The most actionable cybersecurity tips for students include using strong passwords, enabling two-factor authentication, avoiding suspicious links, and updating software regularly. These simple yet proven measures can safeguard personal and academic details from increasingly sophisticated cyber threats.
The importance of cyber security for students cannot be overstated. Since the shift to e-learning during the COVID-19 pandemic, cybersecurity concerns for students have significantly grown as cyber criminals are becoming more active than ever. They target learners, educators, and even parents trying to steal sensitive data.
Want to know how to stay safe in today’s digital world? Check out this practical guide created by IvyPanda experts. Here, you’ll learn:
- Why cyber security is important for students
- The main types of cyber security threats, such as malware, phishing, camfecting, data theft, and file-sharing risks
- The proven ways to mitigate these threats
- Practical recommendations on cyber security for students
🤔 Why Cyber Security Is Important to Students
Cybercriminals target schools, colleges, and universities more and more often. The reason for this is simple. Typically, educational networks contain extensive personal information that isn’t well-protected. Their colossal size also makes it easier to infect other devices and steal more data. Students and institutions are notoriously famous for their lack of concern with cyber security.
The situation has become worse during the pandemic. Cybercriminals now have more reasons and more chances to target academic spaces.
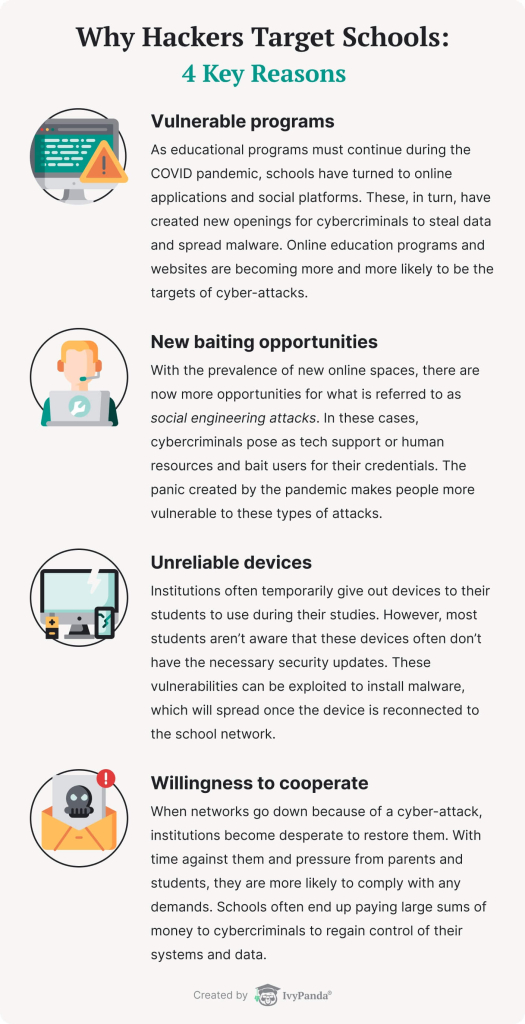
With the rise of cyber-attacks on academic institutions, the number of attacks against students has also increased. Therefore, every individual user must be aware of the new dangers lurking on the Internet. Furthermore, they must know how to protect themselves. Next, we will talk about which cyber-threats are especially risky for students and how to safeguard against them.
💻 Malware
Cybercriminals, or hackers, often develop software intended to steal or damage data and destroy computer systems. This is referred to as malware or “malicious software.” There are many ways it can spread to a device. Spam emails, fake messages on websites, and pop-up ads are notorious for carrying malware. Downloading any kind of software from the Internet also increases the risk of being secretly infected. This is true even for applications acquired through legitimate methods.
In the case of malware, the spectrum of threats is rather extensive. It spreads not only to computers and mobile devices but also reaches the rest of your data. In the list below, we have explained different types of malware threats:
- Computer viruses. Just like humans, devices can become infected by viruses. Students can easily acquire one alongside a downloaded PDF or Word Document. It will activate once the software it is connected to is executed or opened. Viruses’ purpose is to disrupt your computer’s system, cause operational difficulties, and damage your data.
- Trojan horses. Named after the famous incident described in The Iliad, this type of virus masquerades as helpful software. It tricks the users into downloading it, only to cause harm once the program is running. The damage can range from irritating pop-ups to major data loss.
- Spyware. There is a type of malware that runs discretely, silently stealing personal data or sensitive information. Spyware can even grant its creator the ability to change various programs and Internet settings. Typically, people download it alongside other safe-seeming software.
- Worms. What separates a worm from a virus is its ability to compromise a device instantly. The moment you download it, it will start affecting your computer´s system. It will also immediately spread from device to device and system to system. Students and schools are often targeted with worms because of their extensive networks and databases.
- Adware. We have all suffered from advertisements during our time on the Internet, and it is never a pleasant experience. However, what makes adware particularly dangerous is that it can cause significant issues to your system. Sometimes, it contains other viruses or Trojan horses, and it can slow down your device.
- Ransomware. It is designed to find your data and then encrypt it. In this case, you will no longer have access to your accounts or files. To get your information back, you will have to provide a monetary payment to the cybercriminal. These attacks are common among university and school websites because of the pressure to get back sensitive details.
How to Prevent Malware
Your protection against viruses and other types of malware depends on how well you take care of your device. Constantly upgrading your software, using antivirus programs, and cleaning can prevent the majority of threats. However, your Internet activity also plays a significant role.
To protect yourself from malware on your computer and mobile devices, follow our checklist:
- Keep your software updated. No application is ever 100% safe against malware. Yet, developers constantly try their best to combat threats. Regular updates and patches fix the vulnerabilities that tend to show up with time. Thus, it is a critical practice to keep your software validated and up-to-date.
- Install antiviruses. These types of programs detect viruses, spyware, and other malicious software. They are also equipped to remove them. Update your antivirus and run regular scans to check for any threats that managed to slip through.
- Get used to non-administrator accounts. The silver lining about catching malware is that it is often tied to the active user. In other words, it has the same privileges as the account you were using when you installed it. Be careful when wielding administrator credentials. Try to do most of your work on non-administrator accounts.
- Come up with strong passwords. There is a reason why a lot of websites have high demands when creating an account. A longer password with uppercase and lowercase letters, numbers, and special symbols is harder to crack. Make sure to include these when coming up with one. Plus, use different passwords for different websites.
- Try multi-factor authentication. If it is available, it is usually recommended to enable an additional security question or a PIN. It may take slightly longer to access your account, but at least you will feel be more secure.
- Look out for suspicious activity. This goes out for all your accounts and devices. For example, you might find a purchase you cannot remember. Or you can see that someone has accessed your email from a different country. Change your passwords immediately and contact any relevant tech support for further instructions.
- Avoid suspicious emails, links, and files. If you have an antivirus installed, it will typically scan your Internet traffic for malware. However, it is still best not to click on anything that seems out of place. Ignore any pop-ups promising you a million-dollar reward. Besides, stay vigilant when downloading files from the web.
- Use secure payment methods. This goes double for online shopping. Typically, credit cards or online payment services are the safest way to pay on the Internet. Keep track of your purchases and make sure that the website you’re using is a legitimate vendor.
👩💻 Email Phishing
Phishing is a cyber-attack in which hackers administer a fraudulent activity employing email, telephone, text message, or phone calls. Phishers may try to steal your credit card information or trick you into doing something by shocking you. Such scams often ask you to “confirm” your identity by going to a fake website and providing your personal data. In this section, we’ve explored email phishing specifically. Scammers tend to use this method to attack students.

The ultimate goal of every phishing activity is for the receiver to open up the email and provide the requested info by clicking on the link. That’s why the requests are usually one of these:
- Fraud Google Doc notifications.
- Emails asking for your login information.
- “Tech Support” scams with concerns about your laptop’s issues.
- Emails about scholarships and tuition payment processors.
- “Work-from-home” scams.
- Impersonated IRS requests asking you to pay “federal student tax” via the link.
- Fraud ads regarding housing.
- Emails that have “important information about your school account.”
💡 Keep in mind:
No official organization asks a student or any other person to send their personal data via email without any warning. In particular, no banks, social media representatives, or other trustworthy sources seek your passwords.
How to Prevent Email Phishing
To avoid phishing risks, you need to pay close attention to what type of emails you receive and open. You can identify if you got spam email by the following features:
- Suspicious address. The address of the sender may try to imitate a legitimate business. Nevertheless, some characters might be omitted or altered.
- Generic, unspecific greeting. A greeting in a phishing attempt is usually impersonal. A lack of signature block with the name should raise red flags. Besides, a credible company will use your name.
- Poor grammar. Misspellings and lousy formatting are usually indicators of a phishing attempt. Trustworthy organizations have well-trained employees that proofread all customer-facing correspondence.
- Weird hyperlinks. Very often, a phishing email will have hyperlinks in the body of the email. The links can look identical to a legitimate site with a variation in spelling.
- Suspicious files attached. A phishing attempt can have an attachment, a common way to deliver a virus to your device.
However, knowing what to look out for in the email is not always enough to protect yourself. From time to time, it will be dangerous to open spam messages. To avoid these situations, you need to do the following:
- Don’t share your personal information via email and via messages.
- If you need to send a confidential letter, make sure the email of the receiver is legitimate.
- Use filters in your mailbox and all the messengers.
- Don’t post any personal information on untrustworthy websites.
- Use multi-factor authentication whenever it is possible.
- Check the list of cyber threats that attack the students from your campus.
You can find some more tips on how to protect yourself on the website about phishing.
📲 Social Media Phishing
Social media scam is a form of phishing in which cybercriminals connect with their victims through social media platforms (IG, FB, WhatsApp, Snapchat, etc.). It usually starts by sending a friend request. After the victim accepts it, they soon form a conversation. They can also publish a link that sounds irresistible (“put your data and win a car”).

Depending on the social media platform, phishers use different tactics to gain victims’ trust. Here are some examples:
A Facebook phishing attack is made through a message or link posted on the wall. It asks people to confirm their identity. Afterward, it allows attackers to gain access to their page.
People could also get notified that their Facebook account has issues. Make sure that the URL you have received is directed to www.facebook.com.
A phishing attack on Instagram starts when a criminal creates a fake login page for the website. A clueless victim puts their login details, and the scammer captures the credentials. After gaining access, a hacker can send fraudulent messages to the followers. They can also try to take full ownership of the account.
Another problem can arise if you communicate with people you don’t know personally. They can pretend to be a celebrity or a new friend and ask for your personal data or money.
He, hackers Twitter use the same methods as they do for other social media platforms. Victims receive messages supposedly coming from Twitter. They are asked to provide login details, credit card numbers, and additional personal info.
Danger can also come from subscribers who try to get your personal information.
There are two ways in which hackers can obtain personal information. Firstly, by logging into a victim’s account and sending fraudulent messages to colleagues and connections. Secondly, by sending out emails that are “as if” coming from the support team. Find out how the website works and how to use LinkedIn to avoid phishing.
How to Prevent Social Media Phishing
One of the things we hear as kids a lot is not to speak to strangers. It applies to the Internet too. However, the majority of young people neglect this advice for obvious reasons. Below, see how to protect yourself from scammers on social media:
- Accept friend requests with caution. Before befriending someone that you do not know, carefully examine the account. There are several things to pay attention to:
- the kind of information the person publishes,
- when the account is registered,
- who accepts their friend requests,
- and how real everything looks.
- Avoid links that request personal data. No social media platform will ask its users to click an outside link to update their personal information. Check with the official customer support if you are unsure. Internet users should apply the principle better safe than sorry.
- Create a unique login and password for each platform. Do not use the same password across all your online accounts. If one account gets compromised – all of them will. It is always better to have unique login details for each platform as well.
- Make sure not to reveal personal info. Do not publish your address, phone number, or place of work on your social media account for your safety. Also, do not reveal this info to strangers in conversations.
- Check whether the account is verified when approached with offers. When you get a strange message, or an offer to buy or sell something on social media, first check if the account is verified. Do not send money to anyone before that.
- Ask yourself why the person is interested in detailed data. Always be cautious if someone shows too much interest in your personal affairs. There is no need to reveal your data to anyone. Even your friends might have been hacked, so be careful.
🤳 Camfecting
There is a type of malware that specifically targets the camera on your device. When your system becomes infected, the operator (the cybercriminal) will view everything recorded. They will also gain access to the camera controls, turning them on and off without the user’s knowledge. This process is referred to as camfecting.

Despite this, many could be asking why to bother worrying about potential hackers seeing you at home. It might seem like a low-priority concern. However, the truth about camfecting is that it is not an easy feat to accomplish. That is to say, the affected person is targeted for a specific purpose.
There are several main reasons why someone’s device might be camfected:
- Stalking.
Cybercriminals that have access to the camera can monitor a person in their most intimate setting. They can learn the user’s routine, especially if a camera has access to geo-location features. It endangers the person physically and psychologically, violating their right to privacy.
- Blackmailing.
Every hack is an opportunity to look for information that can be used against you. Camfecting is another way of gaining access to your details, such as photos and files. Cybercriminals can use these against you in the long run for money extortion.
- Burglary or theft.
Hacking isn’t always the full extent of the crime that a person is willing to commit. Sometimes, criminals will be scoping out a place through webcams to look for valuables. Memorizing your routine and the layout of your home gives these people the data necessary for a break-in.
- Further hacking.
A camera can give its operator access to a lot more than just its immediate surroundings. It is also a way of obtaining passwords and security details. In these cases, cybercriminals will learn everything they can about you to commit identity theft or hijack your financial accounts.
How to Prevent Camfecting
We know what you’re thinking – it is pretty simple to pin a sticker on your camera and be done with it. These days, you can even buy webcam covers that can be easily removed for video calls. However, we want to remind you of two things:
First, the hacker will still have access to the camera’s audio, if not the image.
Second, any device can become camfected, including your phone and tablet. This is why our tips can become essential in protecting yourself against this type of malware.
You can protect yourself against camfecting with our checklist:
- Turn your devices off when you don’t use them. Even the most skilled cybercriminal cannot hack into a device that is off. Make it a habit to turn off the technology that you aren’t actively using. Besides, it will conserve power and is better for the device in the long term.
- Disable camera access for websites & apps. Check your browser and mobile device’s settings. You can turn off camera use for sites and applications under the Privacy tab.
- Monitor whether someone is using your camera. These days, you don’t have to be particularly good with technology to figure these things out. There are plenty of applications that will help you monitor your processes. If you find that a program is using your camera when it doesn’t need to, turn it off or uninstall it.
- Check what programs use your camera. If an app that doesn’t use its features requests access to your camera, don’t trust it. It is best if it is only enabled for a few select applications. This way, cybercriminals will find it harder to exploit any loopholes.
- Keep your software and devices up-to-date. It is especially vital for those apps that regularly have access to your camera features. The developers often release important updates that fix any vulnerabilities that cybercriminals can exploit.
- Install and update antivirus software. It is the surest way of keeping your device clear of any malware. There also exist specialized programs that will monitor for camfecting. Regularly conduct full scans to make sure your device is safe and protected.
📨 File-Sharing Risks
As you can tell by now, sharing information on the Internet can be dangerous. Yet, it is precisely the case when you download and send files. People do not realize how easy it is for a third party to capture them and or access your details. That’s why we will talk about file-sharing risks.
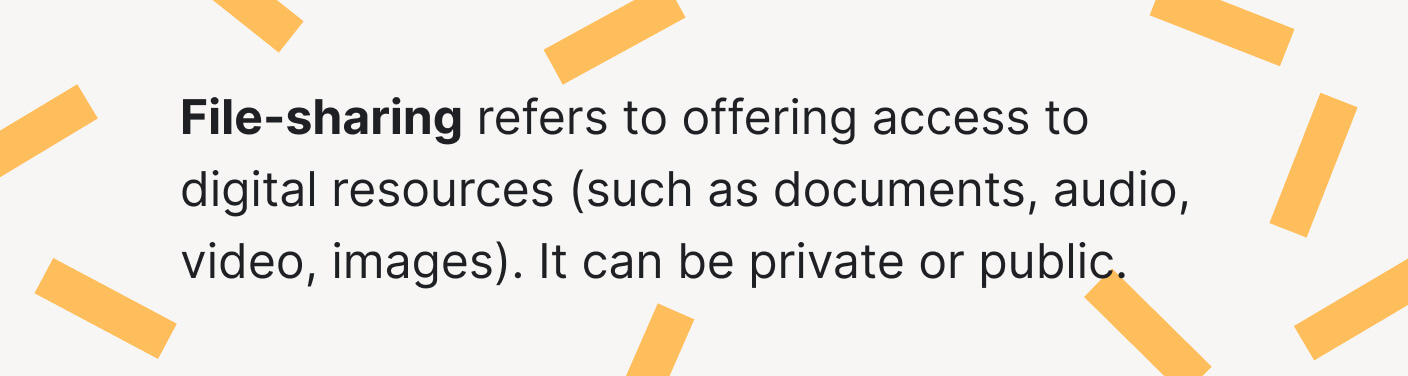
What risks does this technology introduce?
- Hackers can gain access to your sensitive data. When using peer-to-peer (P2P) file-sharing applications, you are opening up your device to unauthorized people. It is impossible to track how many individuals accessed it. Simply by visiting a P2P website, you can be susceptible to various forms of fraud.
- You may participate in criminal activity against your will. Some files on peer-to-peer sharing websites can be pirated. You can download them without knowing that, but it will not save you from fines and legal action. Students are always looking for ways to get free books. However, you can get in trouble with your university and authorities if you download pirated materials.
- Attackers can infect your software with a virus. It is challenging to protect your device on its own, let alone when using a peer-to-peer sharing service. You may download a zipped folder with incorporated Trojan horses, worms, spyware, and viruses.
- You become susceptible to an attack. Inadvertently you become an easy target for attackers because the files you download can include spyware. The infected documents can be named as the materials you are looking for. Unfortunately, you do not have any control over it.
- New files can break your defense system. Some software can open a firewall to allow unauthorized files on your device. You might not even know that attackers are capturing information from your laptop or computer.
How to Prevent File-Sharing Risks
Just like the rest of the cyber threats, students can avoid the dangers of file-sharing. Here, we will tell you how to prevent such risks by doing the following:
- Update your software. The systems that are not up-to-date are easier to hack. This simple action can help you to avoid any unnecessary pains that are connected with hacker attacks.
- Don’t use dubious WiFi. Some students prefer doing their homework in cafes, libraries, and other places with public WiFi. Before sharing any files, make sure the connection you are using is secure.
- Change your passwords regularly. Ideally, you would change your passwords every month. With all the deadlines, homework, and events, it is impossible to remember those dates. So, set up reminders on your phone when the passwords need to be changed.
- Make sure your passwords are strong. Do not use easily guessable passwords. Always include lower and upper case letters, symbols, and numbers. You can also encrypt your files with passwords – it will reduce the risk of cyberattacks.
- Avoid suspicious emails and downloads. The main rule of the Internet is not to download files you do not know. Hackers can put viruses, spyware, and worms to get into your system.
- Don’t click on strange links. If you are not sure what link it is, simply hover over it before clicking. If your gut tells you it is not safe, listen to it.
💡 Pro Tip:
You can try out some secure file-sharing programs. We understand that you have to share files with many people throughout your academic career. For that reason, you need to secure your device, information, and files in the best way possible. These programs can help you:
- Files.com is a cloud-based system with file-sharing features. Simply upload files to the server and send links to people you want to provide access to.
- Dropbox Business allows individuals to share access to files and folders with others. The service has a free plan for private usage.
- WeTransfer Pro is a free file transmission system that has file access tracking built in it. You don’t need an account to send documents.
- G Suite Google Drive lets you store, share, access files from any device. And you get 15GB of free storage.
- OneDrive is free for your first 5GB of data. However, if you want advanced security and 1TB of storage, sign up with Microsoft 365 Personal for $69.99 per year.
💾 Data Theft
Data theft is usually the end goal of every cybercrime. Criminals try to gain access to your information and use it for their benefit. But how do the attackers use your data? Let’s discuss it here!
In this table, we’ve explained why hackers try to gain student’s information:
- Identity theft. Your name, address, social security number, and date of birth are enough to commit identity theft. Sometimes hackers sell such data to other criminals. Credit fraud. Criminals can use your identity to apply for credit cards, file fake tax returns, and take loans in your name.
- Account takeover. Your login details can be used to take over your account. Once the password is changed, you will lose access to it. On shopping websites with payment details, account takeover can lead to losing money as well.
- Blackmailing. It is another way to get the victim to pay. Usually, the hackers with access to sensitive information ask the victim to send them money in exchange for privacy.
- Nuisance marketing. It tends to happen when your data is already sold. In this case, you get emails, text messages, and sometimes phone calls from companies without your prior approval.
How to Prevent Data Theft
You’ve already seen the most critical recommendations in this article. Yet, we should remind you of the need for quality antivirus software and system updates. In this section, we’ve identified where the threat can come from.

For a student, data breach threat can come from the following sources:
- Free WiFi. Numerous college students study in public places while using public WiFi. Identity thieves can set up password catchers and corrupt such free connections. To avoid any theft from your devices, equip them with encryption and the latest software.
- Online purchases. When you buy something online, do not leave your account details. If the company gets hacked, your credit card file will be leaked too.
- Free apps, music, and games. When you download programs for free, remember that hackers can fill them with viruses. Only get your free apps and music from credible sources such as Apple Music or Play Market.
- Phones & Social Media. When you live in a dorm, you should make sure your passwords are not easily guessed. Students who use their social media on university computers must remember to log out.
- Security questions. Put enough thought into choosing and replying to your answers. Do not simply go for the pet’s name and the place of birth. Instead, respond with something that does not make sense. For instance, for “What’s my favorite food?” the answer can be “coffee.” You will not forget it.
- Weak passwords. Students sometimes use the same password for all their devices and accounts. That’s quite dangerous, so create different ones. Change them regularly and make them as strong as you can. The best passwords have small letters, capital letters, symbols, and numbers.
- Dubious celebrity websites. Often, hackers create websites about celebrities filled with viruses and spying software. Such attackers know what students are interested in. The best way to protect yourself is not to go there at all. Find your news on Twitter instead.
🔐 Ultimate Cyber Security Tips for Students
Throughout the previous sections, you have learned numerous tips on keeping your data and devices safe. In the infographic below, we have listed all the essential cyber security recommendations we have for students. With this ultimate collection, you won’t forget what you need for safety.

Thank you for reading the article! We hope that these tips will come in handy in the future. Using them, you will keep both yourself and your data safe. If you’re interested in writing a paper on cyber security, check our free topics and samples. And share this page with all those who could use some cyber security advice.
🔗 References
- 7 Types of Cyber Security Threats – The University of North Dakota
- Types of Cyber Security Threats to College Students – Unigo, EducationDynamics
- How To Recognize and Avoid Phishing Scams – Federal Trade Commission (FTC), Consumer Information
- What Are Cyber Threats and What to Do About Them – The Missing Report, Prey Project
- Malware & Ransomware Cybersecurity – The Ohio State University
- Avoiding Social Engineering and Phishing Attacks – Cybersecurity and Infrastructure Security Agency (CISA), Department of Homeland Security
- Data Security: K-12 and Higher Education – Protecting Student Privacy, U.S. Department of Education
- Camfecting: How Hackers Attack by Gaining Access to Your Webcam – UNSW Newsroom Sydney
- How to Stay Safe When File Sharing Online – NortonLifeLock
- Protect Yourself Against Phishing Scams & Identity Theft – UMass Amherst Information Technology




Great Post. I am continuously searching online for articles that can benefit me. Definitely I bookmarking your website for revisiting. Thank you once again!!
Thank you for the feedback. Your opinion is very important for us!
A most helpful post, to everyone, not only students.
One tip I would add is: if you get a message from a website, for example, your bank or PayPal, stating you need to log in for some reason, don’t follow the link. Log out and then log in directly to their website.
Thank you for your feedback!
Simply just needed to state Now i am happy that i stumbled onto your page
Thanks for the feedback! We look forward to seeing you again!