Executive Summary
Top Breadz, a Sydney-based industrial bread and pastry manufacturer assigned our team to investigate how Business–to–Business (B2B) e-commerce solutions might benefit the company to reach its goals, namely, to increase sales by the retail outlets, to increase revenues by entering new markets or increasing market share, and to reduce operating costs.
In regards to these objectives, our proposed B2B e-commerce solution is the design and implementation of a B2B extranet portal for Top Breadz. The extranet solution includes a secure, easy-to-use order management portal to enable partners, suppliers and buyers manage their dealings with the company more efficiently and less costly and collaborative tools to share customer information with partners.
Undertaking the project will benefit Top Breadz by improving its bottom-line efficiency via cutting costs and time of the expenditure and revenue cycles. This not only reduces operating expenditures but also gives the company an edge over its competitors. Having a unified system for all partners also facilitates new market development or market penetration.
The risks to be considered by the Top Breadz team studying the solution are the following:
- Retail partners might not possess the proper or compatible Information Technology (IT) background to gain advantage of Top Breadz’s new system.
- Taking into account the lack of any legacy systems, and consequently, lack of experience in IT at Top Breadz, implementing a B2B e-commerce platform requires a fundamental shift within the business processes, which might prove to be troublesome and result in early faults.
- For the same reason, defining the exact scope of the project is unsure since the requirements are not clear in terms of scalability and future development.
- Initial capital outlay is substantial, especially compared to the cost savings only to be realized on the long-term.
The proposed system is perfectly capable of delivering the features that will help Top Breadz reach its goals. We therefore, recommend introducing the new B2B extranet system.
Introduction
Business to Business (B2B) e-commerce is becoming an increasingly important method of conducting buying and selling processes. One of the prominent lessons that have emerged from company experiences is the recognition of the significant role that extranets play in B2B e-commerce operations.
Among other things, this paper provides a discussion on how the use of a B2B e-commerce extranet, which has been proposed for Top Breadz, can improve the company’s performance.
Description and Explanation of the IT Innovation
The information technology services required for e-commerce are Internet, intranets, and extranets. An extranet may be defined as a secure network that uses Internet and Web technologies to connect two or more intranets of business partners, thus enabling business to business communications to take place effectively (Kallioranta & Vlosky 2004).
It allows trusted business partners to have secure access to information assets on another firm’s intranet. For example, Top Breadz may connect its computers with its various suppliers and retailers to ensure successful deliveries.
An extranet can be viewed as being part of a series of levels that include the Internet and intranet levels as well (Karra 2006, p. 5). Table 1 provides a comparison of the Internet, intranet and extranet while figure 1 illustrates a typical extranet configuration.
Table 1: Comparison of the Internet, Intranet, and Extranet
Figure 1: A Typical Extranet Configuration (Karra 2006, p. 5)
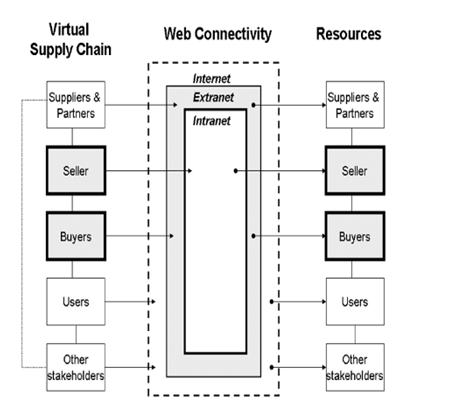
There are four things that can be said of an extranet. First, an extranet is part of the Web and its operation relies on the infrastructure provided by the Internet. Secondly, an extranet is privately owned. This is unlike the Internet that is not owned by any one. When compared to intranet, an extranet if public as it allows companies to access each other’s information.
Another major characteristic of an extranet has to do with the fact that it is mostly used to facilitate business to business interactions. By using an extranet, Top Breadz and its partners will be able to exchange information. Lastly, it is critical for any extranet to guarantee security and control the way information is accessed and shared (Kallioranta & Vlosky 2004).
Generally, the use of a Web browser at the front of an extranet makes it less intimidating. Users without a strong foundation in IT are, therefore, saved from worrying about what goes on at the backend.
Extranet Design Principles
Extranets share the same design principles formulated for the Internet. These principles include the following:
Interoperability
Interoperability for B2B e-commerce means that companies and customers do not have to purchase and upgrade software from the same vendors. Their computers will be able to communicate over the Internet because of the standard protocols such as Transmission Control Protocol/Internet Protocol (TCP/IP).
Layering
The structure of the Internet is layered. While the bottom layers of software are concerned with operating the computer hardware, higher layers come closer to the needs of the person using the Internet. For extranet users, the most relevant layer is the application layer which processes the information required by the Internet user.
The different hardware and application layers need to communicate with each other and they do so by using well defined interfaces. The Internet layering standard results in increased reliability of Internet software and is invisible to the Internet user.
Simplicity
The layering has resulted in simplicity of software design. Each layer is concerned only with its own functionality, making its design simpler. For example, the layer concerned with physical devices like mouse operations are hidden from the higher layers that process information. The kind of simplicity contributes to increased software reliability and hence extranet reliability.
Uniform Naming and Addressing
Each Internet host computer has an Internet Protocol (IP) address that uniquely identifies it on the Internet from millions of other computers on the Internet.
End to End Protocols
The Internet does not process information. It enables the transfer of packets of information between computers. The transmitting or receiving computers, known as the end system, do the actual processing of information.
Business Related Benefits of the IT Innovation
There are a number of benefits that are associated with the use of an extranet. Among the benefits of an extranet are the following:
Coordination
An extranet will allow the company to improve the flow of goods, services and information among it customers. The smooth interaction between Top Breadz and its partners will in turn improve efficiency and increase customer loyalty.
Feedback
An extranet will enable Top Breadz to receive instant feedback from its customers and other business partners. It will give consumers an opportunity to express their views about products or services before they are even introduced into the market.
Customer Satisfaction
Central to any business is customer satisfaction. When treated well, customers will always return to be served by the company. The use of an effective extranet will allow Top Breadz’s to increase the speed at which goods and services are delivered to the customers. Eventually, the relationship with the customers will therefore be strengthened.
Cost Reduction
With an efficient extranet in place, Top Breadz will be able to provide information to its partners in a timely manner and will equally receive whatever information it requires from its partners as and when needed. An extranet will also facilitate easy submission of purchase orders to the company by distributors. Top Breadz will also reduce its expenses through speedy delivery of goods as well as services.
Expediting Communication
Extranets increase the efficiency and effectiveness of communications among business partners by linking intranets for immediate access to information. A traveling sales person can receive the latest product information from his or her hotel room before going to a sales meeting.
Similarly, Top Breadz will be able to provide the latest information to a customer regarding its products without making several phone calls and going through different brochures and sales manuals.
Specific Issues that May be Associated with Extranets
Security is a critical aspect of extranet development, which extends to both the company and its partners. Security issues must be considered through the design, implementation, and management of any extranets applications.
Developing a security plan for an extranet application should begin with a risk assessment to identify the potential sources of threat to the network, how likely these threats are to occur, and the investment in security that will be required.
The level of security investment will vary depending on the nature of the extranet application, the threats of intrusion, and the sensitivity of the information shared on the extranet. Among others, extranet security should consider authentication and access control, privacy and data integrity.
Access Control
Access control provides or denies access to the network and is usually implemented through deployment of a firewall. A firewall alone, however, is not a sufficient security strategy.
Providing confidentiality of information while it is in transit over the public Internet can occur through encryption strategies. User authentication can take place in part at the firewall, but it is usually handled by the application service. User control, however, is almost always handled by the application service.
Authentication
Authentication defines the external population that is permitted to access the extranet. It will ensure that the external interaction with Top Breadz’s extranet is coming from an authorized source. Assigning account names and passwords to extranet users is one of the methods that will be used to implement authentication.
The identity of an extranet user will then be confirmed when he or she presents both the account name and password to the host application. A security policy that allows the use of one-time only passwords that expires once a user has been authenticated or encrypting the password before transmission will be a great addition to the strengthening of Top Breadz’s security.
Privacy
Privacy of communication with the extranet and exchange of data are typically implemented through an encryption technique. Encryption is the process of scrambling data before transmission over the public Internet. Several techniques are available such as public and private key cryptography systems.
While encryption is an effective strategy to protect the confidentiality of the information during transmission, it does not prevent inception and alteration or guarantee that the data packets are received intact.
Data Integrity
Data Integrity provides the assurance that the data transmitted over the public Internet are not modified in any way. For most applications requiring privacy, encryption techniques such as secure sockets layer (SSL) connection will provide sufficient data privacy and integrity. Virtually all Web browsers recognize the SSL protocol, among others, for data encryption.
Recommendation and Conclusion
In spite of the challenges discussed above, the use of extranets is bound to improve the performance of Top Breadz’s B2B e-commerce services. It is a convenient way of saving costs and has a wide reach.
Although the initial capital outlay is substantial, Top Breadz will certainly benefit by implementing the proposed solution. As was explained earlier, there are clear benefits that are linked to the use of extranets for B2B e-commerce.
In implementing the solution, however, it will be necessary for Top Breadz to ensure that retail partners possess the requisite skills to use the proposed system. This may be accomplished by assessing the capacity of these partners and providing training where needed.
All the concerned parties must also be sensitized in advance as their involvement in the entire process is critical for a successful implementation. The team investigating the solution should also work closely with their counterparts at Top Breadz to clearly establish the scope of the proposed system.
Reference List
Kallioranta, SM & Vlosky, RP 2004, A Model of Extranet Implementation Success Effects on Business Performance, <http://www.lfpdc.lsu.edu/publications/working_papers/wp66.pdf>.
Karra, VK 2006, Using Extranets to Add Value: A B2B Perspective. Web.