Introduction
Background Study
A computer network is a system of interconnected computers that allows sharing of resources and information (Banks, 2008). Computer networks comprise of two or hundreds of computers connected together. A network can either be adapt peer- to-peer or client -server connection.
Review of literature
Peer-to-peer network
Peer-to-peer networks are commonly meant for small networks that allow the connected computers to share various resources such as printers, hard disk and CD-ROM. In this type of network, every workstation acts both as a client and a server (DEW Associates Corporation, 2000). Every computer in the network possesses a hard disk where it stores information that can be shared or accessed by any computer in the network. The diagram below shows three computers connected through peer-to-peer.
Peer -to-peer Network
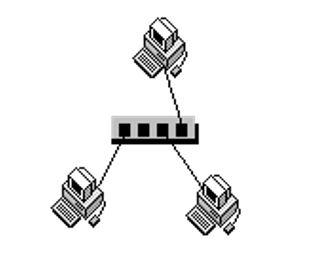
A peer-to-peer network is commonly configured using a coaxial cable and a hub as illustrated above. This network is supported by operating systems such as window 95 and 98. This type of network is cheap and easy to install. Every computer in the network is able to back up its data since all the computers possess a hard disk.
Client –Server Network
A client-server network has one central computer where many files are stored and various operations executed. Such network services as electronic mail and printing utilize a file server router (Lukaszewski, 2010). As a result, clients are not in a position to communicate directly. In case a client intends to send a message to a designated destination, it has to be relayed to a server first. It is the best network that can support a large network with hundreds or thousands of work stations.
Client-Server Network
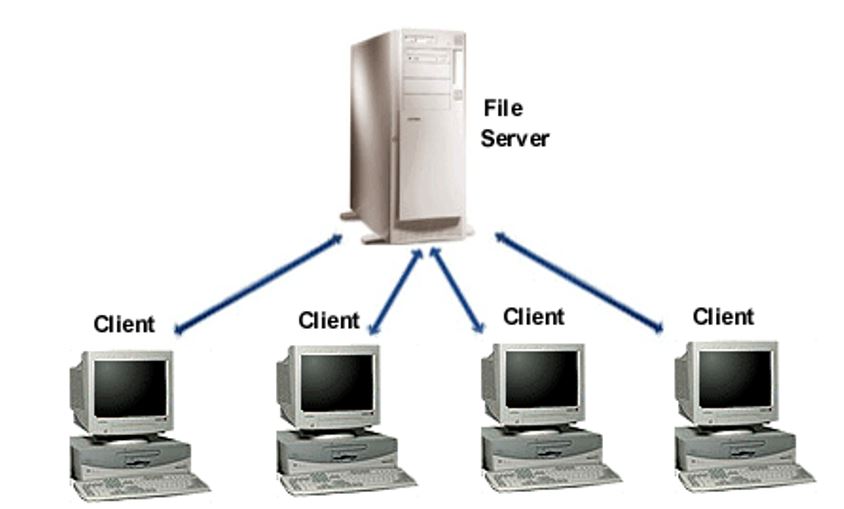
A computer network is made of both hardware and software. Networking hardware are all the physical devices that are required to enable data sharing and execution in a network. Examples of such equipments include;
File server: This is the central computer where all data processing and storage occurs. This computer has very large memory and hard disk. It also possesses a very fast processor and network interface card (Lukaszewski, 2010). This is the place where networks operating software are located. Its main function is to control communications between nodes. A server should have the following specification to perform well.
- A Pentium 4 with a microprocessor of at least 800 megahertz or
- A hard disk with at least 120 gigabytes of storage
- Not less than 512 MB of RAM
- Several expansion slots
- A tape back-up unit
- Fast network interface card
Workstations
These are the computers that are connected in a computer network. Every computer in a network has a network interface card that is configured through the help of networking software. A computer with almost any specification can serve as a workstation bin the network (Pountain, 2001). Network interface card: They act as the physical connection between the workstations and the network. Most of them are purchased together with the computers as they are mostly internal. It is advisable to consider their speed as they highly influence the performance and speed of the network. The widely used card is the Ethernet card, while also Token Ring cards are often used.
Ethernet Cards
This card is purchased separately from a computer. The mackintosh computers contain an alternative that allow their pre-installations. This card supports either a twisted pair or coaxial cables connection. BNC connection supports twisted pair cable, while RJ-45 enables support coaxial cables. Sometimes an Ethernet card possesses an AUI where one can attach a twisted pair, coaxial or fiber optic cable. In such a case, there is an external transceiver that is connected to the nodes.
Ethernet card installed with a RJ-45, AUI, and BNC connectors
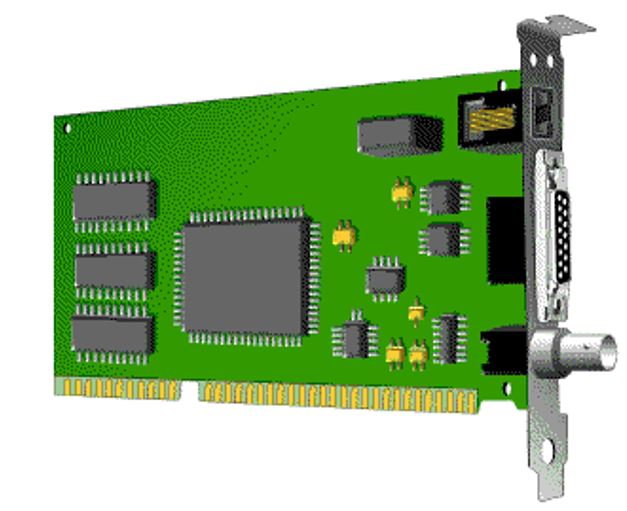
Token Ring Cards
They resemble the Ethernet cards, but are nowadays not very popular since they are being faced out of the market by the Ethernet cards which are faster.
Switches
Switches are configured with 8, 16 or 24 RJ-ports that offer a central connection point for all the computers in the network. They memorize the addresses of all the workstations and the server and thus transmit information directly to the required computer (Lukaszewski, 2010). They are considered to be active and thus, amplify the signals as they relay them.
Repeaters
Repeaters are used to amplify the signal strength in instances where the signal covers a very long distance. They are often incorporated in a switch.
Routers
As good examples of super intelligent devices, routers allows for information translation between networks. A router helps to direct the signal to its destination using the most best available route. This devise is also very instrumental when connecting the network to the internet as it helps to translate the information between the LAN and the internet.
Software
Software is a set of instructions that are programmed to manage hardware in a computers and computer systems. The software that are required in computer networks are operating systems, antivirus and sometimes network monitoring software. The operating systems that can be used include window 95, 98, 2000, xp or Linux. The antivirus can either be single or multi users that support one computer to a maximum of five workstations respectively (Banks, 2008). In big networks corporate antivirus are recommended since they support like 20 or more computers.
Case Study of the LedGrafix design company
This company requires a network with approximately 62 computers. These workstations will be distributed in its various departments to facilitate their communications and sharing of resources and files. The most appropriate network for this company is client-server connection since it is the only one that can support such a big network. The existence of the server will also be very essential as it will control the files that can be shared across the network. On the other hand it will ensure that the sensitive files that should only be accessed by specific users of the network are protected from damage or manipulations. These include files such as those that contain the strategic plans of the organization as well as the company‘s accounting details. All the computers in the network should be installed with antivirus program.
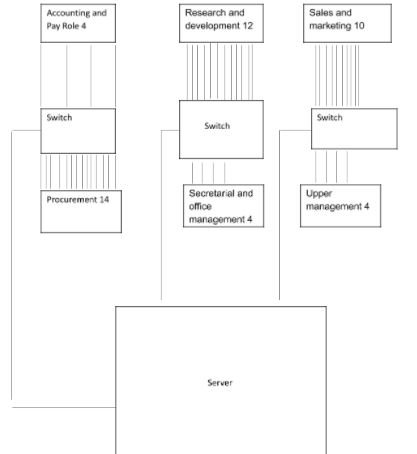
Inventory
Reference List
Banks, M. A. (2008). On the way to the web: the secret history of the internet and its founders. New York: Apress.
DEW Associates Corporation. (2000). Peer-to-Peer versus a client-server. Web.
Lukaszewski, A. (2010) Peer-to-peer Networking. Web.
Pountain, D. (2001). The New Penguin Dictionary of Computing. New York: Penguin Books.