Introduction
Money laundering is considered to be one of the most wide-spread financial crimes of the 21st century. It damages the world economy by rising inflation, supporting crime and terrorism, and enabling individuals and criminal organizations to use their ill-gotten gains unopposed (Caine). According to New York Times, “the front door of money laundering is the banking system, which, due to government efforts, remains closed. The backdoor, which is the international trade system, remains wide open” (Caine). The purpose of this paper is to research the subject of trade-based money laundering, its impact on global scene and export controls, identify types of trade finance techniques used to launder illegal money, and provide a chart of red flags that indicate to potential money laundering.
What is Money Laundering?
In order to understand why money laundering is dangerous and what could be done to prevent such malpractices, it is first required to provide the definition of the term. The working definition accepted in all countries across the globe is provided by the FATF, or the Financial Action Task Force, which is an international organization created with the purpose of setting standards and promoting effective implementation of various measures for combating money laundering, as well as cutting off terrorist financial supplies and dealing with other issues threatening the integrity of the global financial system (FATF 2). According to FATF, money laundering is identified as a process that hides the existence of illegal income, their sources, as well as various illegal applications of income by disguising that income and reintroducing it into the economic system as legitimate (FATF 3).
Stages of Money Laundering
Typically, money laundering schemes pass through three stages, after which the reintegration of illegal income into the formal economy occurs. The first stage is money placement, during which illegal money is introduced into an otherwise legitimate enterprise. This could be done, for example, through putting money in a bank account. The process of layering that occurs after is used to distance money from its source through numerous transactions. The last step is the integration of money into the formal economy, in a way that appears legitimate and is used for purchasing legitimate assets (Caine).
Methods of Money Laundering
FATF identifies three main methods used by criminals and terrorists with the purpose of hiding the origins of money and reintegrating it into the formal economy. These methods are financial money laundering, physical money laundering, and trade money laundering (FATF 3). Financial money laundering relies on making large amounts of investments, deposits, credit cards and other operations to effectively split the large sum into smaller ones, making it easier to hide its origin and avoid detection (“Trade-Based Money Laundering”). The second type is widespread in the USA and Mexico, where drug money is transported back and forth in large quantities. Trade money laundering involves using illegal money to purchase goods and then transferring them across the border disguised as a legitimate trade operation. Various criminal elements exploit the loopholes and weaknesses in the global trading system, as well as massive amounts of transactions conducted daily in order to hide their own activities.
Trade-Based Money Laundering
FATF identifies TBML as “the process of disguising the proceeds of crime and moving value through the use of trade transactions in an attempt to legitimize their illicit origins” (FATF 4). Governments and financial institutions across the world have put considerable efforts into combating money laundering techniques used in the financial segment, making it harder for criminals and terrorists to reintroduce their ill-gotten gains back into the formal economy. This is the reason why trade-based money laundering is on the rise, as a host of anti-laundering laws and identification demands imposed on the banking system makes it much riskier to conduct such operations. Transferring stolen money through objects of value, on the other hand, has much fewer risks (The Hong Kong Association 5).
Stages of Trade-Based Money Laundering
Trade-based money laundering goes through the same stages as other types of money laundering but in a different way. Instead of depositing money in bank accounts and using various transfers and banking transactions to obscure the money trail, TBML suggests transferring money into purchasable assets, such as goods, and hiding their origin through trade operations involving one or several cover-up companies. In the end, when the money is reintroduced into the formal economy, it is done so through legal sales of goods purchased on illegal income (Caine).
The Four Basic TBML Methods
There are four basic TBML Methods which are used more often used to launder money. Over-invoicing is a technique that enables the transfer of value to the exporter, while under-invoicing – to the importer. Multiple invoicing allows the criminals to receive multiple payments for a single shipment of goods. Over- and under-shipments, as the name suggests, involve transferring bigger or smaller shipments for the same amounts of money. Lastly, false descriptions of services and goods involve diminishing or exaggerating the qualities of goods to justify the price (“Anti-Money Laundering Risk” 5).
Trade Finance in Relation to Money Laundering
Trade finance is avidly used in international trade as a means of paying for goods and services between companies. As such, it is an excellent way for criminals to use it to conduct TBML operations, as all of them are camouflaged to be legitimate enterprises. This, and the amount of paperwork that trade finance operations usually solicit, as well as various complications in inter-bank relationships allow criminals and terrorist organizations to use trade finance institutions to launder money (“Anti-Money Laundering Risk” 3).
Trade Finance Techniques Used in Money Laundering
These trade finance techniques are most frequently used in order to launder money, due to the fact that they make up the core of financial operations used in legitimate trade. In particular, letters of credit and guarantees are used to conduct over and under-invoicing operations as well as pay for multiple invoices, as usually banks do not require any extended proof of fairness of the transactions that have taken place. Banker’s acceptance and open account financing are also tools that can be used either to conduct money laundering or to use the already laundered money to finance an otherwise legitimate business (“Anti-Money Laundering Risk” 8).
The Role of Trade Finance Organizations in Mitigating the Risks of TBML
There are several ways in which banks and other financial institutions may mitigate the risks of TBML. The Know-your-customer program allows financial organizations to assess the risks of money laundering posed by particular customers by analyzing the nature of their business and establishing their identity in order to implement a necessary level of monitoring. Due diligence suggests gathering information on the nature of the goods, as well as identifying applicants and beneficiaries in relation to the traded goods. Lastly, the transaction monitoring program should keep a look-out for the potential violations of Anti-Laundering laws and sanctions (The Hong Kong Association 5).
Red Flags for TBML
- Major differences between the invoice and the descriptions of the goods.
- Customer does not follow the standard business procedure.
- High-risk nature of shipments or businesses.
- Commodity is shipped to or from a country known for their laundering activities.
- Shipment does not make sense from an economic perspective.
- Use of shell companies.
- Unnecessarily complicated transaction structures.
- Entities related to the transaction have no apparent connections to it.
- Commodities provided by the customer differ from those associated with their business.
- Shipment locations and conditions of trade differ from those mentioned in the letter of credit.
- The product is more expensive or cheaper when compared to the average market price(“Anti-Money Laundering Risk” 7).
- Red Flags for TBML.
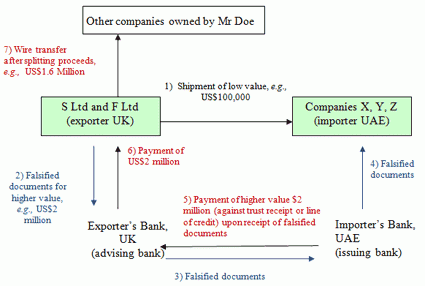
Here is a classic example case of over-invoicing for goods, which was conducted by an expatriate businessman who used this scheme through the use of companies in the UK and the UAE, both of which were allegedly controlled by him. This type of fraud uses falsified documents in order to cover up transactions of low value at the start, and the reception of higher value payments based on a trust receipt or a line of credit given on falsified documents. The chain goes as followed (Chandrasekhar):
- Shipments of low value are sent from companies in the UK to companies in the UAE.
- Falsified documents for higher value are provided to the exporter’s bank in the UK.
- Falsified documents are transferred from the exporter’s bank to the importer’s bank in UAE.
- Falsified documents reach the companies in the region.
- Payment of higher value is sent to the importer through both banks and is then received (6) by the exporter companies in the UK.
- Laundered money is transferred to somewhere else.
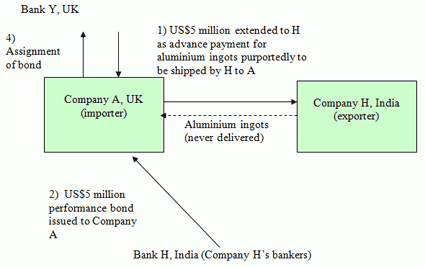
- Company A extended a US$5 million advance to Company H that was to be repaid by the receipt of aluminum ingots from the exporter at a future date.
- Company H’s obligations to supply the metal were backed by a performance bond that was issued by its bankers (Bank H), favoring Company A. Should Company H default on its ability to deliver the ingots, Bank H would compensate Company A to the extent of US$5 million.
- Company A, in turn, borrowed US$5 million from its bankers (Bank Y) and assigned the benefit of the performance bond to that bank. In due course, Company H reneged on its obligations under the original purchase contract.
- Company A repaid the US$5 million to Bank Y and took back the performance bond that was in its favor. Company A then claimed a similar amount from Bank H (Chandrasekhar).
Conclusions
Money laundering is one of the great enablers for the existence of large organized crime rings and various terrorist groups, as it provides them ways of legitimizing their ill-gotten gains to finance their operations further. Statistics show that the number of transactions prevented and apprehended by the authorities is extremely low, which means that most of the illegal money becomes laundered and is used to purchase goods, assets, and services. This presents a challenge to the world trading and financial system and threatens its stability. In order to prevent trade-base money laundering, stricter adherence, and control, as well as total transparency of the financial and trading sector is required (“Anti-Money Laundering Risk” 5).
Works Cited
Anti-Money Laundering Risk in Trade Finance. 2016. Web.
Caine, Kimberly. “Trade-Based Money Laundering is on the Rise.”Law360, 2015.
Chandrasekhar, Deepa. “Trade-Based Money Laundering: A Case Study.” The Anti-Fraud Network, 2011.
FATF. The FATF Recommendations. 2012.
The Hong Kong Association of Banks. Guidance Paper on Combating Trade-Based Money Laundering. 2016.