Abstract
Mobile ad-hoc network (MANET) is today’s one of the fine technologies that we have. The report shed light on the MANET and its characteristics. Though the MANET is a portable hosting system, used by various users, it has certain issues over the security of the data transfer. This is one of the important obsessions facing in the case of MANET. Even though there are many problems persisting much research has been conducted in securing the communication in the MANET network. Various researches show that there are plenty of solutions available for MANET in order to provide secure communication between the nodes. This paper starts off with a concise description of MANET and the various characteristics of MANET. Apart from that paper explains various kinds of issues that have been presented while communication taking place between the nodes present in the MANET. In order to provide effective and secure communication, there are different types of solutions present and this paper explains different types of security solutions for MANET for providing secure transmission.
Introduction
Ensuring effective security in Mobile ad hoc networks (MANET) has been considered to be very essential in the present scenario. This has got great potential for enhancing communication for different applications. The main objective of the research paper is to provide security solutions for MANET including the current Intrusion Detection System (IDS) approaches. Before explaining security solutions for MANET this paper will explore a concise explanation regarding MANET and its characteristics features.
Research aims and objectives
The main aims and objectives of this research are to provide a solution for MANET networks in order to have secure communication between the source and destination. In the case of MANET, there are plenty of issues evolving around the MANET while transmitting the messages over the network. Some issues may be complex and some may be very small issues. Even though these issues are small or big, it is sure that this is going to make a problem while communication takes place between the source and destination. The main objective of this paper is to provide different types of security solutions for this scenario. This mainly includes providing a description and analysis of those different types of solutions which enables MANET to have secure communication.
What is MANET?
MANET means Mobile Ad-hoc Networks. This is otherwise called a Mobile Mesh Network. “Mobile ad hoc (or spontaneous) networks (Manet) are IP networks made up of a collection of wireless and mobile nodes communicating via radio links.” (Albers, et al., n.d., p.1). The operation of these types of networks does not need any sort of predefined infrastructure or centralized supervision. Being spontaneous, these networks are always relying on an adapted routing algorithm in order to exchange various kinds of information all over the network.
Characteristics of MANETs
A MANET consists of many nodes, which are always free to move capriciously. These nodes are “located in or on airplanes, ships, trucks, cars, perhaps even on people or very small devices, and thus there may be multiple hosts per router.” (Garg & Mahapatra, 2009, p.242). These nodes are equipped with wireless transmitters and receivers, which are either omni directional or highly directional (point to point). “The hosts in MANETs are free to move randomly and organize themselves arbitrarily; thereby causing dynamic topology.” (Reshmi, Manvi & Bhagyavati, 2006, p.169).
Security Issues
Security issues are one of the major concerns of MANET. There are chances that these networks can get attacked. The attacks can be external or internal, denial of service, impersonation, eavesdropping and attacks against routing. Thus, there need security considerations in order to provide secure data transmission between the nodes. Some of them are as follows:
- “First, the security solution should spread across many individual components and rely on their collective protection power to secure the entire network.” (Yang, 2004, p.4).
- Implemented security solutions must be able to span different layers of the protocol stack. A single-layer solution will not provide an effective security solution.
- The security solution must be able to avoid potential internal and external attacks.
- The security solution should enhance three levels such as detection, prevention and reaction. The next segment of this paper explains different types of security solutions for MANET.
Research design and methods to finding data’s
The proper research design must be carried out in order to understand clear practice on different types of security solutions that employ in MANET networks. Research design is mainly framed to identify analyze different useful ways of conducting the research and it also involves taking decision-related to the different sources from which the information has been collected. Research design may be either qualitative or quantitative. The main intention of research design is to provide a clear path while doing the research.
The methods for data collection are planned in order to find out accurate information about data’s that is needed to do the research. The majority of the data’s used for this research is forms the secondary sources. This includes various types of research papers prepared by eminent persons, journals and academic articles. This method is used here in order to analyze different types of security solutions for the MANET network.
Security Solutions for the MANET
There are different methods that provide effective and efficient communication using MANET. Some of these approaches are explained below.
General Intrusion Detection Architecture for Enhancing Trust-Based Approaches
Intrusion Detection is a technique that provides secured network functionalities without compromising the efficiency of communication. The intrusion Detection system has got many characteristics. “An IDS collects and analyses audit data to detect unauthorized uses and misuses of the computer system.” (Albers, et al., n.d., p.7). While implementing IDS in AD-hoc networks requires some consideration because it should not affect the overall performance of the system. Besides, the system should run continuously and remain transparent to the users.
General Architecture for Ad hoc Intrusion Detection
The proposed system is a secure Local Intrusion Detection System (LIDS) on each node. The diagram has been shown below.
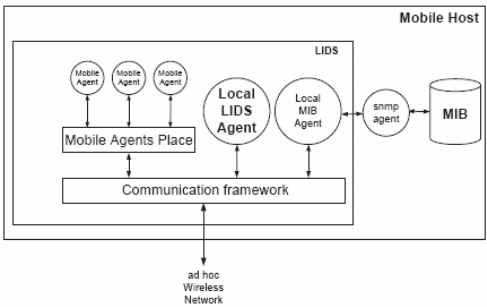
Normally, it employs two types of data; one is security data and another one is intrusion alerts. In the case of security data, it obtains information from various collaborating hosts. Similarly, in the case of intrusion alerts, it locally alerts about the problem. As an audit source for LIDS, it uses SNMP (Simple network management protocol) data that is located in MIBs (Management Information Base). All sorts of missions within LIDS are achieved in two ways called an autonomous and asynchronous manner. All kinds of internal and external communication that are taking place within LIDS always rely on a common communication framework. If the framework presented can understand IDMEF and IDXP messages then it can facilitate cooperation with other open IDS. “Any IDS capable of using the standards implemented by the framework may thus act as a remote data source either providing security data or intrusion alerts.” (Albers, et al., n.d., p.9.).
Data collecting agents present in the LIDS have got different functions that can enhance the security features. Local LIDS agent that is in charge of local intrusion detection and response always reacts to intrusion alerts that arise from other nodes in order to facilitate protection. The mobile agents collect and process the data, which is present on the remote hosts. These agents decide whether the data must be transferred to the home LIDS or to another node. The security control present in this agent can take care of malicious issues. The local MIB agent acts as an interface between the LIDS and tailor-made agent. The local MIB will collect the variables either for local LIDS agents or for mobile agents.
Methodology of Detection
In this architecture, it is the local LIDS agent that could detect the misuse and anomalies. The detection is based on the signature of the attacks and these signatures are defined in the MIB as variables. This is considered to be one of the best intrusion detection models, which take place with respect to the signatures.
Response to Intrusion
When LIDS detect an intrusion locally, it is the duty of LIDS to inform other nodes in the network about the intrusion. In other words, the user can refuse the connection that is having a suspicious node and this node is being from the corporative actions until it re-authenticates itself. When other nodes receive information about a threat; the LIDS acts as a preventive security tool and keeps the nodes away from the intrusion.
This is a simple trust-based mechanism that has been coupled with a mobile agent-based intrusion detection system, which always ensures the security needed for MANET. These types of mechanisms are complementary. Community’s gives a framework, which allows different types of a framework for security policies whereas intrusion detection always ensures that such kinds of policies are not violated.
Multifence Security Solution: Proactive and Reactive Approaches
There are many advantages in using proactive and reactive approaches in providing security to the MANET. The proactive approach mainly uses cryptographic techniques. “On the other hand, the reactive approach seeks to detect threats posterior and react accordingly.” (Yang, 2004, p.5). Proactive approaches use a more secure routing protocol. In the case of the reactive approach, this is employed or widely used in order to protect packet forwarding. In order to provide effective security to the network, MANET employs the use of detection, prevention and reaction techniques.
In the MANET context prevention component is mainly achieved by adopting the routing protocol, which is highly secure. This protocol prevents unauthorized installation of routing states. “These protocols are typically based on earlier ad hoc routing protocols such as DSR, AODV, and Destination-Sequenced Distance Vector (DSDV), and employ different cryptographic primitives (eg. HMAC, digital signatures, hash chains) to authenticate the routing messages.” (Yang, 2004, p.5). These protocols provide end-to-end protection to the MANET.
Network Layer Security
The main concern of network layer design is the protection of the functionality of the network in delivering the packets between the nodes. One is regarding the reliable exchange of messages between the nodes using correct protocol specification and the second is a secure transmission of the packet with routing states. The two methods employed for providing security to the MANET is based on “secure ad hoc routing protocols and secure packet forwarding protocols.” (Yang, 2004, p.5).
These two methods are using message authentication primitives for authentication of messages. The three widely used primitives are HMAC (message authentication codes), Digital Signature and One-way HMAC key chain. In HMAC two nodes always share secret symmetric key K among the nodes. They generate and verify the hk (), which is a message authenticator using a cryptographic hash function. The Digital Signature uses RSA techniques and more computations are used for encrypting and decrypting the messages. It needs to verify the signatures at each node to make sure everything is correct. While One-way HMAC key chain is a lightweight authentication technique is used to authenticate a large number of receivers.
Secure Ad hoc Routing
This technique uses a proactive approach in enhancing the security extension. Here, each of the mobile nodes proactively signs with any of the cryptographic authentication primitives. This can efficiently provide true traffic by differentiating good and bad packets. However, there are some cases in which the generated nodes are comprised and controlled by the attackers. To overcome this problem; it uses different types of routing protocols as Source Routing, Distance Vector Routing and Link State Routing. Source Routing protocols mainly employ Dynamic Source Routing (DSR). An extension of this is Ariadne. For message authentication, it uses a one-way HMAC key chain. For example, consider source S and destination D. A, B, C are the intermediate nodes. Then protocol establishes at the destination as follows: “H(C, H (B, H (A, HMACKSD (S, D)))), where HMACKSD(M) denotes message M’s HMAC code generated by a key shared between S and D.” (Yang, 2004, p.6). Route request (RREQ) and route reply (RREP) messages propagation are shown below.

Here, * denotes local broadcast and HMACKX () denotes generated code on nodes. Distance Vector Routing: This uses protocols such as DSDV and AODV. The main challenge is in advertising the routing metric correctly. This is different from the one-way HMAC. Here, whenever the message passes through the node; it increases the hop count by one. This is a complicated mechanism.
Link State Routing: This is another protocol used by Ad hoc networks. Its operations are similar to Open Shortest Path First (OSPF). Here, each node learns and updates its neighbor node with the help of Neighbor Lookup Protocol (NLP) and Link State Update (LSU). Secure Link State protocol uses a digital signature approach for authentication purposes. While sending the packet, the packets are signed with the private key of the sender. It also employs a time-out mechanism providing tight security.
Secure Packet Routing
Routing protection is considered to be one part and another important concern required is while forwarding the packet. According to the routing table, all packets should be forwarded. There are chances, even though packets are carefully signed, the packets may drop in the middle. The packet that has been dropped is traced out with utmost care.
Localized Detection
It employs the Watchdog Monitor mechanism while sending the packets from source to destination. If A needs to send a packet to B, then A can hear B, similarly, B can hear A. Since the overall path is well known when A sends the packet to B. It knows Bs next hop is C. When the packet reaches B it overhears the channel of B. If A did not hear anything; then it can conclude that failure has happened in B and A can send a report packet saying about Bs misbehavior.
ACK-Based Detection
When packets reach the destination, an acknowledgment has been sent to the source revealing that the packet has been reached safely. While sending acknowledgment; it uses an encrypted method. If the acknowledgment is not received within a specific time slot, it can be concluded that the packet has been lost. On detecting malicious activities among nodes, that node is isolated from participating in the routing activity.
These types of security solution provide an effective fence for the MANET, which secure the MANET network from any kind of intrusion. The protective fence includes all sorts of functional elements such as prevention, detection and reaction techniques. This uses various types of protocols to enhance all these properly.
An efficient and Attack Resistant Key Agreement Scheme for Secure Group Communication
“Secure group communication (SGC) is defined as the process by which members in a group can securely communicate with each other and the information being shared is inaccessible to anybody outside the group.” (Balachandran, et al, 2007, p.1298). Encryption of group keys is done in order to have secure communication in the MANET. A good SGC protocol can efficiently manage the group by considering the join and leave of members. The SGC and key management are closely related as in Mobile Ad hoc network various groups are automatically formed. Before discussing SGC and key management, some interesting features of MANET are mentioned below with respect to SGC.
No-Pre-shared Secret: The group members of the Manet have some sort of common secret key, but this key is not available for the public. As this key is not sent to anyone before the start of the session it is impossible to predict the secret information before forming the group. No Centralized Trusted Authority (TA) or Group Controller (GC): In MANET there is no central authority as the participating nodes themselves shape the network without infrastructure. Battery Power: The entire system is power-optimized, as the devices are dependent on electric current. It is seen that the wireless system transmits or receives information.
Thus, it needs a great amount of power. There is a need for an algorithm for SGC for computation as well as communication. Equal Workload: All wireless nodes are placed at equal distances such that they have equal work to do. Mobility: As the nodes in the MANET are mobile, they are likely to be out of the mobile network range of the other nodes. Due to these features of MANET the secure group communication scheme is issued to get the following features. Avoidance of the Member Serialization: Member serialization is the organizing and numbering of different group of members in the MANET. During the creation of group key, the messages are to be sent to all of the members either by a particular sequence or by broadcast/multicast system. Their IDs or sequence numbers identifies the members. These serializations are not possible with most of the cases with high node mobility thereby increasing the communication cost.
Contributory Key Agreement: This is a protocol by which each participant of the group is able to pre-determine the secret key. DH key agreement protocol is one among them. As there is no centralized authority, the SGC scheme is with agreement protocol. This allows each member to participate in the processes than work done by only a few nodes. Efficiency: The schemes are to be power-consuming and more efficient during computation and communication as the nodes are memory-constrained equipment. Good User Dynamics: The scheme should help the member to join/leave the operation with no trouble, which is one of the main functions of MANETS.
Proposed CRTDH Scheme
CRTDH is otherwise known as the Chinese Remainder Theorem-based DH contributory key agreement protocol. Key establishment: For the key establishment there is a sequence of steps, which are followed by each node. These steps allow each of the members to contribute their share to form the group key. As stated before, the members acquire and distribute their part of the key by the Chinese Remainder Theorem (CRT).
Join Operation
There is a need for certain operations when a new member joins a group. There is a bulk of work for the newly joined member than the existing member. The existing members have a little job, to receive the key and to XOR them with the hash of the old key. These hash keys are then sent to the newly joined nodes for getting the shares of the existing members. But it won’t allow them to read the messages sent by each other within them. If there are multiple nodes joining then, each of them has to follow the required steps for sharing their contribution for the existing keys. Thus, the existing members have to hash each of them together to make it a shared key. There exist only two types of communication; they are Unicast and Broadcast communication. Leave Operation: The Leave Operation enables the members to leave the group. The main step in the leave operation is the installation of new key with existing members other than the leaving node. The main problem on this is that the work that has to be done by the leaving node is then distributed among existing nodes.
Thus, implementation of the scheme should be made in such a way that is able to distribute this responsibility among members. CRTDH protocol is capable of supporting leave operation. Correctness of The Scheme: The keys sent by each node are calculated by the CRT, thus enabling the members to identify that the members use the same group key. The shared key from each node is used to join and make them a shared key. The shared key from each node is used here. Each of the members calculates the CRT values by a certain formula. Security of the Scheme: The CRTDH is secure enough to defend the crack done by anyone outside the member as the CRT is not flexible.
AUTH-CRTDH Authenticated Key: Unlike CRTDH, AUTH-CRTDH has a central key generation center (KGC). The main objective of the KGC is to distribute various IDs to all users. KGC is needed only at system startup, and then it is turned off. One of the types of attack possible in this operation is the LCM attack. The main cause for this attack is the LCM of the DH key, which cannot be unique at any time.
Offline System Setup: Each user in the system does have a unique identification. There is a series of steps for the system setup procedure. This is similar to the RSA algorithm. Security of AUTH-CRTDH: AUTH-CRTDH is able to protect itself from most of the attacks like the LCM attacks and the cracking done by exterior agents.
This proposed security solution is based on secure key management. Here while sending the message from the source, the source makes use of the key in order to encrypt the message so that no one can decrypt the message in the middle without knowing the key. The only receiver can decrypt the message as the key is shared by both sender and receiver.
Medium Access Control to Solve Hidden Terminal and Exposed Terminal problem
Medium Access Control plays a significant role in the functioning and providing security of the Mobile Ad hoc network. The mobile Ad hoc networks utilize the Medium Access Control (MAC) to perform normally in an efficient manner. In a wireless network, the transmitter cannot identify the occurrence of collision during the transmission. As a result, while the lengthy data transmission meets collision; the collision time may be long. Therefore, the reduction of collision during data transmission becomes a main problem for the Medium Access Control in Mobile Ad hoc network. Various methods like Carrier Sense, back off and Handshake methods have been employed to evade the collision in medium access. In the case of carrier sense, it needs that while the channel is inactive only the node can send out the data. In the Back off method, before the transmission, it compels every node to remain for a random period. Making use of short frames is done in order to evade collision between the transmitter and the receiver.
Carrier sense mechanism
It can be defined as a mechanism where received signal power exceeds some verge the node and it concludes that the channel is active. “It can be seen clearly that the value of CST decides the sensing range and affects both the collision possibility and spatial reuse in MANETs”. (Zhai, et al, 2006, p.155). The chance of new transmission meddling with some continuing transmission will be lesser if the sensing range is greater. The great sensing range also suggests that when one node is sending the data the other nodes have to postpone their transmission process.
Backoff Mechanism
In BEB, after a successful transmission; every station may rearrange the size of CW to the smallest value. Furthermore, if the transmission is failed the size of CW becomes twice. As a result, if the node has achieved the channel as well as transmitted the data in an effective manner. It may also achieve the channel in the subsequent channel disputation. If there are several active nodes and stern disputation for the channel the BEB identifies with less effectiveness. The investigation illustrates that when it arrives at the peak, along with the input traffic the collective throughput will reduce furthermore when the amount of dynamic stations is in a drenched position the collective throughput reduces.
Handshake Mechanism
It has been alienated that the multiple handshakes among the sender and receiver are Receiver Initiated (RI) as well as Sender Initiated (SI). While there are only awaiting packets in the queue the sender starts the handshake. “The exchange of short RTS and CTS frames in a four-way handshake between a transmitter and a receiver serves as a channel reservation that notifies overhearing nodes to defer their access to the shared channel so as to avoid collisions” (Zhai, et al, 2006, p.156). In the receiver-initiated channel, to observe whether they contain packets, the receiver censuses its neighbor in a dynamic way. To carry out the access of channel, the multiple accesses collision avoidance by invitation (MACA- BI) implements a three-way handshake. While comparing the four-way handshake of IEEE 802.11 Medium Access Control protocol, the control overhead is less in a three-way handshake.
Solutions to Hidden and Exposed Terminal Problems
The major reason for the collision in the multi-hop wireless network is due to the issue of the hidden terminal. Moreover, the exposed terminal issue restricts the reuse of spatial. Every node will have many hidden terminals while this wireless network spans a big region. In order to conquer the trouble of hidden terminal and expose the terminated out-of-band tone signal that is extensively utilized in several systems. The transmission of a busy tone signal is the use of Busy tones multiple accesses to maintain hidden terminals from the channel. Dual busy tone multiple accesses are used for avoiding problems related to the exposed terminal. For the problem of the exposed terminal and hidden terminal this busy tone method offers an easy solution.
This solution is mainly based on medium access control in MANET. Mac protocol provides solutions for these types of terminal problems. It has been seen that MAC has shown significant improvement in providing security to the MANET.
On-Line and Off-Line Security Measurement Framework for Mobile Ad Hoc Networks
Offering suitable security services for the MANET (mobile and ad hoc system) is essential for the task decisive application. The system helps to start a framework to resolve the various difficulties at the time of the planning of a self-adaptive safety system-provisioning proposal. Maintaining the most favorable offline safe protocol selection and the online safety management device is done by the system to organize various amalgamation of safe protocol to ensure various security needs in various applications. “Security in MANETs is a particularly challenging research issue due to the highly dynamic network topology, the lack of central authority, the shared wireless medium, and the memory and performance resource constraints.” (Savola, & Abie, 2009, p.565). In spite of progress in the area, there is a need for techniques for the assessment of the whole safety level of mobile and Ad hoc networks and a structure for the measurement and estimation of the extent of the reliability of the processes and the outcomes.
On-Line Security System
The online security measurement system is a device for the assessment of the mobile and Ad hoc networks’ safety level on the basis of the previous work. This aspect is self-adaptive with one exemption. The real assessment of the safety can be made on the basis of node point, system segment point level, and entire system point.
Off-Line Security Measurement System
It illustrates the scheme for the need-centric, model basis safety assessment. This structure would be conveyed is in the formal method. In this method, the procedures are made up in a practical point safety assessment and also it is vital that the assembly of confirmation information is utilized for the possibility and impact assessment
The deficiency in the awareness of negative needs is the main cause of security troubles. The independence of the proof differs a huge deal and it is hard to achieve better safety objectivity. In most situations, the extent of measuring set-ups is also set in a prejudiced mode. In general, no distinct precise value is capable to confine the safety assessment of a system. Therefore, numerous sections of safety evidence have to be balanced to bring up the viability and independence of the measurement made. Even though various researches have been made in the area of security of MANETs, the result, which has been achieved from these researches, is not very useful and hence the molding of security has not been easier.
Safety surveillance and judging can be made in the network sector also. This can be made possible in the situations where this section is quite still and the nodes within that section rely upon each other. In order to assess, the safety characteristics of a system, the definitions of safety action, atomic safety action, and safety behavior are necessary. A safety action is a behavioral unit that has some increasing and decreasing consequences of the safety point of a particular safety need. An atomic safety action is a safety action, which cannot be divided into further safety actions. It is the least point of visible safety behavior.
The safety behavior is a mixture of atomic safety actions of every safety need that consider their dependence. The dependence shows circumstance when a safety action is influenced by the transpiring of the other. “The final phase of off-line security measurement is the decision process. The main goal is to make an estimation and find out the conclusion on the level of the security of the system performance. The decision process can be split into sub-decisions based on different threats.” (Savola, & Abie, 2009, p.575).
The application of online surveillance is based on the calculation, storing and communication of resources. The databases of the surveillance have to be the latest. In order to ensure that this is achieved, the regular renewing of regarding the dangers, susceptibility, and status is very essential. The safety stage in MANET depends upon the blending of online and offline advances. The maximum circulation of significant control data has been an important safety purpose. The online safety surveillance system is based on every node being liable for the safety supervision of itself and also its neighbors.
It is a widely accepted principle that anything, which cannot be measured, cannot also be well handled. Therefore, a systematic mechanism to measure things in this area has to be found which may solve the problem and provide better research results in this area so that developments can be effectively made.
Conclusion
MANET has gained more popularity in this world because of its significant features. It has got great potential to enable communication over a large number of applications. There is no doubt that MANET is going to explore this world. However, there are some concerns regarding the security issues of MANET and many types of research have been developed in this field analyzing the different types of securities of the MANET. Still, this area is open for research people to explore more contributions in providing security solutions to MANET.
Reference List
Albers, P., et al. (n.d.). Security in ad hock net works: A general intrusion detection architecture enhancing trust based approaches, p.1. (Provided by the customer).
Albers, P., et al. (n.d.). Security in ad hock net works: A general intrusion detection architecture enhancing trust based approaches: Audit source and computing location, p.9. (Provided by the customer).
Albers, P., et al. (n.d.). Security in ad hock net works: A general intrusion detection architecture enhancing trust based approaches: Characteristics of intrusion detection systems, p.7. (Provided by the customer).
Balachandran, R. K., et al. (2007). An efficient and attack-resistant key agreement scheme for secure group communications in mobile ad-hock networks. Wiley Inter Science, p.1298. (Provided by the customer).
Garg, N., & Mahapatra, R. P. (2009). Manet security issues: Characteristics of Manets, 9, p.242. (Provided by the customer).
Reshmi, B. M., Manvi, S. S., & Bhagyavati. (2006). An agent based intrusion detection model for mobile ad hoc networks. Mobile Information System, p.169. (Provided by the customer).
Savola, R. M. & Abie, H. (2009). On-line and off-line security measurement framework for mobile ad hoc networks. Academy, 4, p.565. (Provided by customer).
Savola, R. M. & Abie, H. (2009). On-line and off-line security measurement framework for mobile ad hoc networks. Academy, 4, p.575. (Provided by customer).
Yang, H. (2004). Security in mobile ad hoc network: Challenges and solutions. Ieee Wireless Communications, p.4. (Provided by the customer).
Yang, H. (2004). Security in mobile ad hoc network: Challenges and solutions: A multifence security solution. Ieee Wireless Communications, p.5. (Provided by the customer).
Yang, H. (2004). Security in mobile ad hoc network: Challenges and solutions: Secure ad hock rounding. Ieee Wireless Communications, p.6. (Provided by the customer).
Zhai, H., et al. (2006). Medium access control in mobile ad hock networks: Challenges and solutions: Carrier sensing range. Wiley Inter Science, p.155. (Provided by customer).
Zhai, H., et al. (2006). Medium access control in mobile ad hock networks: Challenges and solutions: Sender-initiated and receiver-initiated channel access. Wiley Inter Science, p.156. (Provided by customer).