Cyber Kill Chain (CKC) means a sequence of steps that assist in tracing the phases of cyber-attack from the early investigation to the exfiltration of data. From the CKC’s application and utilization, technocrats in organizations understand and fight ransomware, security issues, and advanced persistent attacks (APTs) (Abbasi et al., 2021). CKC works by a range of phases that reinforce attacking and phishing during the process. This article presents research on the third phase, delivery, by conducting the appropriate tools applied in the stage. Additionally, the article discusses why email is the most successful via spear-phishing attacks.
Application of Delivery Tools in Cyber Kill Chain
Delivery involves the transmission of the weapon to the target during the control measure. In this case, the attacker can utilize different Universal Serial Bus (USB) drives, email add-ons, and websites for this initiative (Williams & Polage, 2018). The transmission and distribution of weaponized packages to the affected website comes with some digital fingerprinting. There is a representation of the most important phishing protection during the CKC (Ju et al., 2020). However, performing the defense defeats specific key abilities and other sensitive data. This stage measures the effectiveness of fractional intrusion attempts that are hindered at the delivery stage.
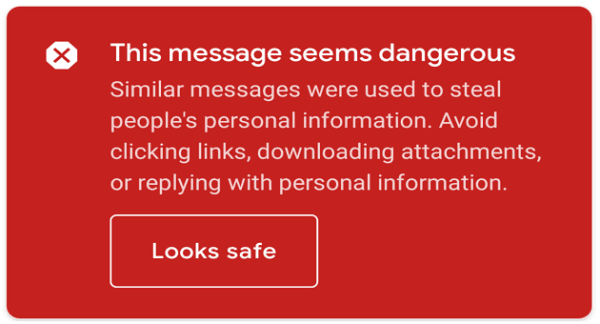
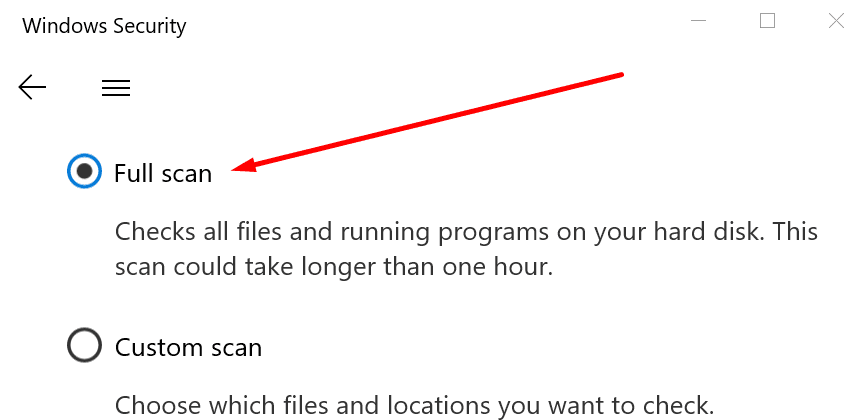
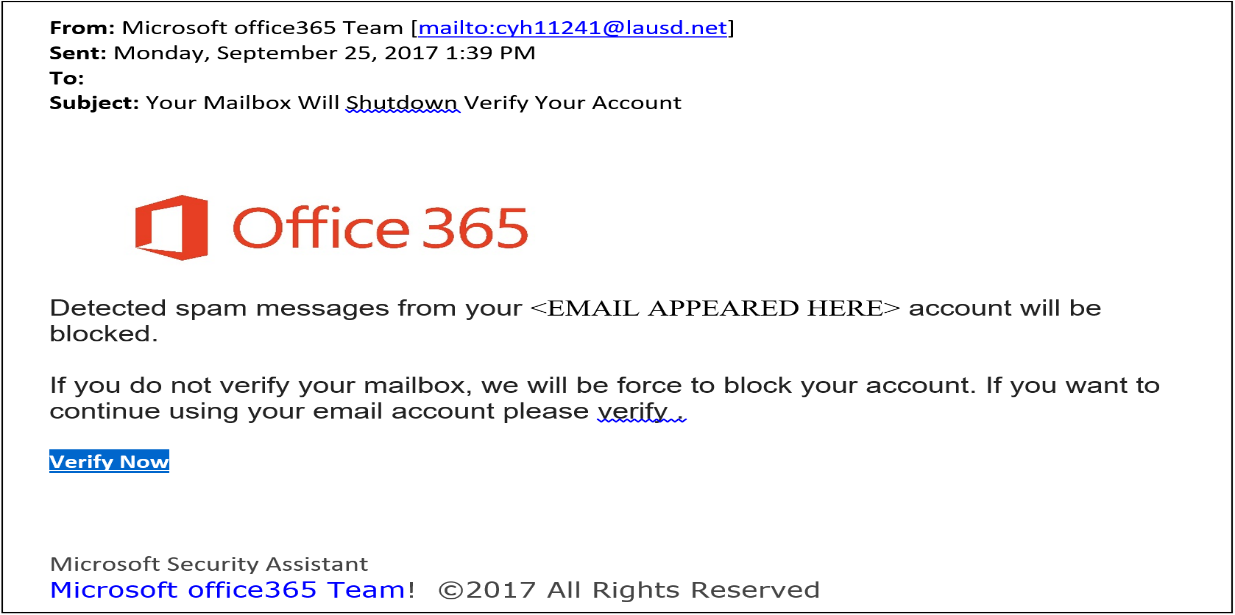
Explanation of How the Above Screenshot Issues Would Be Solved
Email is most effective via spear-phishing attacks because several solutions respond to attack at various stages during kill chain process. For example, Google’s ‘Gold Key’ program for Gmail usually cuts the kill chain at deception point by sending an indicator message to the user about the suspicious message (Fig. 1). Google gives a user an option of scanning to remove malware that might be present in the system (Fig. 2). Furthermore, Microsoft has a program known as ‘Green Shield’ that indicates trust issues in Hotmail and Outlook (Fig. 3). The stage involves posting website cautions for the users to avoid phishing.
Additionally, organizations may use a ‘phishing filter’ that warns users upon clicking a website about giving out their information to scammers. At this stage of delivery, competent Information Technology (IT) departments usually pollute the data and cut the chain by making the expropriated data invalid (Kim et al., 2018). Use of email prevents cyber-attacks by offering an interface that is disabled but has a notification button where a user can check the warning.
USB drives can be used at this stage to combat any phishing attacks. A software protector effectively prevents any information from being accessed or tampered with by the use of malware devices written in the USB drives (Ju et al., 2020). Companies have relied on encrypting their data where a USB cannot be read by the system memory. That enables the prevention of malicious attacks when hackers and crackers access the hardware devices that contain sensitive data and information (Sinha & Thakare, 2021). By effective USB firewalls, third parties find it hard to run their techniques in the background during the phishing process. The other activity in which CKC can be implemented under the delivery phase is by incorporating websites with Secure Socket Layers (SSL) intelligence. Under this process, websites require an SSL certificate to function as per the applied command. It is important to note that SSL certificates prevent phishing attacks on websites by encrypting user’s data to the authenticated configuration of data in the process.
Advise on How to Countermeasure for the Three Delivery Vehicles
The chief information security officer (CISO) can apply emailing, USB-drives, and website design to protect against phishing attacks. It is advisable that the CISO applies technology to eliminate the possibility of attacks reaching user data. Through applications such as Mimecast Targeted Threat Protection (MTTP), malicious links in messages can be scanned, and inbound emails are blocked from spreading to multiple users (Ju et al., 2020). The application contains weaponized attachments that preempt and sandbox all the suspected activity by performing security checks before delivery is achieved to the user.
The officer can add SSL certificates to the website, whereby any suspicious activity will be authenticated before the entire process runs completely. Through SSL, data will be verified for a secure connection between the main browser and the server, based on public-key coding. The recommended SSL certificate to use here is Extended Validation (EV) SSL (Ju et al., 2020). This would work effectively for an organization because the setting of EV SSL allows the website owner to go through an authenticated identity verification procedure that confirms they have the exclusive liberty to access the domain. The organization can use USB-drive technology to block any phishing attack during the delivery phase. Encryption can be made for the USB ports whereby only specific drives can be detected on a given device for an organization.
To combat the risk of cybercrimes, organizations can apply CKC to bar malicious access to sensitive data and information. One of the phases that the kill chain involves is the delivery phase. The stage involves the organization using email technology to prevent users from getting phishing attacks from online criminals. Furthermore, a firm can USB or SSL certification to secure the system in place. It is advisable that the IT team in any organization employ the Cyber Kill Chain technique to increase safety of the data and information contained.
References
Abbasi, A., Dobolyi, D., Vance, A., & Zahedi, F. (2021). The phishing funnel model: A design artifact to predict user susceptibility to phishing websites.Information Systems Research, 4(5), 12-19. Web.
Ju, A., Guo, Y., & Li, T. (2020). MCKC: A modified Cyber Kill Chain model for cognitive APTs analysis within enterprise multimedia network.Multimedia Tools and Applications, 79(39-40), 923-949. Web.
Kim, H., Kwon, H., & Kim, K. (2018). Modified Cyber Kill Chain model for multimedia service environments.Multimedia Tools and Applications, 78(3), 153-170. Web.
Sinha, V., & Thakare, V. (2021). Building and implementation of cyber security strategies under linux environment using Cybersecurity Kill Chain.International Journal of Computer Applications, 174(23), 34-37. Web.
Williams, E., & Polage, D. (2018). How persuasive is phishing email? The role of authentic design, influence and current events in email judgements.Behaviour & Information Technology, 38(2), 184-197. Web.