281-1307.
Reza, A, Yun, T, Dimyati, K, Tan, K, & Noordin, K 2012, ‘Deployment of a 3D tag tracking method utilising RFID’, International Journal Of Electronics, vol. 99, no. 4, pp. 557-573.
Schneider, C, Tautz, J, Grünewald, B, & Fuchs, S 2012, ‘RFID Tracking of Sublethal Effects of Two Neonicotinoid Insecticides on the Foraging Behavior of Apis mellifera’, Plos ONE, vol. 7, no. 1, pp. 1-9.
Tan, K, Wasif, A, & Tan, C 2008, ‘Objects Tracking Utilizing Square Grid Rfid Reader Antenna Network’, Journal Of Electromagnetic Waves & Applications, vol. 22, no. 1, pp. 27-38.
Tesoriero, R, Gallud, J, Lozano, M, & Penichet, V 2009, ‘Tracking Autonomous Entities using RFID Technology’, IEEE Transactions On Consumer Electronics, vol. 55, no. 2, pp. 650-655.
Wu, Y, Sheng, Q, Shen, H, & Zeadally, S 2013, ‘Modeling Object Flows from Distributed and Federated RFID Data Streams for Efficient Tracking and Tracing’, IEEE Transactions On Parallel & Distributed Systems, vol. 24, no. 10, pp. 2036-2045.
Zetlin, M 2013, ‘RFID File-Tracking Solutions’, RFID Journal, vol. 10, no. 1, pp. 32-36.